What Is Ssl Cryptography – Getting started with OpenSSL: Cryptography basics
Di: Samuel
The second key in the pair is a private key that is only known ., plaintext) into an encrypted output (i.Cryptography is the use of coding to secure computer networks, online systems, and digital data.
How SSL Works and Why It’s Important
Step 3: Under Startup type, select Automatic and click the Start button to enable it.
What is Secure Socket Layer (SSL)?
Die Informationen können sich im Ruhezustand (z.

TLS the short form of Transport Layer Security, which is a cryptographic protocol that provides secure communication over a computer network.Cryptography is the mathematical foundation on which one builds secure systems. SSL technology, created by Netscape, establishes a secure connection between a Web server and a browser, ensuring private and secure data transmission.Step 1: In the Start menu search bar, type services. There are three types of cryptography: Symmetric-key cryptography – Both sender and receiver share a single key and the sender uses this key to encrypt plaintext . In this course you will learn the inner workings of cryptographic systems and how to correctly use them in real-world applications. It studies ways of securely storing, transmitting, and processing information. Step 2: The list of services will be displayed.
What is SSL, TLS and HTTPS?
Das Wort ist eine Mischung aus zwei griechischen Wörtern: „kryptós“, was verborgen .Asymmetric key cryptography, also known as public-key cryptography, is an approach in which all individuals possess a key that is openly shared and a private key that remains confidential. Companies and organizations need to add SSL certificates to their websites to secure online .
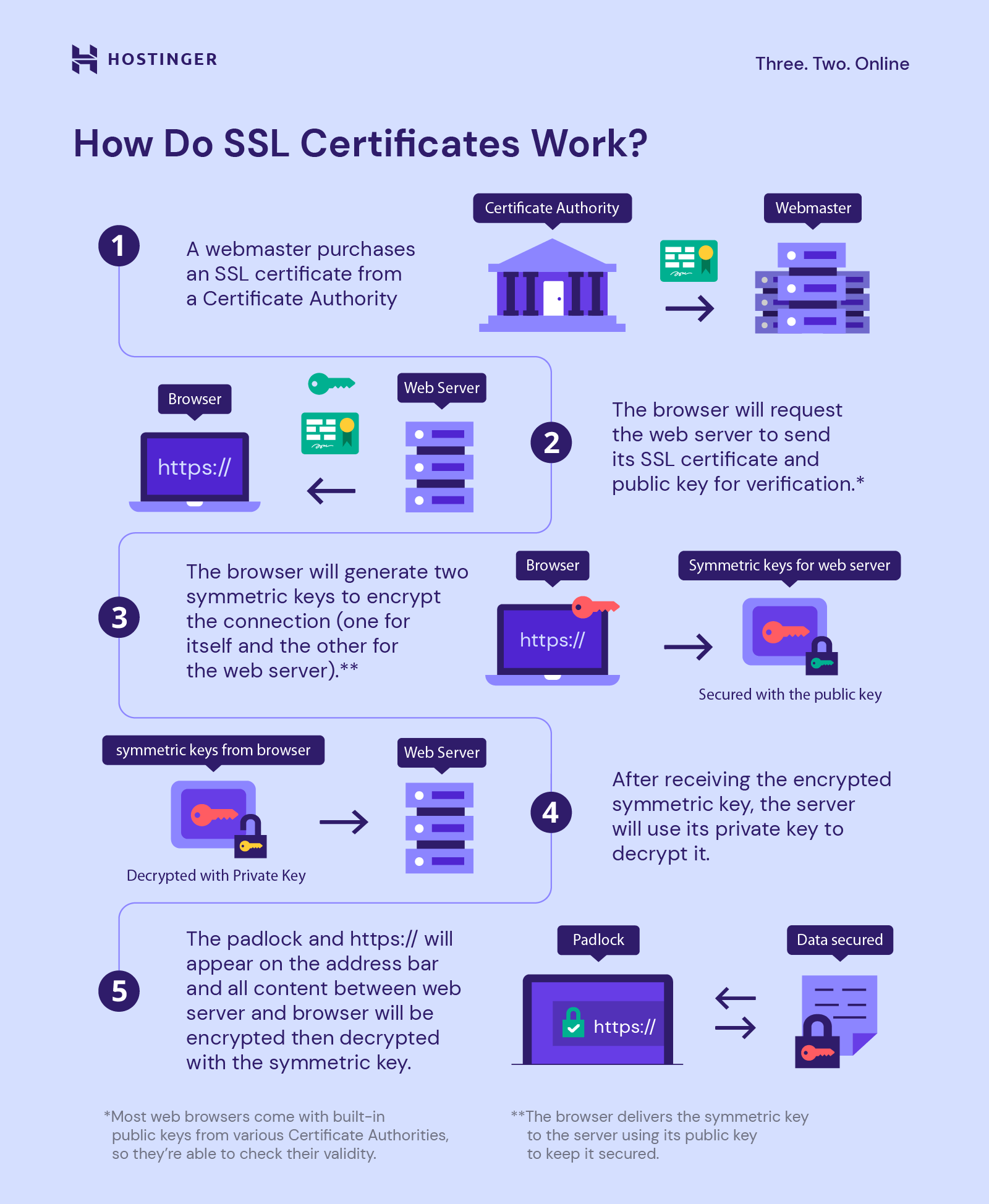
The sender’s message is typically known as the . The public key, included in the certificate, allows a web browser to initiate an encrypted communication session with a web server via the TLS . Like a physical key, it locks (encrypts) data so that only someone with the right key can unlock (decrypt) it. It is the study of communications and a form of security for messaging. Here’s a bit of the history of SSL and TLS: SSL version 1.Another key benefit is authentication.Image by: Opensource. Miller—Elliptic Curve Cryptography uses a different formulaic approach to encryption.
Kryptographie
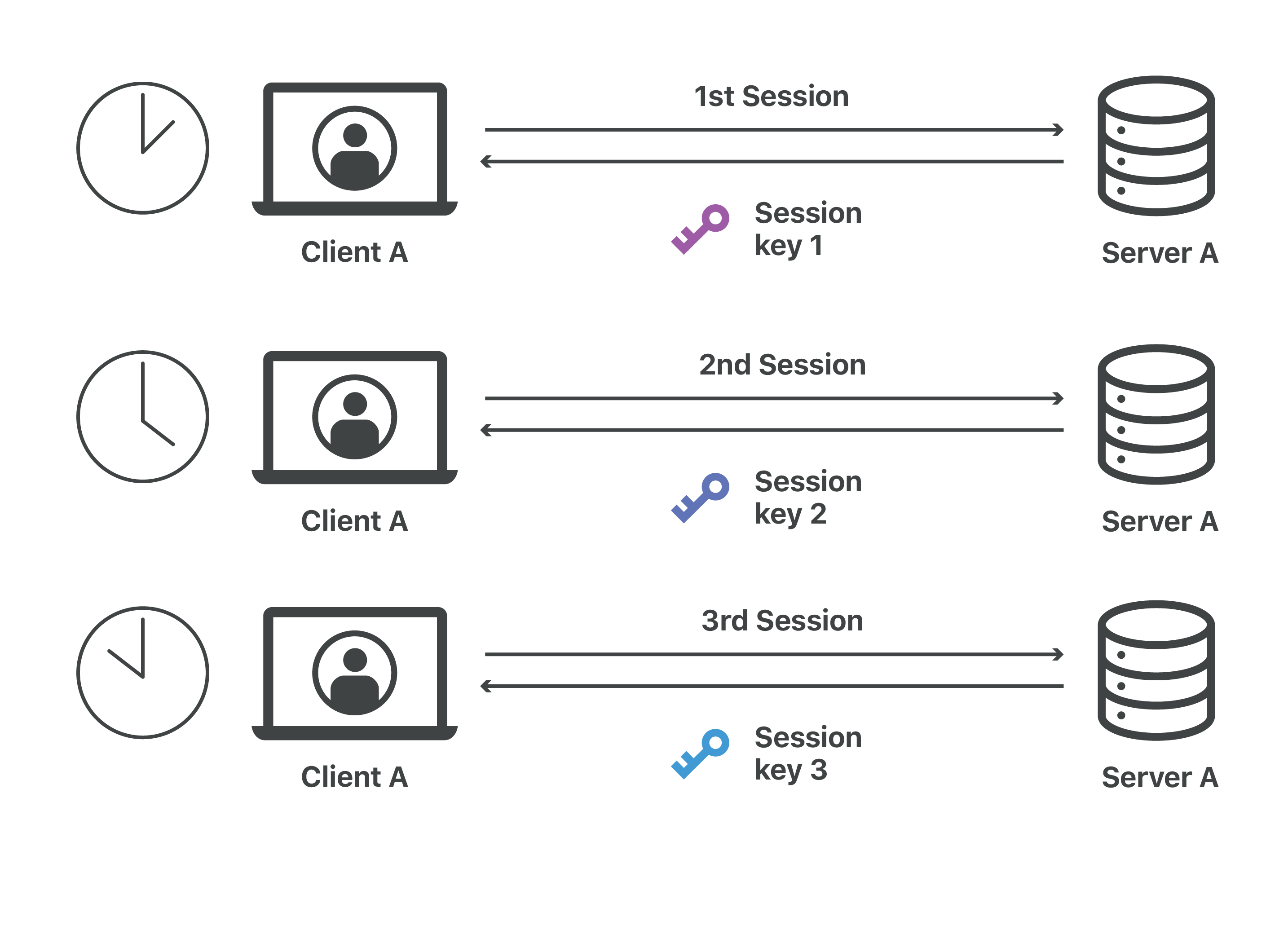
Introduction to Cryptography 3/53. From digital signatures to disk encryption, these everyday applications of cryptography enable users of the Internet, developers, and business to keep sensitive data private. The protocol is designed to support a range of choices for specific algorithms used for cryptography, digests and signatures.Elliptic curve cryptography (ECC) uses the mathematical properties of elliptic curves to produce public key cryptographic systems. While the term tends to be associated with the modern digital era, the concept has played a significant role for centuries .Cryptography is an indispensable tool for protecting information in computer systems.Transport Layer Security, or TLS, is a widely adopted security protocol designed to facilitate privacy and data security for communications over the Internet. The sender leverages a specific type of key and algorithm for encryption of a message before sending it to the receiver. It provides less latency. TLS (Transport Layer Security) provides high security. Anything encrypted with the public key can only be decrypted by the corresponding private key. Like all public-key cryptography, ECC is based on mathematical functions that are simple to compute in one direction, but very difficult to reverse. HTTPS is encrypted in order to increase security of data transfer.An SSL certificate is a digital certificate that authenticates a website’s identity and enables an encrypted connection.Kryptographie ist die Praxis des Schutzes von Informationen durch die Verwendung von verschlüsselten Algorithmen, Hashes und Signaturen.SSL: Secure Sockets Layer. In TLS (historically known as SSL), the two communicating parties (the client and the server) generate session keys at the start of any communication session, during the TLS handshake. The project’s technical decision making is managed by the OpenSSL Technical Committee (OTC) and the project governance is . Without an SSL certificate, a website’s traffic can’t be encrypted with TLS. During a TLS handshake, the client and server agree upon new keys to use for symmetric encryption, called session keys. Cryptographic systems are generically classified (1) by the mathematical operations through which the .Quantum cryptography (also known as quantum encryption) refers to various cybersecurity methods for encrypting and transmitting secure data based on the naturally occurring and immutable laws of quantum mechanics.

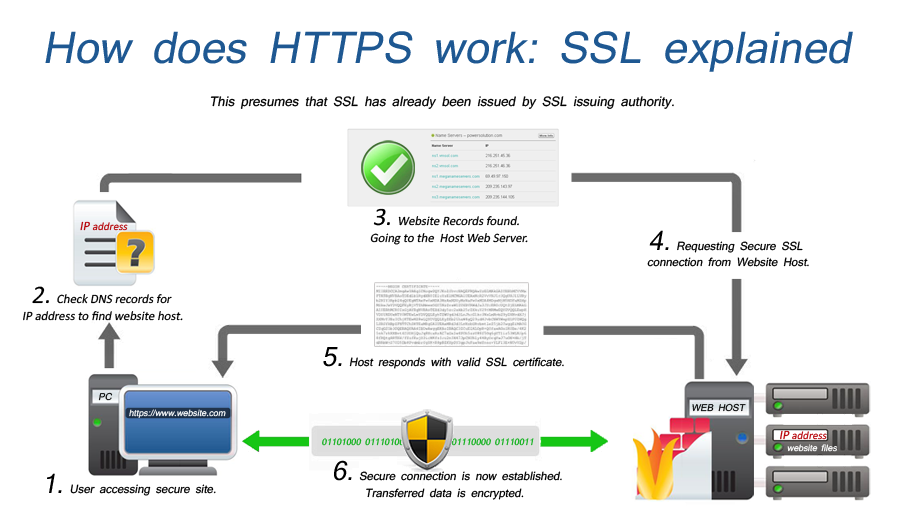
The RSA algorithm is as follows: Choose p, q, two prime numbers. Understanding what cryptographic primitives can do, and how they can be composed together, is necessary to build secure systems, but not su cient. TLS is still widely used. This key pair – public and private keys – are uniquely related. Um diese sichere Verbindung herzustellen, benötigen Browser und Server ein TLS/SSL-Zertifikat. The information can be at rest (such as a file on a hard drive), in transit (such as electronic .Socket Security Layer (SSL) Architecture.TLS, historically known as SSL, is a protocol for encrypting communications over a network.
What is an SSL Certificate & Why is it important?
Calculate n = pq.
A complete overview of SSL/TLS and its cryptographic system
It supports Python 3.The key allows the user to decrypt the message, thus ensuring on they can read the message.) OpenSSL utilities are available at the command line, and programs can call functions from the OpenSSL . Secure Sockets Layer (SSL) is a standard technique for transmitting documents securely across a network. Devices attempting to communicate with the origin server will reference this file to obtain the public key and verify the .Cryptography is the study and practice of sending secure, encrypted messages between two or more parties.
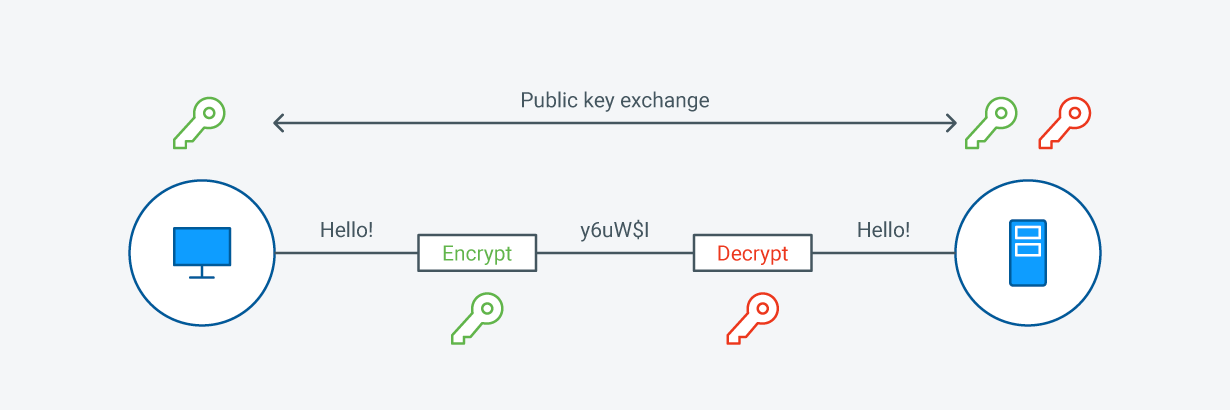
What is asymmetric encryption?
Cryptography is used to keep messages and data secure from being accessible to anyone other than the sender and the intended recipient. While still in its early stages, quantum encryption has the potential to be far more secure than previous types of cryptographic . Mehr dazu erfahren Sie auf dieser FAQ .
Was ist SSL-Kryptografie?
The official RFC for TLS does not actually call these keys session keys, but . That is, it helps to prevent malicious actors from falsely impersonating a site. Cryptography allows digital currency transactions to be pseudonymous, secure, and “trustless” – with no bank or other intermediary required.Cryptography is a cornerstone of modern secure communication practices.The server uses its private key to decrypt the secret key sent by the client.
Public Key and Private Key Explained
Encryption uses an algorithm and a key to transform an input (i.A cryptographic algorithm is the mathematical equation used to scramble the plain text and make it unreadable. eine Datei auf einer Festplatte), in der Übertragung (z. A popular alternative, first proposed in 1985 by two researchers working independently—Neal Koblitz and Victor S. It can also be used to authenticate users.Cryptology – Encryption, Ciphers, Security: Cryptography, as defined in the introduction to this article, is the science of transforming information into a form that is impossible or infeasible to duplicate or undo without knowledge of a secret key. The strength of the randomness of an . SSL is standard technology for securing an internet connection by encrypting data sent between a website and a browser (or between two servers).cryptography is a package which provides cryptographic recipes and primitives to Python developers. The “crypto” in the word “cryptocurrency” means “secret” in Greek – which gives . Several additional considerations go . TLS is highly reliable and upgraded. It prevents hackers from seeing or stealing any information transferred, including personal or financial data. It is a concept whose endgame is to keep vital information that is subject to potential data breaches safe and confidential. It’s simply a data file containing the public key and the identity of the website owner, along with other information.Transport Layer Security (TLS), auch bekannt unter der Bezeichnung des Vorgängerprotokolls Secure Sockets Layer (SSL), ist ein Standardprotokoll für die sichere Übertragung sensibler Daten. The program sends back data that has been signed, encrypted, and compressed (optional). TLS uses both asymmetric encryption and symmetric encryption.Welcome to OpenSSL! The OpenSSL Project develops and maintains the OpenSSL software – a robust, commercial-grade, full-featured toolkit for general-purpose cryptography and secure communication.Historically, cryptography was used for confidentiality: keeping messages secret Encryption goes back thousands of years Today, we do much more, including authentication, integrity-checking, “signing” documents, playing games of chance over the Internet, cryptocurrencies like Bitcoin, etc. Once the secret key is decrypted, both the server and the client have a shared secret key. They are used for data encryption, authentication and digital signatures. Encryption algorithms take the original message, or plaintext, and converts it into ciphertext, which is not understandable. Calculate f (n) . A working SSL/TLS connection ensures that data is being sent to and received from the correct server, rather than a malicious “man in the middle.0 was never publicly released because of some serious security flaws.Cryptography increasing relies on mathematical concepts — a set of encryption algorithms and hashing algorithms — to transform information in a way that is difficult to interpret or “crack”. Die Kryptografie ist eine Technik zur Verschleierung oder Verschlüsselung von Daten, die sicherstellt, dass nur die Person, die die Informationen sehen soll und den Schlüssel zum Brechen des Codes hat, sie lesen kann. SSL communicates using the Transport Control .
How does SSL work?
SSL has been depreciated. The two primary types of cryptography are symmetric key cryptography and asymmetric key cryptography and .The Rivest-Shamir-Adleman (RSA) algorithm is the most widely accepted approach in asymmetric cryptography. The course begins with a detailed discussion of how two parties who have a shared secret key can communicate securely when a powerful . Any application-layer protocol can send data via SSL in most cases; however, HTTP is the most used one. SHA is a modified version of MD5 and used for hashing data and certificates.Kryptografie (altgriechisch κρυπτός kryptós, deutsch ‚verborgen‘, ‚geheim‘ und γράφειν gráphein, deutsch ‚schreiben‘) ist ursprünglich die Wissenschaft der Verschlüsselung von Informationen.Basically, cryptography serves as a technique for the transmission of secure messages among two or more participants.Cryptography is the practice of protecting information through the use of coded algorithms, hashes, and signatures.An SSL certificate (also known as a TLS or SSL/TLS certificate) is a digital document that binds the identity of a website to a cryptographic key pair consisting of a public key and a private key.
What is Elliptic curve cryptography (ECC)?
What is Cryptography?
The word cryptography is derived from the Greek words kryptos, meaning hidden, and graphein, to write. A given algorithm will always transform the same plaintext into the same ciphertext if the same key is used. In order to facilitate your understanding, this article will start with the basics of cryptography, and then move on to a detailed explanation of the SSL protocol principles, processes and some important features, and . Cryptography is the study of securing communications from outside observers.SSL (Secure Socket Layer) is less secured as compared to TLS (Transport Layer Security). Heute befasst sie sich auch allgemein mit dem Thema Informationssicherheit, also der Konzeption, Definition und Konstruktion von .Secure Sockets Layer.Cryptography i s a technique of securing communication by converting plain text into unintelligible ciphertext.Hypertext transfer protocol secure (HTTPS) is the secure version of HTTP, which is the primary protocol used to send data between a web browser and a website.
This article is the first of two on cryptography basics using OpenSSL, a production-grade library and toolkit popular on Linux and other systems. Rather than physically hiding a message from enemy .
Cryptography Tutorial
SSL is less reliable and slower. cryptography includes both high level recipes and low level interfaces to common cryptographic algorithms such as symmetric ciphers, .
What Is Quantum Cryptography?
SHA stands for secure hashing algorithm.SSL provides for secure communication between client and server by allowing mutual authentication, the use of digital signatures for integrity and encryption for privacy. Ultimately, cryptography can keep data from being altered or stolen. In order to secure and compress data produced at the application layer, SSL was created. msc and press the Enter key.
Technically, any website owner can create their own SSL certificate, and such . This guide provides an overview of what cryptography is, a brief history of cryptography, . The public key is employed to secure or encode information, while the private key, exclusively held by the individual, is required to unlock or decode it.Kryptographie bzw.SSL protocol is an important part of modern network communication, which provides data security at the transport layer. For example, suppose communication between two parties is secured using cryptographic principles. The third core benefit of SSL/TLS is data integrity. A hashing algorithm shortens the input data into a smaller form that cannot be understood by using bitwise operations, modular additions, and compression functions. Right-click the Cryptographic Services and select Properties.An SSL certificate is a file installed on a website’s origin server. It involves various algorithms and protocols to ensure data confidentiality, integrity, authentication, and non-repudiation. A primary use case of TLS is encrypting the communication between web applications and servers, such as web browsers loading a website.
Getting started with OpenSSL: Cryptography basics
RSA is currently the industry standard for public-key cryptography and is used in the majority of TLS/SSL certificates.
What Is Cryptography? Definition & How It Works
Then, the receiver employs decryption for obtaining the original message. (To install the most recent version of OpenSSL, see here .A session key is like a password that someone resets every time they log in. SSL stands for Secure Sockets Layer, a security protocol that creates an encrypted link between a web server and a web browser.Symmetric Cryptography. While RSA is based on .
What is an SSL certificate?
One key in the pair is a public key which can, as the name suggests, be distributed widely without impacting security.
Cryptography
Each new communication session will start with a new TLS handshake and .
SSL certificates make SSL/TLS encryption possible, and they contain the website’s public key and the website’s identity, along with related information. Asymmetric cryptography means that one key is used to encrypt and a different, but related one is used to decrypting the message.Public-Key Cryptography, which is also known as asymmetric cryptography, is a system that uses pairs of keys to encrypt and authenticate information.Die Definition der Kryptographie. The original data is known as the plaintext, and the data after the key encrypts it is known as the . In theory, only an individual with a unique cryptographic key should be able to .Historic methods of secret-keeping. This is particularly important when users transmit sensitive data, such as by logging into a bank account, email service . Protect your online presence with a trusted SSL certificate.In cryptography, a key is a string of characters used within an encryption algorithm for altering data so that it appears random.Cryptography provides for secure communication in the presence of malicious third-parties—known as adversaries.An SSL certificate is a data file hosted in a website’s origin server. Also called “secret key cryptography,” symmetric cryptography functions via cryptographic key sharing between users.7+ and PyPy3 7. Our goal is for it to be your “cryptographic standard library”. In this method, the same key is used to encrypt and decrypt data and is typically shared between users. The history of SSL/TLS. bei elektronischer Kommunikation zwischen zwei oder mehreren Parteien) oder in . TLS can also be used to encrypt other . In the case of ECC, this difficulty resides in the .

- What Is Matlab Toolbox : System Identification Toolbox
- What Is The Best Vin Lookup Tool?
- What Is The Difference Between Git Fetch –All And Git Pull
- What Is Robinson Club Janda Playa?
- What Is The Difference Between Gad And Situational Anxiety?
- What Is Nvidia Geforce Experience?
- What Is Majora’S Mask In The Legend Of Zelda?
- What Is The Difference Between Vim Improved
- What Is The Highest Grossing Foreign Film In India?
- What Is The Entrance Location Of The Iron Horde Raid?
- What Is System Mechanic Pro? – Update System Mechanic