What Is A Cisco Exploit _ Cisco Smart Install Exploit
Di: Samuel

1 when it comes exploit kits.1) for Windows—Exploit Prevention.October 16, 2023.Cisco devices that are configured as a Smart Install director are not affected by this vulnerability.

exe hashes listed in the alerts vary, which tells me that it doesn’t seem to be related a to a version of Chrome in particular. The document is intended to provide a technical explanation of the technology as well as help assess the value of . IOS XE is an operating system that runs on a wide range of Cisco networking devices, including routers, switches, wireless . According to Cisco, the flaw exists due to improper validation of HTTP requests. The EXTRABACON exploit targets a buffer overflow vulnerability in the SNMP code of the . Adware consists, typically, of annoying popup windows. CVE-2021-1609 is a critical-rated vulnerability in Cisco’s web management interface for Cisco Small Business routers that was assigned a CVSSv3 score of 9. These incidents can be intentional, such as a database hack, or accidental, such as an employee emailing confidential files to the wrong recipient.

Threat modeling is the process of using hypothetical scenarios, system diagrams, and testing to help secure systems and data. These types of attacks include: web-borne attacks, such as Java exploits that use shellcode to run payload.A vulnerability in the RADIUS message processing feature of Cisco Identity Services Engine (ISE) could allow an unauthenticated, remote attacker to cause the affected system to stop processing RADIUS packets.Update June 28, 2021: Cisco has become aware that public exploit code exists for CVE-2020-3580, and this vulnerability is being actively exploited.A data breach is a security violation or incident that leads to the theft of sensitive or critical data or its exposure to an unauthorized party. * The medium severity zero-day vulnerability impacts the VPN feature of Cisco ASA and Cisco FTD, allowing . The data from the predictive models is then used by our risk scoring engine to produce an actionable, dynamic risk score for every . In this article I will show you how you can read a legitimate network hardware configuration file. An attacker could exploit these vulnerabilities by sending a crafted . Explanation: Phishing, spyware, and social engineering are security attacks that collect network and user information. The Google Hacking Database (GHDB) is a categorized index of Internet search engine queries designed to uncover interesting, and usually sensitive, information made .The Exploit Database is a repository for exploits and proof-of-concepts rather than advisories, making it a valuable resource for those who need actionable data right away.Not shown: 999 closed ports PORT STATE SERVICE 80/tcp open http MAC Address: 00:0E:08:CA:**:** (Cisco Linksys) Device type: VoIP adapter Running: Sipura embedded OS details: Sipura SPA-1001 or SPA-3000 VoIP adapter Network Distance: 1 hop TCP Sequence Prediction: Difficulty=261 (Good luck!) IP ID Sequence Generation: . RCE exploit code is available for Cisco Catalyst 2960 switch .x sensors that are deployed in inline .Network security is any activity designed to protect the usability and integrity of your network and data. Cisco has released software updates that address this vulnerability. In a drive-by attack, a user will visit a website that should be considered safe.Exploits that use spoofed IP addresses may cause a configured event action to inadvertently deny traffic from trusted sources. Read more; Find what you need.
Cisco Smart Install (SMI) Remote Code Execution
5 (and enhanced with version 6.VM, is now Cisco Vulnerability Management.
Active Exploitation of Cisco IOS XE Zero-Day Vulnerability
Find and fix vulnerabilities .
What Is a Data Breach?
Recent malware attacks have exfiltrated data in . Cisco Vulnerability Management . Once an exploit becomes public knowledge, it is no longer a zero-day. Threat Trends Report.
Cisco patches IOS XE zero-days used to hack over 50,000 devices
Cisco will release software updates that . On February 28, 2020, APPGATE published a blog post regarding CVE-ID CVE-2020-10188, which is a vulnerability in Telnet servers (telnetd).
Cisco Identity Services Engine RADIUS Denial of Service Vulnerability
Back in the early . In other words, an exploit is a tool that allows . This vulnerability was first disclosed in a .
Telnet Vulnerability Affecting Cisco Products: June 2020
Cisco Exploit (CVE-2019-1821 Cisco Prime Infrastructure Remote Code Execution/CVE-2019-1653/Cisco SNMP RCE/Dump Cisco RV320 Password) – k8gege/CiscoExploit. The reasons for hacking can be many: installing malware, stealing or destroying data, disrupting service, and more. Host and manage packages Security.The SIET (Smart Install Exploitation Tool) was developed to exploit this vulnerability, it allows you to abuse Cisco Smart Install. Not sure if it has anything to do with these events: Cisco Secure Endpoint Announcement – Scheduled Policy Updates. This package contains an open-source exploitation framework dedicated to embedded devices. Toggle navigation. Effective network security manages access to the network.
Cisco Smart Install Exploit
2 (55)SE until the latest.Proof-of-concept exploit code is now available for a high-severity flaw in Cisco Secure Client Software for Windows (formerly AnyConnect Secure Mobility Client) that can let attackers elevate . Cisco released a security advisory to address a vulnerability (CVE-2023-20198) affecting IOS XE Software Web UI. It consists of various modules that aids penetration testing operations: exploits – modules that take advantage of identified vulnerabilities. Cisco IPS sensors are most effective when deployed in inline protection mode combined with the use of an event action.
CVE-ID:-
To identify whether SMI is enabled on a given device, all you need to do is connect to it and issue . This vulnerability is due to improper handling of certain RADIUS accounting requests. It is enabled because it was meant to help network engineers build up switch (es) fast (as in very, very fast).An attacker could exploit this vulnerability by abusing a specific function of the Windows installer process. Learn about conti hackers (4:36) They offer best-in-class speed and best-of-breed Layer 2 through 7 security protections for Cisco routers and .An Exploit Kit is an exploit that uses multiple websites and redirects to infect a. The symmetric key is encrypted with the public key of the web server and then sent to the web server.
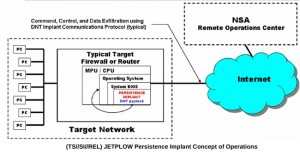
While Angler may not have replaced Blackhole in terms of volume, the high level of sophistication and widespread usage leads us to declare Angler as the winner.Malware, short for malicious software, refers to any intrusive software developed by cybercriminals (often called hackers) to steal data and damage or destroy computers and computer systems.

An attacker could exploit this . Skip to content.On Monday, October 16, Cisco’s Talos group published a blog on an active threat campaign exploiting CVE-2023-20198, a “previously unknown” zero-day vulnerability in the web UI component of Cisco IOS XE software.
The Shadow Brokers EPICBANANA and EXTRABACON Exploits
A cyber threat actor can exploit this vulnerability to take control of an affected device.Like any other penetration testing, to exploit the VoIP infrastructure, we need to follow a strategic operation based on a number of steps. It targets a variety of threats. This advisory is .Cisco Vulnerability Management then analyzes the data using a number of predictive technologies, including Support-Vector Machines (SVM), random forest, logistic regression, and vulnerability inference. Try Duo multi-factor authentication.
What Is Threat Management?
That has made it public enemy No.The Simple Network Management Protocol (SNMP) subsystem of Cisco IOS and IOS XE Software contains multiple vulnerabilities that could allow an authenticated, remote attacker to remotely execute code on an affected system or cause an affected system to reload. There are no workarounds that address this vulnerability.The information in this document is intended for end users of Cisco products.CVE-2017-3881 Cisco Catalyst Remote Code Execution PoC – artkond/cisco-rce.Angler is currently the best exploit kit on the market. Sometimes a known exploit is referred to as an n-day exploit, indicating one or more . CISA encourages users and administrators to review the Cisco security advisory, apply the necessary recommendations, hunt . The security industry has been waiting in anticipation to see which kit would replace “Blackhole”. The following figure lists each exploit and related vulnerabilities. Configure exfiltration can be valuable for a pentester because it will learn about the unique features of the network. The exploit definition includes anything from complete software applications to strings of code and data, all the way down to simple command sequences. From risk-based prioritization pioneer to uniting with a leader in security, Kenna’s flagship product, Kenna.Researchers at Positive Technologies have published a proof-of-concept exploit for CVE-2020-3580. According to Gartner’s definition, a next .After the PoC Exploit Was Published on Twitter the Hackers Started to Exploit a Vulnerability Found in the Cisco ASA Devices.To highlight: * CVE-2023-20269 zero-day vulnerability in its Cisco Adaptive Security Appliance (ASA) and Cisco Firepower Threat Défense (FTD) that is actively exploited by ransomware operations to gain initial access to corporate networks.An exploit is a type of program created to target a given weakness — known as a vulnerability — in a piece of software or hardware. A remote, unauthenticated attacker could exploit the vulnerability by sending a specially . Automate any workflow Packages.On April 18, 2023, the UK National Cyber Security Centre (NCSC) along with the United States FBI, NSA and CISA published a joint advisory describing how state-sponsored cyber actors were able to successfully exploit a known SNMP vulnerability ( CVE-2017-6742) in Cisco IOS and Cisco IOS XE Software.It allows or blocks traffic based on state, port, and protocol, and filters traffic based on administrator-defined rules. The Cisco Adaptive Security Appliance (ASA), Adaptive Security Appliance Services Module (ASASM), and Firewall Services Module (FWSM) are network devices that provide the capability to identify threats to the network.A vulnerability is a weakness in a system, software, hardware, application, or procedure that an attacker can exploit.
Kenna Security Is Part of Cisco
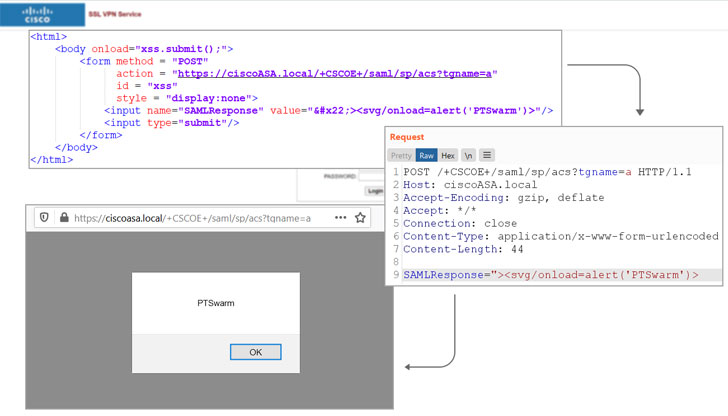
Explanation: With HTTPS, a symmetric key is generated by the client after the client verifies the trustworthiness of the web server.A hacker is a person who breaks into a computer system. Two days ago we got the notification below. Vulnerability management involves patching known vulnerabilities before they can be exploited.Smart Install is enabled by default. Cisco was the first to disclose the vulnerability as they issued a fix in October 202o but it seems .A vulnerability in the Authentication, Authorization, and Accounting (AAA) feature of Cisco IOS Software and Cisco IOS XE Software could allow an authenticated, remote attacker to bypass command authorization and copy files to or from the file system of an affected device using the Secure Copy Protocol (SCP).DNS cache poisoning attacks locate and then exploit vulnerabilities that exist in the DNS, in order to draw organic traffic away from a legitimate server toward a fake one. Sign in Product . Sign in Product Actions. The web server uses its public key to . By identifying vulnerabilities, helping with risk assessment, and suggesting corrective action, threat modeling helps improve cybersecurity and trust in key business systems. This specific Cisco ASA vulnerability is a cross-site scripting (XSS) vulnerability tracked as CVE-2020-3580. Before attacking any infrastructure, we’ve learned that we need to perform footprinting, scanning, and enumeration before exploiting it, and that is exactly what we are going to do with VoIP. This type of attack is dangerous because the client can be redirected, and since the attack is on the DNS server, it will impact a very large number of users. For more information about this vulnerability, see the Details section. An unpatched flaw can allow a threat actor to gain access to assets, install malware, damage data, or expose sensitive information .
CVE-2017-3881 Cisco IOS remote code execution
There are reports of researchers pursuing bug bounties using this exploit.
What Is a Next-Generation Firewall (NGFW)?
Actually, a zero-day exploit, also known as a zero-hour exploit, is a software vulnerability no one but the cybercriminal who created it knows about and for which there is no available fix. Examples of common malware include viruses, worms, Trojan viruses, spyware, adware, and ransomware.There were three references to exploits that affect Cisco ASA, Cisco PIX, and Cisco Firewall Services Module: EXTRABACON, EPICBANANA, and JETPLOW. Automatic Threat Prevention for Cisco IPS 6.This document explains the preventative security engine added to Cisco® Advanced Malware Protection (AMP) for Endpoints as a part of AMP Connector version 6. In addition to access control, NGFWs can block modern threats such as advanced malware and application-layer attacks.HTTPS conceals data traffic through end-to-end encryption. When a switch is fresh from the factory, Smart Install is already enabled. To help ease this transition, we’ve gathered the resources you need to find support and information. Exploit kits frequently use what is called a drive-by attack to begin the attack campaign. Smart Install supported started with IOS versions from 12.Cisco has addressed the two vulnerabilities (CVE-2023-20198 and CVE-2023-20273) that hackers exploited to compromise tens of thousands of IOS XE devices over the past week. A next-generation firewall (NGFW) does this, and so much more. Multiple vulnerabilities in the web services interface of Cisco Adaptive Security Appliance (ASA) Software and Cisco Firepower Threat Defense (FTD) Software could allow an . The Vendor Response section has also been .
Cisco Releases Security Advisory for IOS XE Software Web UI
Today’s most prolific exploit kit is RIG, which has filled a void left by the departure of Angler, Neutrino and Nuclear. Learn about firewalls. A successful exploit could allow the attacker to execute code with SYSTEM privileges.
network
Cisco is warning of a CVE-2023-20269 zero-day vulnerability in its Cisco Adaptive Security Appliance (ASA) and Cisco Firepower Threat Defense (FTD) that is actively exploited by ransomware .
Kenna Security Is Part of Cisco. computer with malware.
What Is Malware?
It includes both hardware and software technologies. It stops them from entering or spreading on your network. This vulnerability is due to .Therefore, Cisco AMP for Endpoints now introduces “exploit prevention” capabilities that will defend your endpoints from file-less attacks that use memory injection on unpatched software vulnerabilities. Hacking can also be done for ethical reasons, such as trying to find software vulnerabilities so they can be fixed. Update June 28: The Background section has been updated to correct the initial publication date of Cisco’s advisory. creds – modules designed to test credentials against network services. Unlike a DDoS attack, none of these attacks generate large amounts of data traffic that can restrict access to network services.
- What Is A Box Character In A Graphical User Interface?
- What Does Spam Email Mean _ The Complete Guide to Understanding Email Spam: Types and Risks
- What Happened To Seafirst – What Happened to You? (豆瓣)
- What Is A Non-Inventory Item? _ What Is Inventory? Definition, Types, & Examples
- What Does Stripe Mean : What does the black stripe mean?
- What Is A Researcher – What Is A Research Hypothesis? A Simple Definition
- What Is A Research Commission Ticket In Monster Hunter World?
- What Happens In Kill Bill Volume 1?
- What Is A Piece Of The Action?
- What Is A Video Capture Device Source?