Was Ist Discretionary Access Control
Di: Samuel
Here, an ACE mentions users or groups that are permitted or denied access to a secure object. When a user tries to access a resource, the system automatically checks . FreeBSD supports security extensions based on the POSIX®.
(In capability-based systems, there is usually no explicit concept of ‚owner‘, but the creator of an object has a similar degree of control over its access policy.Discretionary access control (DAC) is a paradigm of controlling accesses to resources. The owner can assign permissions to other users or groups, enabling them to read, write, execute, or modify . DAC in the Workplace. Discretionary access .) Mandatory access control. Sumber daya ini bisa bersifat fisik, seperti ruangan atau gedung, maupun logis, seperti data atau jaringan komputer.Because secret S has been encrypted by access user’s public key, unauthorized user(s) cannot decrypt it, thus achieving strong discretionary access control.Discretionary access controls are therefore based on authorizations that state who can exercise given accesses. Access under RBAC is based on a user’s job function within the organization to which the computer system belongs. On Trusted AIX systems, however, the use of privileges and other access controls significantly reduces this security risk. This means that users can set specific access levels and permissions, such as read, write, or delete, for . For example, you could be working on a .Discretionary access control systems allow users to establish or change these permissions on files they create or otherwise have ownership of.
What is access control? A key component of data security
When working with cloud-based documents, such as Google Docs or Microsoft Office 365, you have the power to control who can access your files. Eine Access Control List (kurz ACL, englisch für Zugriffssteuerungsliste, kurz ZSL) ist eine Software-Technik, mit der Betriebssysteme und Anwendungsprogramme Zugriffe auf Daten und Funktionen eingrenzen können. These security mechanisms include file system Access Control Lists ( “Access Control Lists”) and Mandatory Access Control (MAC).
Discretionary Access Control
An access control list (ACL) is a list of access control entries (ACE). DAC mechanisms will be controlled by user identification such as username and password. This paper argues that reliance on DAC as the principal method of access control is unfounded and inappropriate for many commercial and civilian government organizations. According to the trusted computer system evaluation criteria (TCSEC) (often referred to as the Orange Book)[], discretionary access control is “a means of restricting access to objects based on the identity of subjects and/or groups to which they belong.

discretionary access control (DAC) An access control policy that is enforced over all subjects and objects in an information system where the policy specifies that a subject that has been granted access to information can do one or more of the following: (i) pass the information to other subjects or objects; (ii) grant its privileges to other . Zugriffsschutzstrategie vom Benutzer bestimmt.Discretionary access control (DAC) With DAC models, the data owner decides on access.Alternatives to PBAC.Muster einer ACL. System ACL (SACL) The system access control list (SACL) is more about monitoring who is accessing a secured object than controlling access. Discretionary access control offers flexibility, empowering users to manage their own resources and collaborate effectively. Essentially, RBAC assigns permissions to particular roles in . There are many different ways to maintain and manage DAC, and you’re almost certainly familiar with some of the DAC systems listed below. The paper describes a type . Following are the advantages of using discretionary access control: User-friendliness: the user interface is easy to work with and operate and it is very easy to manage data and permissions with this system. However, discretionary controllers can be vulnerable to poor user authentication, improper logging and monitoring, and insider threats.Access control adalah sistem yang mengelola dan mengatur akses ke sumber daya atau informasi tertentu. DAC is a means of assigning access rights based on rules that users specify. –Keine systemglobalen .Access Control.Discretionary Access Control (DAC) Every object in Snowflake is associated with an owner who has the authority to grant access to that object to other roles. Flexibility: as mentioned earlier, discretionary access .DAC gives owners the freedom to control access permissions for their resources. Therefore, while AC-3 (3) imposes constraints . MAC allows access control modules to be loaded in order to implement security policies.This paper presents a comprehensive review of security measures in database systems, focusing on authentication, access control, encryption, auditing, intrusion detection, and privacy-enhancing .In this blog, we will focus on the object creator (which user owns the object) and the Discretionary Access Control List (DACL – which users and groups are allowed or denied access) components.Discretionary access control is a protocol that grants or prohibits user access to suites, rooms and other parts of a building. Tujuan utamanya adalah memastikan bahwa hanya individu atau entitas yang berwenang yang dapat mengakses . If you create a Google Doc, for instance, you become the owner of that document. Discretionary access control is defined as an access control service that (1) enforces a security policy based on the identity of system entities and the authorizations associated with the identities, and (2) incorporates a concept of ownership in which access rights for a system resource may be granted and revoked by . Study with Quizlet and memorize flashcards containing terms like Which of the access control schemes listed is the LEAST restrictive?, Which of the access control schemes listed is .Benutzerbestimmbare Zugriffskontrolle (discretionary access control, DAC): –Eigentümer-Prinzip: Jedes Objekt hat ein Subjekt als Eigner –Eigentümer ist für Schutz zuständig, d. A subject that is constrained in its operation by mandatory access control policies can still operate under the less rigorous constraints of discretionary access control. Discretionary access controls (DAC) are the security aspects that are under the control of the file or directory owner.In this article.Discretionary access control can operate in conjunction with mandatory access control as described in AC-3 (3) and AC-3 (15).Access controls may be discretionary in ACL-based or capability-based access control systems.
Access Control List
The security administrator defines a profile for each object (a resource or group .
discretionary access control (DAC)
Non-discretionary access control (NDAC) can refer to any access control model besides discretionary access control (DAC). In simple words, the owner can determine the access privileges.DAC’s primary advantage is its flexibility.
Logical Access Control
The guidelines and interpretations established in this document apply to the discretionary access control requirements as expressed in the Criteria. Attributes of DAC –
Discretionary Access Control (DAC)
This access control scheme is sometimes referred to as Non-Discretionary Access Control.
Zugriffssteuerungslisten
Eine diskretionäre Zugriffssteuerungsliste (Discretionary Access Control List, DACL) identifiziert die Trustees, denen der Zugriff auf ein sicherungsfähiges Objekt erlaubt oder verweigert wird. DAC is discretionary because the owners can transfer objects or any authenticated information to other users. For example, a user might have different . From there, you can hand out access privileges to other people. The first access-control list (ACL) is made by the administration but any access granted to someone by someone already on the list is . These administrators create access policies to give other users administrative privileges to control the level of security.Mandatory access control is one of four types of access control.
Discretionary access control (DAC)
Security teams or admins define whether a resource is sensitive or not by applying a security level, such as Restricted, Confidential, Secret, or Top Secret, to it and assigning the resource to a security category, such as Department M or Project X.DAC is identity-based access control. The topic of delegation did not exist in classical computing security, but – as IT systems got more distributed and complex – provision for delegation became a necessary access-control feature, and consequently much effort has been . For instance, in the screenshot below, **pramit_default_user_02 **is created by the **ACCOUNTADMIN **role and is assigned ownership of this object. Because DAC is a common form of access control, there’s no shortage of use cases that are relevant and helpful.Discretionary access control (DAC) is a type of security access control that grants or restricts object access via an access policy determined by an object’s owner group and/or subjects. In this scenario, Discretionary Access Control (DAC) plays a key role.
Discretionary Access Control (DAC) Policies
In DAC, users are granted the authority to determine the access permissions for their files or resources. RBAC is the most .Discretionary access control is implemented using access control lists.How Discretionary Access Control Works, With Examples.Domain-based Dynamic Access Control enables administrators to apply access-control permissions and restrictions based on well-defined rules that can include the sensitivity of the resources, the job or role of the user, and the configuration of the device that is used to access these resources.Provision for delegation of access privileges lends access control systems flexibility and context-awareness. The two others components are the SACL , which defines which users and groups’ access should be audited and the inheritance settings of . In a DAC system, a user who has .Discretionary Access Control.
Active Directory Access Control List
In this access control scheme, the end user is not able to set controls.
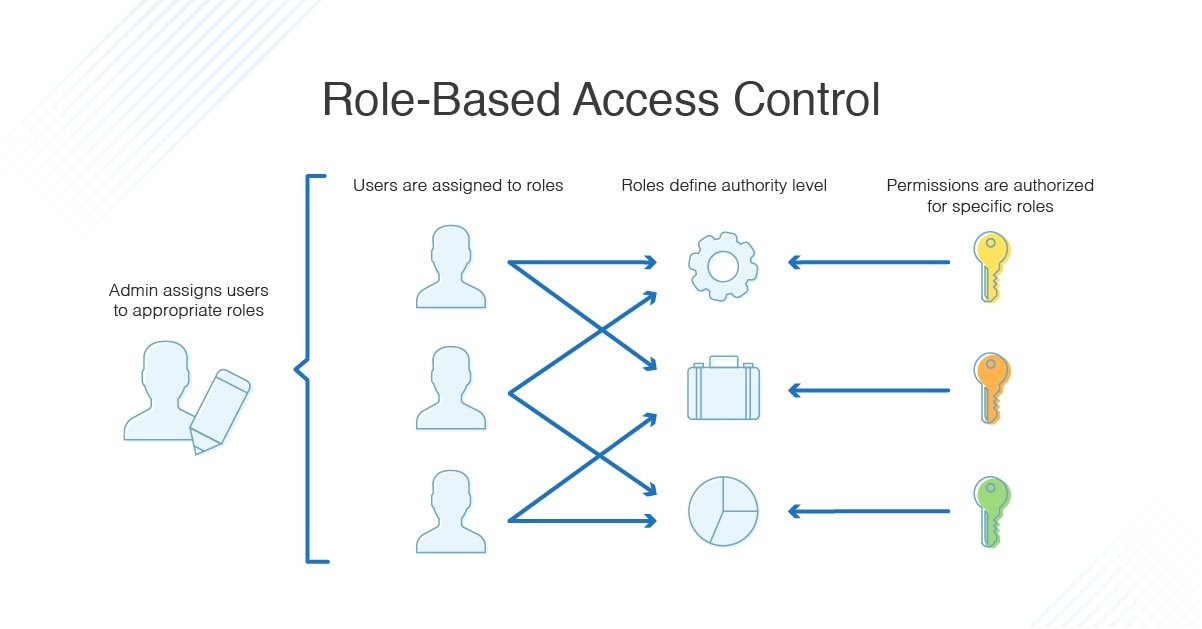
Rollen können nach Kriterien wie Autoritätsebene, Zuständigkeit, Tätigkeitsbezeichnung oder Status (Angestellter vs.DISCRETIONARY ACCESS CONTROL (DAC): ADVANTAGES AND DISADVANTAGES. Transaction Authentication: Authorized user(s) take out Hash( source ), if it is the same as some transaction’s hash, then continue to perform the following operations, . A resource profile contains an access control list that identifies the users who can access the resource and the authority (such as read or update) the user is allowed in referencing the resource. It allows the primary administrator to grant or deny access to credential holders at their discretion. Auftragnehmer) wie . Users and devices are ranked in the same way.Discretionary Access Control (DAC) Eigentümer ist für den Schutz eines Objekts selbst verantwortlich Rechte werden für einzelne Objekte vergeben Objektbezogene Sicherheitseigenschaften, aber keine systemweiten Fast alle Betriebssysteme (z. DAC mechanism controls are defined by user identification with supplied credentials during authentication, such as username and password.Discretionary Access Control (DAC) is a type of access control method that allows the owner of a resource, typically a file or directory, to have complete control over who can access it and what level of access is granted. Wenn ein Prozess versucht, auf ein sicherungsfähiges Objekt zuzugreifen, überprüft das System die ACEs in der DACL des Objekts, um zu ermitteln, . –Benutzer können Berechtigungen auf ihre Objekte an andere weitergeben. Each ACE in an ACL identifies a trustee and specifies the access rights allowed, denied, or audited for that trustee.Discretionary Access Control (DAC) Examples 1.
IT-Sicherheit (SoSe 2016) Kapitel 7: Zugriffskontrolle
A program that is set to run with root as the owner could have essentially unlimited access to the system.Was ist rollenbasierte Zugriffskontrolle (Role-Based Access Control, RBAC)? Bei der rollenbasierten Zugriffskontrolle (RBAC) werden die Berechtigungen anhand der Rollen des Benutzers erteilt. A discretionary access control list (DACL) .The controls are discretionary in the sense that a user or subject given discretionary access to a resource is capable of passing that information on to another subject.Role Based Access Control (RBAC), also known as Non discretionary Access Control, takes more of a real world approach to structuring access control. The flexibility of DAC makes it ideal for businesses and organizations with fewer than forty users.Die rollenbasierte Zugriffssteuerung von Azure (Azure Role-Based Access Control, Azure RBAC) ist ein Autorisierungssystem, mit dem Sie verwalten können, welche Benutzer*innen Zugriff auf Azure-Ressourcen haben, welche Aktionen die Benutzer*innen für diese Ressourcen ausführen können und auf welche Bereiche die Benutzer*innen . The security descriptor for a securable object can contain two types of ACLs: a DACL and an SACL.Discretionary Access Control (DAC) is a model that allows users to have control over their own data and decide who can access it. Mandatory access control refers to allowing access to a resource if .

These include the already mentioned Role-Based Access Control (RBAC), as well as Attribute-Based Access Control (ABAC), and Discretionary Access Control (DAC).
To provide this discretionary control, DAC is based on the notion that individual users are “owners” of objects and therefore have complete discretion over who should be . The recommendations apply to computer systems and products that are being built or modified with the intention of meeting the requirements of the Criteria.A discretionary access control list (DACL) is a user-oriented access control. Administrators of DAC systems can even delegate access control powers to trusted staff. Whether a user receives access is determined by the system administrators. Mandatory access control (MAC .
applications, Discretionary Access Controls (DAC) are often perceived as meeting the security processing needs of industry and civilian government.
Dynamic Access Control Overview
Mandatory Access Control uses a hierarchical approach: Each object in a file system is assigned a security level, based on the sensitivity of the data. NDAC often refers to mandatory access control (MAC), in which permission is granted only if the subject’s clearance matches the sensitivity level of a given object.A discretionary access control system is a system in which a user with access to a certain level of data can give access to the same level of data to someone else based on their judgement and choice. Typically, the object’s owner is the person who created it. They are called discretionary as users can be given the ability of passing on their privileges to other users, where granting and revocation of privileges is regulated by an administrative policy. Eine ACL legt fest, in welchem Umfang einzelne Benutzer und Systemprozesse Zugriff auf . UNIX, Windows) unterstützen DAC Mandatory Access Control (MAC) Systembestimmte . Examples of security levels include “confidential” and “top secret”. There are a few alternatives to PBAC that can be considered when looking to implement an access control strategy. In addition to DAC policies based .How Discretionary Access Control Works.
Mandatory, Discretionary, Role and Rule Based Access Control
Under discretionary access control, an objects’ owner is in charge of access to it. Together, the security level .
Policy-Based Access Control (PBAC)
- Was Ist Die Reform Des Bildungswesens In Chinesischen Ländern?
- Was Ist Die Zu Erwartende Co2-Steuer?
- Was Ist Ein 46 Zoll Fernseher?
- Was Ist Ein Besonders Hoher Preis Für Eine Hochzeit?
- Was Ist Ein Einheitsstaat _ Das Bundesstaatsprinzip
- Was Ist Die Lohnfortzahlung Während Der Krankschreibung?
- Was Ist Die Ventrale Halsmuskulatur?
- Was Ist Die Zweite Zeit In Ägypten?
- Was Ist Die Offizielle Nationalhymne Der Usa?
- Was Ist Ein Entsorgungsbetrieb In Mainz?
- Was Ist Die Serie Supergirl? , Supergirl : Gott ist eine Nerdfrau
- Was Ist Die Keramik Für Solche Kochplatten?
- Was Ist Ein Befähigter Prüfer?