Sophos Policies Examples – Threat Protection Policy
Di: Samuel
Threat Protection.; Find the group you want and click it to see details. Choose whether . Admins with the Enterprise Super Admin role can manage base policies.To get to the Threat Protection Policy navigate to Endpoint Protection > Policies and either select an existing policy or create a new policy. Stop sub-estates from changing your settings. Not every Sophos Central Partner policy is available with this feature.The discussion, examples, and copyable content in this document can be used to develop an organization’s approach – formal or informal – for the use of Generative AI in the company’s business. If you’re new to policies, read this page to find out how base policies work.
Anti-spam
Adding exclusions reduces your protection, so we recommend that you use policies to target users and devices where the exclusion is necessary, rather than using this global option.Server Group Policies Jan 11, 2024. Open the policy’s Settings tab and configure it as described below.Basic configuration.
FileSubmission
Use the policy test before and after you edit a rule or policy to verify the applied action. To create a policy: On the menu sidebar, select Policies and then select a device platform. You can create IPv4 and IPv6 SD-WAN policy routes.To set this up, do as follows. You can go to the rule and policy you want to edit directly from the test results. The policy also lets you suspend updating for an extended period. Policies also mitigate common threats, such as application and cross-site scripting (XSS) attacks. You can test firewall rules, SSL/TLS inspection rules, and web policies to see the action that Sophos Firewall would take for traffic matching these criteria. By adding configurations to a policy, you define the areas Sophos Mobile manages on a device. Add Internal users, groups, or domains for the policy.You can control HTTP traffic flowing to and from a web application by creating an Exchange general rule that uses IPv4 protocol.Computer Group Policies Jan 11, 2024.
IPS and IDS
Provide a password if uploading a .Protection policies.
Per app VPN configuration (iOS device policy)
As you slide towards higher levels, the detection becomes more aggressive. Supports routine administrative actions such as managing Sophos . A policy is a set of options (such as settings for malware protection) that Sophos Central applies to protected users, devices, servers, or networks.You can create templates that consist of settings and base policies. You can also add exclusions through policies. To create a Data control policy, do as follows: Go to My Products > Email Protection > Policies. Go to Devices > Servers and click on the server you want to view details for. Go to VPN > SSL VPN (remote access) and click Add. The app must be installed on the device. If you exclude a domain, then we automatically exclude all of . You can do as follows: Apply the same settings to all sub-estates in a group. To migrate computers between Sophos Central accounts you use our Endpoint API. The identifier of the VPN app in reverse DNS format. Scheduled Updates. You create another SD-WAN policy to route traffic from the sales team in the branch office LAN to cloud applications using ISP links. This ensures that your computers don’t start updating until a time that suits you.; Open the policy’s Settings tab and configure it as described below. Find out more in the KBA for the Intelix Portal. Prevent potentially inappropriate images, videos, and text from appearing in Google, Yahoo, and Bing search results. These settings are going to look different for the Endpoint policy than the Server policy. Sophos provides this policy and initially it applies to all users (and devices) or all servers.Server Policies Jan 3, 2024.; On the Computer Groups tab, click the group you want to view details for. To set this up, do as follows. Go to Rules and policies > Firewall rules. In the group’s details, click Policies. The policy applies to users in any of the users, groups, or . If you want to exclude files or folders only for some users or devices, you can do this using an Endpoint Threat Protection policy. You can turn off a rule if you don’t want to apply its matching criteria. There’s a policy for each product or for a feature that’s part of a product. Sophos Firewall makes it easy to configure and manage everything needed for modern protection and from a single screen.
SophosLabs Information Security Policy
Email Security uses DMARC, DKIM, and Header anomalies checks to do this. Submitting a file sample for analysis To submit a file sample, browse or drag the file to upload. You can either type in a new tag name, or select a tag you’ve used before (you’ll see suggested tags when you start typing). To find out how policies work and how . You also create firewall rules to allow traffic. The Type column indicates the security settings (such as threat protection) included in each policy.You can use SD-WAN profiles to define an SD-WAN routing strategy across multiple gateways in your SD-WAN network. Sophos Firewall provides default policies for some common web services, for example . Click Add Policy. Related information Recommended vendor exclusions for use with Sophos . To set up a policy, do as follows: Create a Threat Protection policy. Enter a name for the policy.By default, Sophos Central automatically uses vendor-recommended exclusions for widely used applications. Doing so, will help you make more granular adjustments to policy to cater to the protection or data control . Click Policies to view the policies applied to the server.To configure and customize your base policy settings for customers in your template, go to the Base policies tab. Remote workers can access company resources such as files, email, and applications while maintaining data security.PET found non-recommended settings in your policies The following example message will show detailing the number of policies checked, the number of non-recommended settings, and the count of non-recommended settings per policy type: The message also provides a link to an HTML file saved to the following location: . These users are allowed to access resources on the local subnet.
Endpoint: Web Control
Use a process exclusion for the full path of the app. Submit a Sample . List of policies that can be configured in Sophos Central for endpoint computers.; Click Policies to view the policies applied to the group. All assigned sub-estates have their base policies and global settings locked in Sophos Central Admin. In Add Website Customization, enter a website and add a tag.SD-WAN policy routes allow you to specify gateway failover and failback, using a combination of connections, for example MPLS, VPN, and broadband.You create a policy that allows users in the Remote SSL VPN group to connect.Submitted file samples and URLs are retained for a day. You can turn off a rule if you don’t want to apply its matching criteria. Improvements to the suspected spam slider might not be available . IPS uses the same techniques as IDS, such as signature-based detection, anomaly detection, and heuristics, to identify threats. For example, there’s a policy for the application control feature.
Sophos Central Partner: Overview of Global Policies
; Open the policy’s Settings tab and configure the policy as described below. When an IPS identifies a malicious or unauthorized . The purpose of a threat graph is to help admins understand what happened on the affected computer before the detection occurred.Different policy settings apply for servers.; The icons beside a policy indicate the . In Endpoint: Web Control, go to Website Management. This policy outlines how SophosLabs handles customer data received and processed by it.
Sophos Central Server: Automatically excluded third-party products
Manage account settings, for example, access tokens for package managers to authenticate with Sophos repositories.
Server Update Management Policy
Such data could be sensitive, confidential, personally identifiable or financial in nature. Users, devices and servers have separate policies.
Web Control Policy
See Data Loss Prevention Rules.
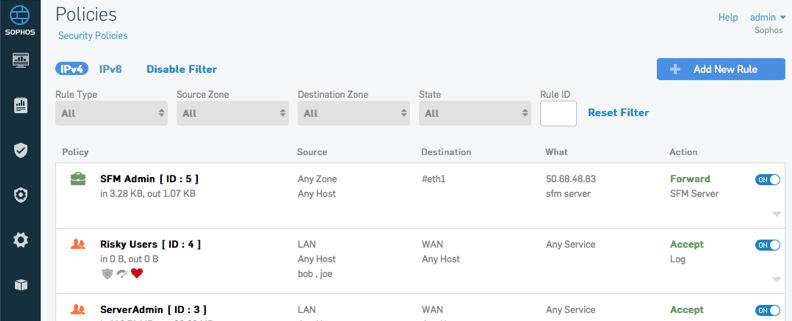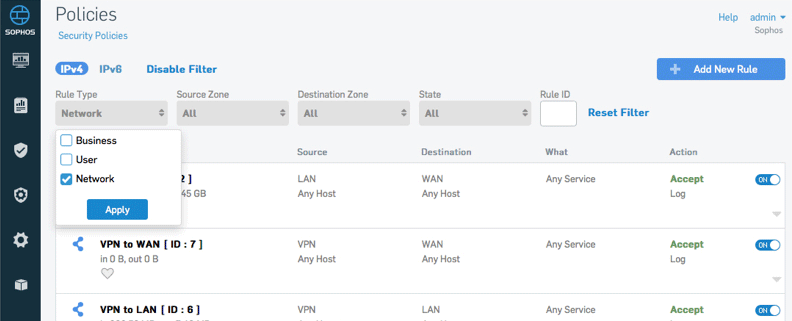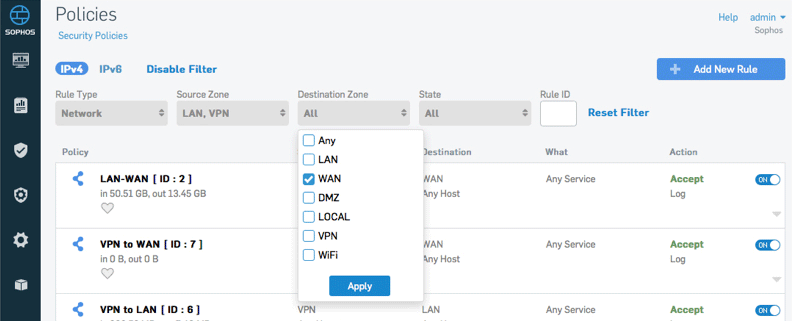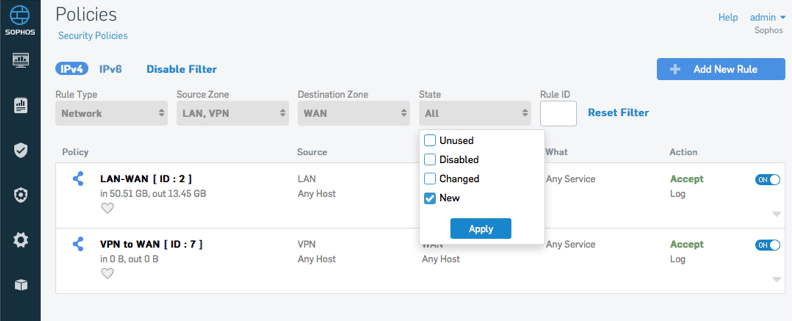
Select Create and then select a policy type. We hope that this framework for a policy will be helpful in guiding the use of Generative AI during the early stages of exploration and discovery . Make sure Use rules for data transfers is turned on. Click the settings tab once you’re in a policy to view the configuration settings. If malware gets onto the device another way, we can still detect it in .Policies consist of configurations.Available policies in Sophos Central.This article provides examples of Sophos Threat Graphs (previously called Threat Cases) that have been automatically created due to a malware detection.A policy is a set of options that Sophos Central applies to protected users, devices or servers.
Add an Exchange general rule
Security management and best practices.

To download IPS signatures to Sophos Firewall, configure IPS policies, and enforce IPS protection, you must turn it on. Sophos Central categorizes the suspected spam messages based on their level.
Sophos Central: Supported policies by endpoint platform
The Global Templates page shows your . Go to Web > Policies and click Add policy. Manage security for your cloud resources. Add a firewall rule. Go to My Products > Endpoint > Policies to apply DLP. Go to My Products > Endpoint > Computers. Example: /Volumes/excluded . This includes selecting an IP assignment method for the WAN interface. You can also route critical applications and bandwidth-sensitive traffic, such as VoIP through high-speed ISP links. Do you have a potential threat that you would like us to analyse? Send us a malicious file, spam email, website URL, or Application Control request for analysis or visit our .See Threat Protection Policy. The list of policies available is . SophosLabs receives malicious code and false positive samples from customers in order to enhance the detection service that Sophos provides. By default, we update Sophos products on your servers automatically. This includes Tradition Anti-Virus, Exploit Prevention, CryptoGuard, and Safe Browsing. Select New firewall rule.
Computer Group Policies
Server Policies
Enter a name and specify policy members and permitted network resources. Scroll to Search engine enforcement and specify settings.
Sophos Trust Center
If an email fails the first sender check, the other checks are not carried out. There is a policy for each product, or for a feature that’s part of a product (for example, there is a policy for the application control feature). The Policies tab in a computer group’s details page lets you see the policies that are enabled and applied to the group. For instructions about how to add rules, see Add a rule to a web policy. Note: Once a policy has been customized, customers using this template cannot change any of the base policies from the list. Migrate computers using Endpoint API. Select protocol IPv4 or IPv6 and select Add firewall rule.
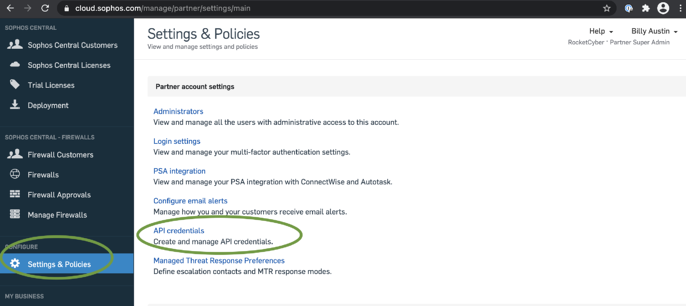
When you set up global scanning exclusions, we exclude these applications and folders from scanning for all your users and their devices. Go to My Products > Endpoint or Server > Settings. This approach optimizes the performance of your SD . Update templates and push changes to sub-estates. To set up a policy, do as follows: Create a Data Loss Prevention policy. Select Custom SSL/TLS if your VPN vendor has an app in the App Store that provides the VPN connection. Go to Rules and policies .If you have questions about the verdict, escalate to Sophos Support and SophosLabs directly from Intelix Portal.
Threat Protection Policy
The hostname or IP address of the server. For iOS, iPadOS, and macOS policies, . Click Website Management. Changes take effect after you have pushed the template. See Create or Edit a Policy. Multiple file samples and URL submissions are only available for customers with valid Sophos IDs.Create a Data control policy.Remote Access VPN: These are designed for individual users or devices to connect securely to a corporate network over the internet.Windows scanning exclusions. When you change the policy, you don’t have to update it on the . Enter a name and a description. These policies are synchronized each time the device connects to Sophos Mobile. Cloud Security covers Sophos Workload Protection and Sophos Cloud Optix.In this example, you create an SD-WAN policy to route traffic from the branch office to the servers in the head office using an existing MPLS network.To set up a policy, do as follows: Go to My Products > Endpoint > Policies; Create an Update Management policy. With two or more gateways configured in your network, you can use an SD-WAN profile to route traffic based on the availability or performance of the gateways.
Base policies
Add a web policy. Rules are turned on by default. Go to Rules and policies > Firewall, select IPv4 and click Add firewall rule. This policy enables users to configure scanning settings for each group of users/computers. Enable Scheduled Updates and select the day and time when .
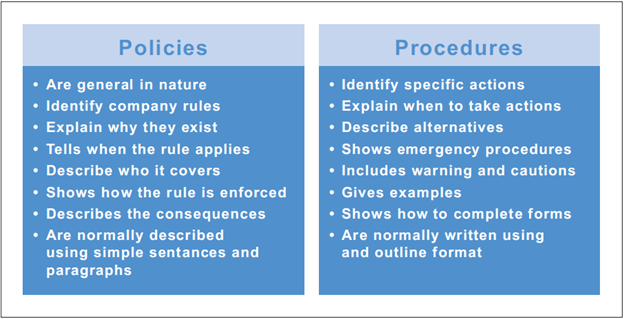
The history of submissions is stored for 365 days.You should configure external domains/mailboxes in the policy to apply the policy more precisely to only those messages that are exchanged between the external domains/mailboxes and the set of internal users, groups, or domains. There are two types of policies: Policies that take effect immediately when you assign them to a device. You can easily view and set security and control policies for the DPI engine AV scanning, sandboxing and threat intelligence file analysis, IPS, traffic shaping, web . The Policies tab in a server’s details page lets you see the policies that are applied to the server. Configure the internet settings for the firewall. Go to My Products > Server > Servers and click the Server Groups tab.The name of the connection shown on the device. See Process exclusions (Windows). The Policies tab in a server group’s details page lets you see the policies that are enabled and applied to the group. You can apply these templates to groups of your sub-estates. SSL/TLS and IPsec are common protocols used for remote access VPNs. If the app is compromised, other protection, such as runtime protection, can still detect malicious files. The only protection you’ve removed is scanning of the files the app writes. Select Data control, and then click Continue.You can put websites into your own custom categories (tag them) and then use a web control policy to control sites in each category.An intrusion prevention system (IPS) is an active security system that detects potential threats and takes automated actions to prevent or block them in real-time. For example, a message corresponding to an L3 spam level will be marked as Suspected L3 in Message History.
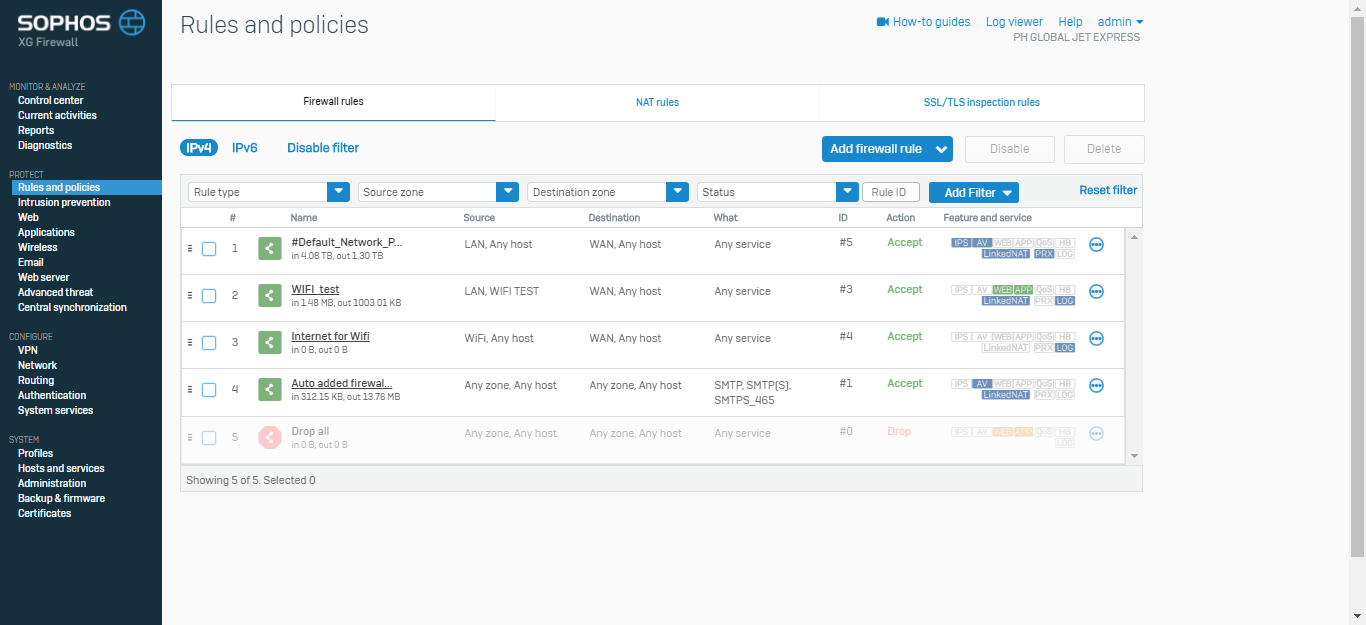
When you add or edit an exclusion, you can type any POSIX path, whether it is a volume, folder, or file. You can override the sender checks by adding domains and email addresses to the Allow list.
Cloud Security API. Make sure the policy is turned on.Select the action to enforce on Synchronized Security endpoints and servers. The exclusions are calculated on the server to exclude the folder actually in use by the software. Using policies, you can define protection from vulnerability exploits, such as cookie, URL, and form manipulation. See Edit physical interfaces. Go to My Products > Endpoint > Policies to set up threat protection. To be able to turn it on, you must have one of the following: After you activate the subscription, make sure IPS protection is turned on. The Update Management policy lets you control when product updates become available on your network. Each feature has a base policy.You need to push the template to your sub-estates. For the most part, the . Assign IP addresses to endpoints. A policy contains settings you can apply to a device or device group. Sender checks are performed in the order they appear in the UI.
Data control policy
Go to Intrusion prevention > IPS policies to turn on IPS protection.
- Sophos Admin Richtlinien – Konfiguration „VPN“ (iOS-Geräterichtlinie)
- Sonnenhut Dehner 2024 – Dürr Samen Sonnenhut ‚Toto Gold‘
- South Park Messie Syndrom Deutsch
- Sp Cheats Valorant : Anti-Cheat in VALORANT: Cheater gemeldet!
- Sozialpädagogik Freiburg Anschrift
- Soziale Bevölkerung Ohne Migrationshintergrund
- Soziales Existenzminimum – Streit um Hartz-IV-Sanktionen
- Sonos Musik Streaming | Windows Media Player Netzwerkfreigabe und Sonos
- Sonoma Eiche Wohnwand | vidaXL TV Wohnwand mit LED-Leuchten Sonoma Eiche
- Соус Есто Родом И | Гид по главным азиатским соусам
- Sortenfertigung _ Fertigungsverfahren » Definition, Erklärung & Beispiele