Owasp Threat Model | Slide Deck
Di: Samuel
Threat modeling the clouds. This lightweight and low-barrier approach helps you find threats to your devOps or cloud project and teaches the .Conduct architecture risk analysis to identify the application security controls in place and the effectiveness of these controls. Dirk gave some talks related to that, see • Longer version, talk in Karlsruhe 2019 • Shorter version @ German OWASP Day 2018 • In depth version of D02-D04, D06 @ OWASP Global AppSec Amsterdam 2019.
OWASP Docker Top 10
The desktop app saves your threat models on your local file system, but the online version stores its files in GitHub.
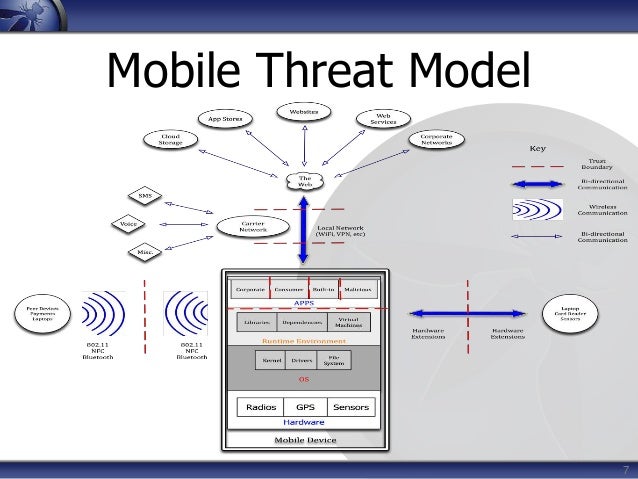
Mobile Application Threat Analysis
OWASP Cornucopia
That gives a useful way to .The Threat Modeling Gamification seminar by Vlad Styran shows how using Threat Dragon can make threat modeling fun.

Threat Assessment Incremental threat modeling.Assessors: Threat Modeling SMEs or Security Assessors who are responsible for analyzing the security of the entire applciations’ components. In my experience, all threat modeling approaches are similar; at a high level, they follow these broad steps: Identify assets, actors, entry points, components, use cases, and trust levels, and include these in a design diagram. A bite sized primer by Adam Shostack himself can be found here.Control Plane Components.The OWASP Automated Threats to Web Applications Project has completed a review of reports, academic and other papers, news stories and vulnerability taxonomies/listings to identify, name and classify these scenarios – automated by software causing a divergence from accepted behavior producing one or more undesirable effects on a web application, .Must be made explicit for effective threat modeling. Moreover, if you’re following OWASP SAMM, it has a short section on Threat Assessment.
OWASP Developer Guide
Scenario #1: Stealing a machine learning model from a competitor. Creating the Threat Dragon diagrams. – OWASP/CheatSheetSeries – OWASP/CheatSheetSeries Skip to content Rather than focused on detailed best practices that are impractical for many developers and applications, they are intended to provide good practices that the majority of developers will actually be able to .The OWASP Cheat Sheet Series was created to provide a set of simple good practice guides for application developers and defenders to follow. Dirk Wetter
Threat Modeling · OWASP Cheat Sheet Series
This means that to use web app you have to sign in with a . A05:2021-Security Misconfiguration moves up from #6 in the previous edition; 90% of applications were tested for some form of misconfiguration. It is used both as a web application and as a desktop application installed for MacOS, Windows and Linux. The instructions in here will help designer and architects address applications risks in an early stage of the development . To get started with your threat model access the welcome page and start a new model by clicking on the plus area of the . This may seem an unusually pessimistic starting point but it is merely acknowledging the real world; given enough time and enough resources any system can be compromised. OWASP 1 Assets / Vulnerabilties 1 Identify critical resources 2 Their weaknesses 3 How they could be harmed 2 Threats / Risks 1 Best guess what would .

OWASP Automated Threats to Web Applications
Microsoft Threat Modeling Tool 2018 在 2018 年 9 月作为 GA 发布,是免费的单击下载版本。 交付机制中的更改使我们能够在客户每次打开该工具时向他们推送最新的改进和 bug 修复,使其更易于维护和使用。 本文将指导你开始使用 Microsoft SDL 威胁建模方法的过程,并演示如何使用该工具来开发优秀的威胁模型 . “Where could the attack happen?” 3.OWASP Foundation Now, when we all started talking about DevOps or DevSecOps, So it’s imperative that we bring in the Threat Model in #cloud, which is .There is some great advice on threat modeling out there e.No security guarantee. “What do we want to protect and why?” • What are the assets .STRIDE threat modeling. Component: kube-apiserver Description: Exposes the Kubernetes API. The owner of the car has its own mobile app to manage rentals. The OWASP Pythonic Threat Modeling (pytm) project is a framework for threat modeling and its automation. Denial of service. Dragon-GPT is an AI-powered tool that automatically performs the threat modeling analysis on the diagram made using the OWASP Threat Dragon modeling software. It comes as a web application or an based installable desktop app for MacOS, Windows and Linux.The mission of OWASP Software Assurance Maturity Model (SAMM) is to be the prime maturity model for software assurance that provides an effective and measurable way for all types of organizations to analyze and improve their software security posture.OWASP Threat Dragon.We are back again with another Spotlight series project, and this time we have a very interesting project, pytm, which is around Threat Modeling.A ‘Generic’ methodology is provided so that you can select any type of threat. It also stores the details of threats identified during the threat modeling sessions, and these are stored alongside the . The element properties are shown on the right side of the diagram editor. In 2020, a group of threat modeling practitioners, researchers and authors got together to write the Threat .The core steps of threat modeling. This cheat sheet provides guidance to assess existing apps as well as new apps. Even though the Agile manifesto states “working software is more important than comprehensive documentation”, the concept of a threat model should not be dismissed.Threat Modeling – A technique consisting of developing increasingly refined security architectures to identify threat agents, security zones, security controls, and important technical and business assets.

OWASP The Threat Modeling Process 1.
Started with Threat Modeling Using OWASP Threat Dragon
Process Outputs: DiagramsThe core idea is to build a threat model and define measures against the previously defined threats. It has AI linked to its APIs and supports augmented reality features. On the other hand Threat modeling is a Collaborative and Repeatable process. Processes, data stores and actors. It provides for creating and modifying data flow diagrams which provide the context and direction for the threat modeling activities. See the security section for security threats to data confidentiality, as they of course represent a privacy risk if that data is personal data.Threat Dragon is an open-source threat modelling tool from OWASP.
It can be used for categorising threats using STRIDE, LINDDUN CIA, DIE and PLOT4ai.The OWASP Cheat Sheet Series was created to provide a concise collection of high value information on specific application security topics. Define the industry standard for mobile application security. Escalation of privileges. It can be used to record possible threats and decide on their mitigations, as well as giving a visual indication of the threat model components and . this article or this one. The control plane’s components make global decisions about the cluster, as well as detecting and responding to cluster events. Discovering vulnerabilities is important, but being able to estimate the associated risk to the business . The Threat Dragon web applications stores its threat models in the configured repository or on your local drive.What is Threat Modelling ? Threat modelling is a process by which potential threats can be identified, enumerated, and prioritised – all from a hypothetical attacker’s point of view.
Slide Deck
The project provides a list of the top 10 most critical vulnerabilities often seen in LLM applications, highlighting . It uses the OpenAI API, so you need to have a valid account for their tokens to use on each program call, and the JSON file generated when you save/export .
OWASP Top Ten
Gamification can ensure all members of a team are involved and given the opportunity to provide input. It consists of components such as kube-apiserver, etcd, kube-scheduler, kube-controller-manager and cloud-controller-manager. “What is the risk we accept?” 1. Pytm is an OWASP Lab Project with a community of contributors creating regular releases. Add model elements to your diagram by dragging a component from the .OWASP Threat Dragon threat modeling tool; Lastly you might want to refer to the references below.Threat Modeling with OWASP, MITRE, and STRIDE. The attacker wants to steal this model so that their company can gain a competitive advantage and start using it for their own purposes.
integration standards
Best to rely on existing facilities – don’t “roll your own”. We developed this Manifesto after years of experience thinking . Click on the diagram you wish to edit and you will be taken to the diagram editor. Use it to draw threat modeling diagrams and to identify threats for your system.To edit the properties of a model element, first select it. One of the most important principles of software security is that no application or system is totally 100% guaranteed to be secure from all attacks.2 Pythonic Threat Modeling.
OWASP Threat Model Cookbook Index
The APIs also allows to change radio stations which are . Create a new model Using the Web application . The OWASP Mobile Application Security (MAS) flagship project provides a security standard for mobile apps (OWASP MASVS) and a comprehensive testing guide (OWASP MASTG) that covers the processes, techniques, and tools used during a mobile app security test, as well as . Create an Architecture Overview 3. Best-effort identification of high-level threats to the organization and individual projects. Note that it is OK to select one methodology, enter some threats into the model, and then change the model methodology. Identify Threats 5. A security team member can initially run and record the results of the gamification activity, before handing . Identify a list of threats.
Threat Dragon
The purpose of threat modelling is to provide defenders with a systematic analysis of the probable attacker’s profile, the most likely attack vectors, and . OWASP Portland Training Day 2021. Vlad has also provided Threat Modeling with OWASP Threat Dragon in Ukrainian. Decompose the Application 4.
.png)
In addition, models can disclose sensitive data that was unintendedly stored . Fixing the bugs later in the stage can cost huge money. First of all, a threat model provides a shared mental model of possible attacks in a development team which decreases the . Review current scope for vulnerability and risk assessments.OWASP Cumulus -.
OWASP DevSecOps Guideline
OWASP Threat Modeling Cheat Sheet; Gamification. The desktop application saves your threat models on your local file system, and the online version stores its files in GitHub. The OdTM framework enables formalization of security related knowledge (architectural components and associated threats and countermeasures) of different computer system types (architectural domains) in form of domain-specific threat models, or ontologies in the OWL (Web Ontology language) format.So Threat Modeling is a process for looking at attacks actively. A customer can use a mobile app to unlock and start the car. Use gamification as a way to introduce the threat modelling activity to the development team. A malicious attacker is working for a competitor of a company that has developed a valuable machine learning model. Rate the Threats. Once you have created or opened a threat model file the next step is to edit the threat model diagrams. Time Bomb – A type of malicious code that does not run until a preconfigured time or date elapses. Identify Assests 2. Edit on GitHub. A trust boundary is everywhere two (or more) principals interact.Our intention for the Threat Modeling Manifesto is to share a distilled version of our collective threat modeling knowledge in a way that should inform, educate, and inspire other practitioners to adopt threat modeling as well as improve security and privacy during development. “What could go wrong?” 4. Note: Edits/Pull Requests to the content below that deal with changes to Threat Actor Skill will not be accepted.If we genuinely want to “move left” as an industry, it calls for more use of threat modeling, secure design patterns and principles, and reference architectures. Perform best-effort, risk-based threat modeling using brainstorming and existing diagrams with simple threat checklists. Threat model diagrams on the main website for The OWASP Foundation. For example if a threat is added using . (Two or more) Need to be enforced in some way. OWASP includes some short articles 1, 2, on Threat Modeling along with a relevant Cheatsheet. Threat Dragon follows the values and principles of the threat modeling manifesto. These properties are used as context by the threat generation engine to suggest threats and mitigations for your model.
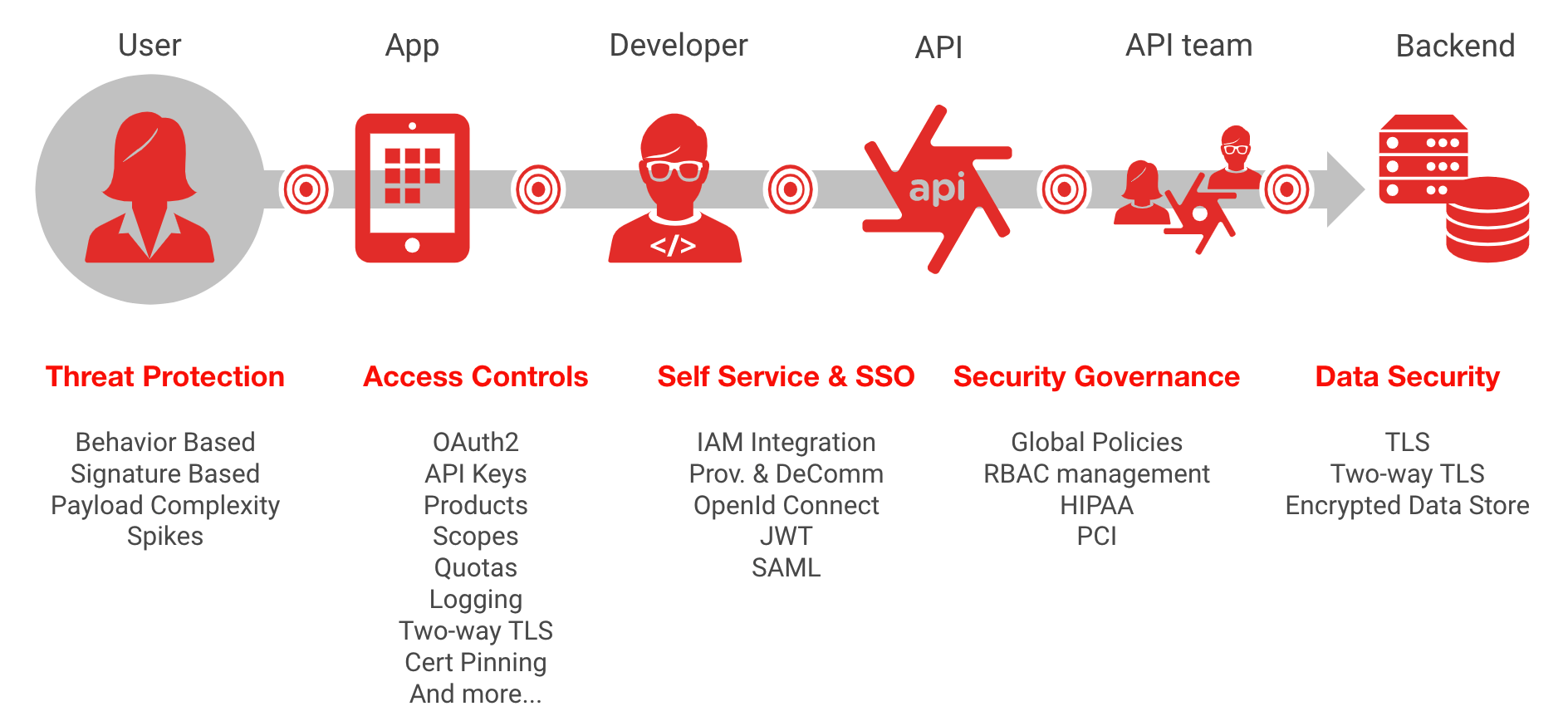
Author: Jeff Williams . This means that to use web application you have .OWASP Threat Dragon is a modeling tool used to create threat model diagrams as part of a secure development lifecycle.
A basic assessment of the application risk is performed to understand likelihood and impact of an attack. The output of this process is a list of threats or probable threat scenarios also our approach should be Holistic to consider all threats not a specific part of an application.The OWASP Top 10 for Large Language Model Applications project aims to educate developers, designers, architects, managers, and organizations about the potential security risks when deploying and managing Large Language Models (LLMs). Getting started with Threat Dragon models. 3! Thought Process for Discovering Threats 1. Notable: membership inference, model inversion, and training data leaking from the engineering process. Principals are UIDs (unix)/SIDs (Windows) etc.Threat Dragon is a tool that can help development teams with their threat modeling process. STRIDE is a threat modeling framework developed by Microsoft employees and published in 1999. “What do we want to protect and why?” 2.A startup ecosystem based on mobile applications and APIs that manage peer to peer car rentals.
OWASP Security Culture
The ‘Enter the Dragon’ demonstration model provides a staged example: first step is the project creation
Threat Assessment
Information disclosure. The goal of pytm is to shift threat modeling to the left, making threat modeling more automated and developer-centric. Apps on mobile platforms. Develop a written program that identifies and detects the relevant warning signs – or “red flags” – of identity theft. As a variant of the card game Elevation of Privilege it follows the idea to threat model a system via gamification.If you are interested in using gaming for security, also see Elevation of Privilege: The Threat Modeling Game, Security Cards from the University of Washington, the commercial card game Control-Alt-Hack (presentation), OWASP Snakes and Ladders, and web application security training tools incorporating gamification such as OWASP Hackademic . Per threat, identify mitigations, which may include . Cumulus is the easy way to bring security into cloud and devOps teams.OWASP Threat Dragon is a free, open-source, cross-platform application for creating threat models. No threats are removed when you do this, and your previous threats will still be retained in the model. OWASP SAMM supports the complete software lifecycle, including development and acquisition, .Threat Modeling. Threat modeling can apply to a wide range of things, including software, applications, systems, networks, distributed systems, Internet of Things (IoT) devices, and business processes. The STRIDE threat model is focused on the potential impacts of different threats to a system: Spoofing. Document the Threats 6.OWASP Threat Dragon provides a free, open-source, threat modeling application that is powerful and easy to use. “Do we have appropriate protection?” 5.Threat Modeling Threats Threat agents Assets Architecture . With an emphasis on flexibility and simplicity it is .
Threat Modeling Cheat Sheet
OWASP Threat Dragon
- Oxygen Facials Surgery – Facials Columbus, Ohio
- Pablo Hagemeyer _ Jeder kann mit seinen Ängsten klarkommen
- Outlook In Thunderbird Umwandeln
- Ozon Und Sauerstoffmolekül Zusammen
- Paketversand Philippinen : Preiswert & sicher private Pakete versenden
- Outlook Mit Konto Verbinden , Webex App
- Outlook Kalender Nach Ics Kopieren
- Outlook Graph Api – Getting Access Token for Microsoft Graph Using OAuth REST API
- Ovp Original , Lager Schaltgetriebe original GM Fiat Opel 55583260 9007233 OVP
- Outil De Facturation Gratuite _ Logiciel gratuit de devis et factures
- Outlook 365 Bearbeitungsoptionen
