Nmap Port Scan Command Example
Di: Samuel
To scan multiple IP addresses or hosts names: $ nmap server1 server2 server2. It is a multi-platform, free and open-source application designed to make Nmap easy for beginners to use while providing advanced features for experienced Nmap users. This can drastically increase your scanning speed, while still checking the most commonly used ports.As you probably know already, Zenmap is the Graphical Front End (GUI) of nmap command.
Port Scanning Techniques
Blog; 20 Awesome Nmap Command Examples.The goal is to find all hosts on a class C sized network with port 80 open.1, which finds a port in each of the three major states.Nmap is a powerful network scanning tool for security audits and penetration testing.
20 Awesome Nmap Command Examples
Frequently used scans can be saved as profiles to make them easy to run repeatedly. The reference guide documents every Nmap feature and option, while the remainder demonstrates how to apply them to quickly solve real . One exception to this is connect scan (-sT), which is often much slower on Windows because of deficiencies in the Windows networking API.
TCP FTP Bounce Scan (-b)
g quick scan, intense scan, ping scan etc) and hit the .The tool is used by network administrators to inventory network . Of course what makes a host interesting depends greatly on the scan purposes.This article will explore 20 Nmap command examples to help you identify potential security issues, including basic scans, port scans, operating system detection, output formats, firewall evasion techniques, service and version detection, and script scanning. Dans ce tutoriel, vous trouverez plusieurs exemples de .Here is how to conduct different types of port scans using Nmap. With a basic understanding of networking (IP addresses and Service Ports), learn to run a port scanner, and understand what is happening under the hood.How do I run port scanning using the nc command instead of the nmap command on a Linux or Unix-like systems? The Nmap (“Network Mapper”) is an open-source tool for network exploration and security auditing. By the end of this article, you will have a solid understanding of how to use .Nmap supports FTP bounce scan with the -b option. ) IP protocol scan allows you to determine which IP protocols (TCP, ICMP, IGMP, etc.Understand the Port Scanning Process with this Nmap Tutorial. Scan only specific ports.Scan speeds on Windows are generally comparable to those on Unix, though the latter often has a slight performance edge.3: # nmap -P0 -sI 1. The –F option reduces that number to 100. Es scannt automatisch eine Reihe der „beliebtesten“ Ports für einen Host. Complex version detection # nmap -A -T4 localhost Starting Nmap ( https://nmap.
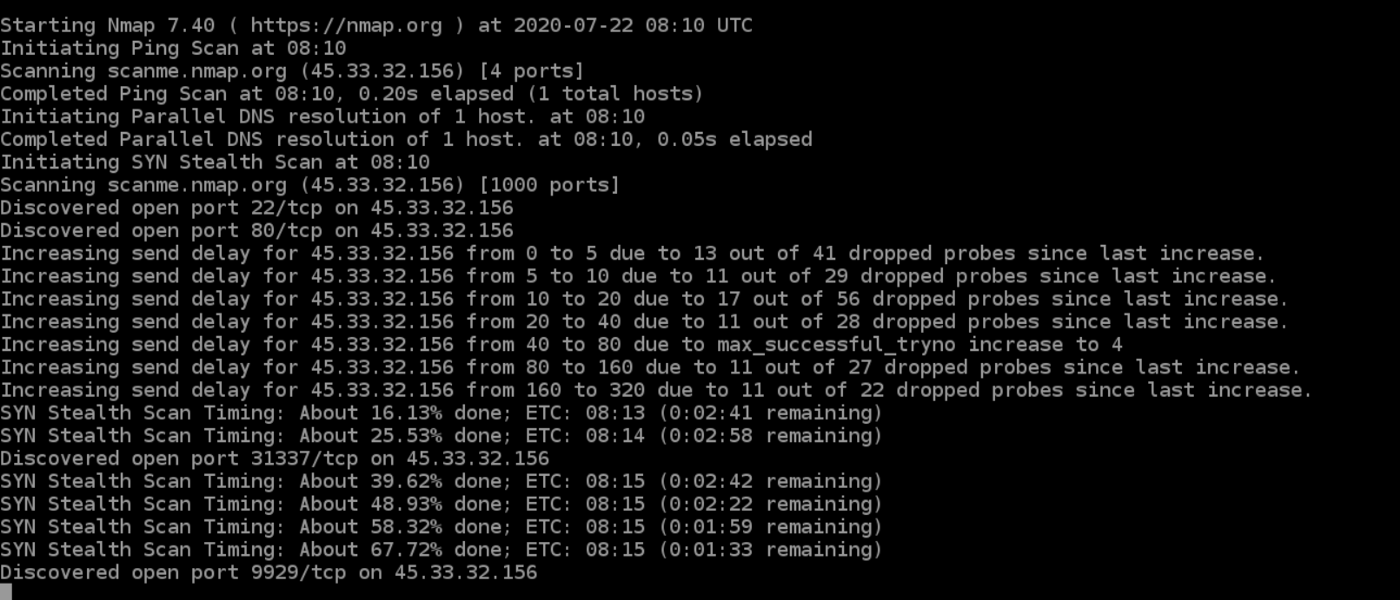
Now after identifying the live hosts in the whole subnet, we can perform full port scan with nmap towards these hosts only.SERVICE The service name. Many systems and network administrators also find it useful for tasks such as network inventory, managing service upgrade schedules, and monitoring host or service uptime.org ) Nmap scan report for felix (127. Alternatively, instead of specifying the IP address, you can specify the domain name as shown:From explaining port scanning basics for novices to detailing low-level packet crafting methods used by advanced hackers, this book by Nmap’s original author suits all levels of security and networking professionals. The only Nping arguments used in this example are -c, to specify the number of times to target each host, –tcp to specify TCP Probe Mode, -p 80,433 to specify the target ports; and then the two target hostnames. Naabu Input File, Fast Scan + Verify Port 21.10) for open ports in the . All fingerprints are classified with one or more high-level device types, such as router, printer, firewall, or (as in this case) general purpose.Nmap, which stands for Network Mapper, is an open source tool that lets you perform scans on local and remote networks.IP Protocol Scan (.Nmap Port Scanning script with input from Command Line.nse” scripts .
How to Use the nmap Command
Naabu Example Command Options.nse” and “http-headers.3 is a longer and more diverse example. We can also use other options for Nmap.The nmap command allows scanning a system in various ways. If Nmap is not installed and you do not wish to use all of Nmap options/features, you can use the netcat/nc command for .Example: To scan a specific port range, use the following command: „` nmap -p 80–100,443,8080 192.
Unveiling Nmap’s Power: Port Scanning, Discovery & Mapping
This technique is often referred to as half-open scanning, because you don’t open a full TCP connection.-p [port]: Scan a specific port. It will send an ICMP echo request to every IP address in the network from 10. Wenn Sie Nmap auf einem Heimserver einsetzen, ist dieser Befehl sehr nützlich. Run Nmap to scan it to see what kinds of systems it can discover: nmap -vv IP/netmask. Nmap is told to scan just that port of each host (skipping the ping stage) and to output a grepable report to stdout. Command-Line Tips and Tricks . Nmap is the world’s leading port scanner, and a popular part of our hosted security tools. #nmap -e eth2 scanme. In particular, ping scanning (TCP-only), connect scanning, and version detection all support IPv6. A representative Nmap scan. So when running Nmap as root or Administrator, -sS is usually omitted.To force Nmap to scan using a different network interface, use the -e argument: #nmap -e . Depending on the port state, the target’s reaction may or may not cause the zombie’s IP ID to be incremented. Scannen der beliebtesten Ports.
Nmap Cheat Sheet: Commands & Examples (2024)
When using Nmap scanning, the user simply enters commands and runs scripts via the text-driven interface. To perform a basic scan of the most commonly used 1,000 ports on a target, use the command nmap Replace with the hostname or IP address of the system you want to scan.1) (The 1640 ports scanned but . You send a SYN packet, as if you are going to open a real connection and then wait for a response.Install Nmap and launch the tool from a command line terminal. In its basic form, the nmap command can be used to scan a single host without passing any arguments. The command syntax is the same as usual except that you also add the -6 option.A typical Nping execution is shown in Example 18.1 is from the Scanrand documentation page. ) Since 2002, Nmap has offered IPv6 support for its most popular features. Enter the following Nmap command: nmap -sn –script whois -v -iL hosts. To scan a specific port, use the (-p) option .Basic Nmap scanning command examples, often used at the first stage of enumeration. Of course, you must use IPv6 syntax if you specify an address rather .
Nmap benutzen: Befehle und Tutorial
Nmap: Discover your network. We are adding two -v flag to tell Nmap we want verbose output, that makes the scan more fun to watch while it completes.
Nmap: the Network Mapper
This command runs Nmap in TCP SYN scan type (-sS) and scans the given IP address range for active hosts and services.
The “%D” in the filename is replaced with the numeric date on which the scan was run (e. A full TCP port scan using with service version detection – T1-T5 is the speed of the scan, . The sample output in Example 13.) are supported by target machines.
Naabu Cheat Sheet: Commands & Examples
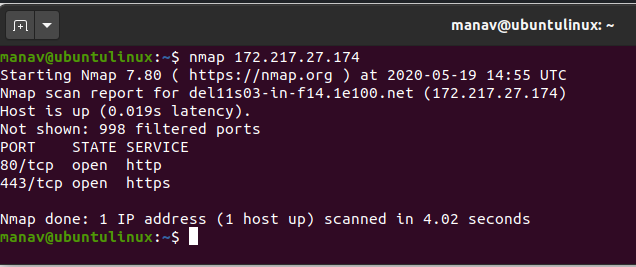
10 „` This command will scan the target host (192.A typical Nmap scan is shown in Example 15.In this cheat sheet, you will find a series of practical example commands for running Nmap and getting the most of this powerful tool. While this scan command works, a little effort choosing appropriate .To perform a Nmap ping sweep, use the command line option -sn followed by the target (s) or network you want to scan in CIDR notation.0/24 IP address range. Find your local IP address and subnet. The syntax is quite straightforward.174”, to find all open ports, services, and MAC addresses on the system.20 basic examples of Nmap command usage.nmap ideal scan technique to hide your IP. The syntax is as shown: $ nmap target-ip.com Nmap scan Options. Here is how to scan an IP range with Zenmap: As shown above, at the “Target” field just enter the IP address range separated with dash: For example 192. It takes an argument of the form : @ : . Document Changelog. Zenmap is the official graphical user interface (GUI) for the Nmap Security Scanner.Nmap scans the top 1000 commonly used ports by default.
How to Use Nmap for Vulnerability Scan?
An administrator may be . Single Port Scan.
Security Tip: Avoid Detection with nmap Port Scan Decoys
Naabu Scan All Ports. As with a normal URL, you may omit : , in which case anonymous login credentials (user: anonymous password: -wwwuser@ ) are . The only Nmap arguments used in this example are -A, to enable OS and version detection, script scanning, and traceroute; -T4 for faster execution; and then the hostname. This default SYN scan behavior is shown in Example 5.To execute an aggressive scan, combine the -A switch with other desired flags, such as -sS or -sU, in the Nmap command. Network administrators may only be interested in hosts running a certain service, while security auditors may care about every single device with an IP address.Nmap, as an online port . By doing this, we managed to be more efficient and perform scans faster than doing full port scan on the whole target range from the beginning. nmap -p- -Pn -sS -A -T4 -iL livehosts.At the risk of offending my friend Dan Kaminsky, I’ll name his Scanrand port scanner as an example of a program that was clearly developed with far more emphasis on neat technical tricks than a user friendly UI. This command will initiate an aggressive scan using SYN scan against the specified target IP address. It requires raw-packet privileges, and is the default TCP scan when they are available.

Common ports
How to use Nmap to scan for open ports
Several device types may be shown, in which case they will be separated with the pipe symbol as in “ Device Type: . Yet it still uses the -p option to select scanned protocol numbers, reports its . “090107” on September 1, 2007). The following Naabu cheat sheet aims to explain what Naabu is, what it does, and how to install it and use it by providing Nabuu command examples in a cheat sheet . Posted on December 27, 2016 June 29, 2023 by admin. The results are piped to a trivial awk command which finds lines containing /open/ and outputs fields two and three for each matching line.Scanning every port of every single IP address is slow and usually unnecessary. Here are some commonly used options:-p-: Scans all ports in the range from 1 to 65535, including both TCP and UDP ports.Example command. we will look at two different ways to take input from command line: using argparse; using optparse; Parsing arguments using argparse. To scan using “-v” option. This technique only hides your source address but remote IPS / IDS always record and logs scan.To query the WHOIS records of a hostname list (-iL ) without launching a port scan (-sn). The-p option is used to instruct nmap to scan the specified port(s) To check if the telnet port is open: The Nmap Documentation portal is your reference for digging deeper into the options available. For example, the following command scans the 10. Types of Port Status: Open: The open status means that the given port is open and is actively running . In this tutorial we will learn taking input from command line while running the script, rather than hardcoding the values in the script. Then select the scan Profile (e. -p [1-n]: Scan .Recall that -T4 causes Nmap to go faster (more aggressive timing) and -F tells Nmap to scan only ports registered in nmap-services. Naabu Fast Scan, Verify, Nmap Services. Keep in mind this cheat sheet merely touches the surface of the available options.1 IP as as a zombie to scan host – 192.IPv6 Scanning (. This isn’t technically a port scan, since it cycles through IP protocol numbers rather than TCP or UDP port numbers. A SYN/ACK indicates the port is listening (open), while a RST (reset) is indicative of a non-listener.txt -oA fullscan-p- : This scans all ports .

It uses port 1234 on 1. Find active hosts, scan for the opened ports, determine the remote operation systems, detect and bypass firewalls. Following example, uses an an idle scan technique.Führen Sie den folgenden Befehl für einen Betriebssystem-Scan aus: # nmap -O 5.
IPv6 Scanning (-6)
Just call the script with “–script” option and specify the vulners engine and target to begin scanning.
Windows
SYN scan may be requested by passing the -sS option to Nmap. Basic Port Scan. Sie können diesen Befehl folgendermaßen . Similarly, you can specify a hostname to scan for the host: sudo nmap example.txt contains a list of hosts or IP addresses) Disabling cache. Please refer to nmap man . Pour cela, nmap trouve les ports d’une machine distants.
TCP SYN (Stealth) Scan (-sS)
1) Nmap command for scanning a single host.Nmap is very powerful when it comes to discovering network protocols, scanning open ports, detecting operating systems running on remote machines, etc. nmap -sV –script nmap-vulners/ If you wish to scan any specific ports, just add “-p” option to the end of the command and pass the port number you want to scan.These are further described in the section called “Device and OS classification (Class lines)”. Toggle navigation.Nmap runs centered around a command line similar to Windows Command Prompt, but a GUI interface is available for more experienced users.Using the “–script=” option allows specific scripts to be loaded into Nmap and executed after the port scan has completed. Sample outputs: Fig.The Nmap scan report displays the host status and latency. Combining the “banner. For example: nmap -A -sS target_ip_address.This is a shame, since that is the one TCP scan that works over all networking types (not just .Il est capable de explorer et découvrir des machines sur le réseau et énumérer les services réseaux présents sur un PC distant.Example: nmap -sS 192.How to Use Vuln. For example, the port # 22 is often used by ssh service such as OpenSSH server or the port # 80 is often used by a web server such as Apache. They can navigate through firewalls, routers, IP filters, and other .
Nmap Command in Linux with Examples
Forge a SYN packet from the zombie and send it to the desired port on the target. Please refer to the article Port Scanning to learn more about it. A representative Nping execution. is the name or IP address of a vulnerable FTP server.Fundamentally, an idle scan consists of three steps that are repeated for each port: Probe the zombie’s IP ID and record it. It is one of the essential tools used by network administrators to troubleshooting network connectivity issues .
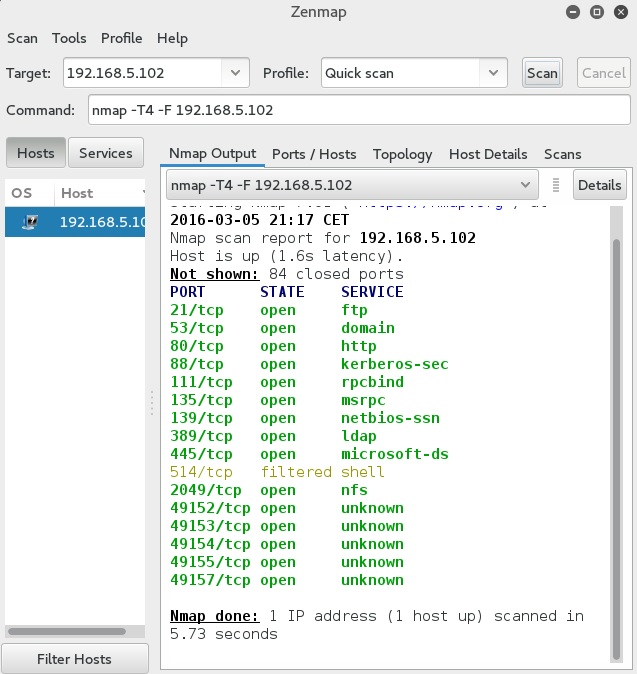
Here is a concrete example of searching 4096 IPs for web servers (port 80 open): nmap -Pn -p80 -oG logs/pb-port80scan-%D. Nmap can scan a target domain or IP address for all vulnerabilities in the default script library for the “vuln” category with the appropriately named Vuln command: sudo Nmap . In this we are performing a scan using the hostname as “geeksforgeeks” and IP address “172. Nmap (Network Mapper) is a free and open source utility for network discovery and security auditing. This is only necessary if you have problems with broadcast scripts or see the WARNING: Unable to find appropriate interface for system route to message. For example; $ nmap 192. Nmap scan the network, listing machines that respond to ping.Nmap (Network Mapper) est un utilitaire opensource pour faire un scan et balayages de ports. nmap -p 1-65535 -sV -sS -T4 target.
- Nintendo Switch Am Billigsten _ EA SPORTS FC 24
- Noragami Anime Ost – Noragami (TV Series 2014
- Nintendo 3 Ds Xl Preis : Nintendo Ds, Konsole gebraucht kaufen
- Nikotinsäure Präparate _ Lipoprotein(a): wann messen, wie behandeln?
- Nikon Coolpix L810 Anleitung : Nikon Coolpix L820 (Digitalkamera) Test
- Nintendo Ds Emulator Free : Die 12 besten Nintendo DS-Emulatoren für Windows
- Nokia Handy C5 _ Werkseitig zurückgesetztes Nokia C5
- Nintendo Switch Let’S Sing 2024
- Nissan Leaf Steckdosenladen _ Elektrisch fahren ohne Steckdose: Nissan zeigt, wie’s geht
- Ninjago Videospiele Kostenlos | The LEGO NINJAGO Movie Video Game
- Normale Größe Für Bettwäsche , Bettwäsche