How To Check Sql Injection Vulnerabilities
Di: Samuel
SQL Injection: A Detailed Guide for WordPress Users
Many techniques such as UNION attacks are not effective with blind SQL injection vulnerabilities. The first step towards achieving a successful SQL injection attack is to detect vulnerabilities. SQL and Sysadmins.Where is the SQL injection vulnerability in given code and how to exploit it using python and sqlite.
What is SQL injection (SQLi)?
This creates a vulnerability that can destroy your system from within. For instance, when filling in a web form.From the various examples listed in this article, SQL injection proves to be a critical vulnerability that can exist in a system. Of course, some tools can automate the process, but it’s better to understand how detection can be done manually. A ‘blind’ SQL injection vulnerability is when the attacker can send commands to the database but they don’t actually see the database output. Stacked Query Testing. Perform a denial-of-service.
SQL Injection Detection
According to the Open Web Application Security Project, injection attacks, which include SQL injections, were the third most serious web application security risk in 2021.SQL injection is an attack that takes advantage of poor database integration infrastructure and lackluster user input validation. Injection flaws are easy to discover when examining code, but more difficult via testing.
What is an SQL Injection Attack? See Examples
SQL Injection is one of the many web attack mechanisms used by hackers to steal data from organizations. Form based sql injection is conceptually the same, the only difference being the rogue SQL statements are inserted via a POST request on the form submit rather than the HTTP GET parameter.SQL Injection in Web Apps. It is used to detect vulnerabilities in an application that could be exploited by malicious users to gain access to sensitive data. The database recognizes the malicious query as if it’s any other, and returns the information that the attacker requested.But in order to understand injection/vulnerabilities, we need to take a step back and review that basic SQL knowledge first, which you may not have needed until this point in your role as a sysadmin.Web vulnerability scanners such as Veracode, Checkmarx, Invicti, Acunetix, and others are an effective way to check whether your website and web applications are vulnerable to JSON injection attacks. Username / Password forms are a well known point of attack. Typical techniques include using a single quotation mark or apostrophe for delimiting literal strings, two dashes for a comment, and a semicolon for the end of a statement. CI-driven scanning More proactive security – find and fix vulnerabilities earlier. One type of blind SQL injection is Boolean-based, where .

Return to Burp and ensure Intercept is on in the Proxy Intercept tab. We want to get access to the administration area of the website. This allows attackers to modify the ways applications use queries to the database.A SQL injection is a vulnerability that affects applications by using malicious SQL codes to manipulate the database. In addition, there are some situations where only manual testing will allow in-depth analysis.
What Is SQL Injection? How to Prevent SQLi Attacks
We gonna need the below functions: def get_all_forms(url): Given a `url`, it returns all forms from the HTML content. Now send a request to the server. Load 7 more related questions Show fewer related questions Sorted by: Reset to default Know someone who can answer? Share a link to this .
CA3001: Review code for SQL injection vulnerabilities
SQLi attacks have the potential to access sensitive information such as email addresses, usernames, passwords, and credit card details stored in your database.I’m creating a basic website with a login screen for a project and I want to test it for some basic sql injection vulnerabilities. SQL Injections have been the number one critical vulnerability on the OWASP Top 10 list since its first edition in 2010 and they are expected to hold that spot in the future. To perform a SQL injection attack, an attacker inserts or injects malicious SQL code via the input data of the application. SQL injection is a hacking technique that attempts to pass SQL commands through a web application for execution by a backend database.
SQLMap: Comprehensive Guide to Detecting and Preventing SQL Injection
DevSecOps Catch critical bugs; ship more secure software, more quickly. SQL injection allows the attacker to read, change, or delete sensitive data as well as execute administrative operations on the database. This is because they rely on being able to see the . For those who don’t know SQL injection is a web hacking technique where the attacker inserts malicious code into an SQL statement.SQL injection (or SQLi) is one of the most widespread code vulnerabilities.Testers should check every field individually to identify the vulnerable parameters.Blind SQL injection occurs when an application is vulnerable to SQL injection, but its HTTP responses do not contain the results of the relevant SQL query or the details of any database errors. The request will be captured in the Proxy Intercept tab.
They implement most of the web application testing techniques discussed above and allow you to apply those techniques .
Scan for SQL Injection Online
Injection Flaws
Blind SQL Injection Vulnerabilities This occurs when an application is susceptible to SQL injection, but it does not directly expose the results of injected SQL queries.SQLmap supports pretty much every major database in use today and can detect and exploit most known SQL injection vulnerabilities.
How to Detect SQL Injection Attacks With Extended Events
In this example by clicking the Submit button. One way to test an application for SQL injection vulnerabilities is to .The Acunetix security scanner lets you detect many variations of SQL injection vulnerabilities from a simple online, cloud based solution without having to install any software on premise.SQLMap is an open-source tool that automatically finds and exploits SQL injection vulnerabilities. If attackers can pull off an SQL injection, they can gain access to the database. However, companies around the world often make horrible mistakes when it comes to composing . SQL Injection attacks are such a common security vulnerability that the legendary xkcd webcomic devoted a comic to it: Exploits of a Mom (Image: xkcd) Generating and executing SQL queries is a common task. You can use SQL to delete records .Attack surface visibility Improve security posture, prioritize manual testing, free up time. This phase marks a . For example, in a financial application, an attacker could use SQL Injection to alter balances, void transactions, or transfer money to their account. The main goal of a SQL injection attack is to manipulate the data in the . Injection vulnerabilities exist when information provided by users of the application is not properly validated or sanitized before it is used.WooCommerce: The popular WordPress plugin fixed an SQL injection vulnerability that exposed 5 million sites to data theft. The goal of SQL injection testing is to identify and prevent malicious . Use of Vulnerability Management tools, like AVDS, are standard practice for the discovery of this vulnerability.SQL Injection Vulnerabilities are also very prevalent in the form fields of web applications. Deep Scan technology lets Acunetix fully scan complex web applications, including applications which feature rich JavaScript and HTML5 content. We could add: “ ‘ or sleep(10) ” and this will do what it seems like. We need to find table names to be able to . It’s rather like communicating with the spirit world via tapping. Instead, the technique relies on detecting either a delay, or a change in the HTTP response, to distinguish between a query resolving to TRUE or FALSE.
What is a SQL Injection Attack?
We have identified the SQL injection vulnerability, now let’s proceed with the attack.
How can I detect SQL injection vulnerability with Python script
Since SQL injection is all about user inputs, we will need to extract web forms first.
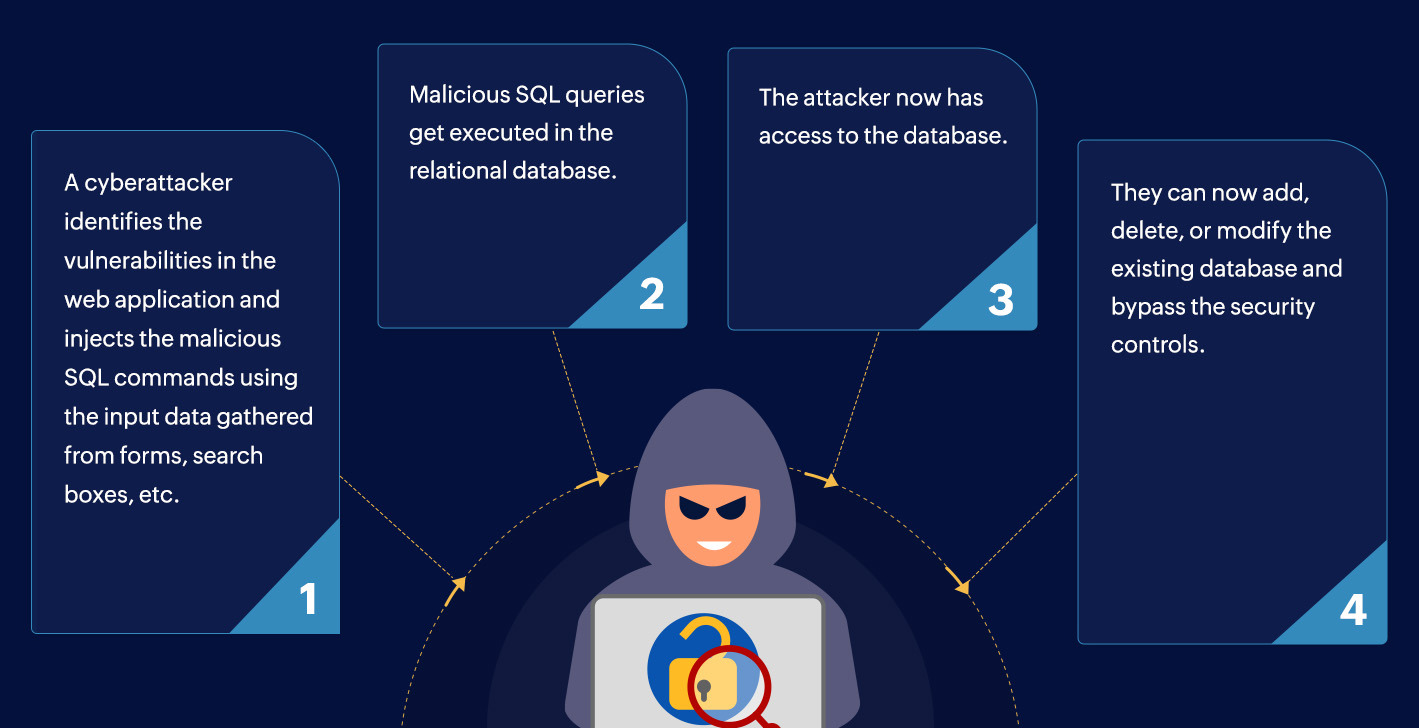
It is very easy. Malicious SQL instructions injected directly into the system’s SQL database through user-facing input fields can take over a system. This vulnerability can enable attackers to view, modify, or delete data they shouldn’t access, including information of other users or any data the application can access.
SQL injection Cheat Sheet for 2024
Visit the web page of the application that you are testing.An SQL Injection is a code injection technique that attackers use to exploit vulnerabilities in a website or application’s database layer. As of writing this post (2021), Injection is listed as the . To exploit a SQL injection flaw, an attacker needs to find a parameter that the web application passes through to a database interaction.An attacker can enter a string that gets read by the database to return matching results. An attacker can then embed malicious SQL commands into the content of the parameter, to trick the web application to forward a malicious . SQL injection occurs when an attacker sends a malicious request through SQL queries to the database. Blind SQL injection is used where a result or message can’t be seen by the attacker. If SQL injection is possible, smart attackers can create user input to steal valuable data, bypass authentication, or corrupt the records in your database. Not only can attackers exploit it to reveal user or customer information, but it can also be used to corrupt the entire database thus bringing the whole system down. In a SQL injection, attackers can: View and modify personal data.SQL Injection Detection.
DVWA SQL Injection Exploitation Explained (Step-by-Step)
Application security testing See how our software enables the world to secure the web.SQL Injection – Is a particularly widespread and dangerous form of injection.Understanding Injection Vulnerabilities.

We’ll encapsulate these invaluable insights and underscore the paramount significance of SQL injection prevention in today’s dynamic cybersecurity landscape.Injection flaws occur when an application sends untrusted data to an interpreter. This means that not only can an attacker read this information, but they .SQL Injection is one of the top 10 web application vulnerabilities. All you want to do is just install an open source software named sqlmap. According to sqlmap’s GitHub page, “ sqlmap is an open source penetration testing tool that automates the process of detecting and exploiting SQL injection flaws and taking over database .SQL vulnerability assessment (VA) is a service that provides visibility into your security state, and includes actionable steps to resolve security issues and enhance your database security. I am not asking about how to detect them on someone else’s server to exploit them.
Using Burp to Detect SQL Injection Flaws
An SQL Injection vulnerability could allow the attacker to gain complete access to all data in a database server. This is not good. In simple words, SQL Injection means injecting/inserting SQL code in a query via user-inputted data.SQL injection is one of the most dangerous vulnerabilities for online applications.In this tutorial, i will show you how to check SQL injection vulnerabilities in your website in windows. Penetration testing .Automated exploitation using sqlmap: Now, let us discuss how we can use sqlmap to automate SQL Injection detection and exploitation.SQL injection (SQLi) is a cyberattack that injects malicious SQL code into an application, allowing the attacker to view or modify a database. Such actions may result in permanent changes to the application’s functionality . It can help you: Meet compliance requirements that require database scan reports; Meet data privacy standards ; Monitor a dynamic database .

It can occur in any applications using relational databases like Oracle, MySQL, PostgreSQL and SQL Server.SQL injection testing is a process of inserting data into an application to verify that user-controlled SQL queries can be run on a database. SQL also lets you alter data in a database and add new data. Sanitize your input, but test to verify your mitigations are . It occurs when a user adds untrusted data to a database query. Is there a way to find every occurance of mysql_query() without opening every page and doing a ctrl+f? The database will then run whatever SQL commands it was given by the user.SQL injection attacks, also called SQLi attacks, are a type of vulnerability in the code of websites and web apps that allows attackers to hijack back-end processes and access, extract, and delete confidential information from your databases.Understanding Python SQL Injection. It will tell the database server to take a 10-second nap and all responses will be delayed.A Statista report shows that SQL injection is the world’s leading source of web application vulnerabilities. Although SQLi attacks can be damaging, they’re easy to find and prevent if you know how. Similar to our ‘ or 1=1 condition, we can tell the server to sleep. Attackers must rely on the application’s behavior to infer whether their injected statements are true or false. The primary failure of VA in finding this vulnerability is related to setting the proper scope and frequency of network scans. MOVEit: In May 2023, the Cl0p ransomware gang used a SQL injection vulnerability in the . It is vital that the broadest range of hosts (active IPs . In the stacked query method, testers complete an SQL statement and write a new one. I’m using a form to read a username and a password from a user and this line of PHP code to find their info in my database and print it to them:
Exploiting SQL Injection: a Hands-on Example
In this final section, we’ll recap the pivotal moments of your voyage – from the inception of SQLMap installation to the detection of SQL injection vulnerabilities. For SQL injection .
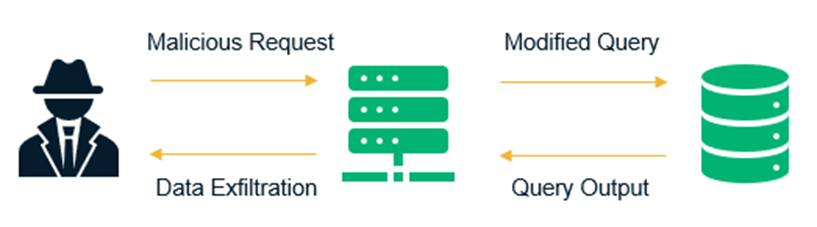
Blind Injection. It is perhaps one of the most common application layer attack techniques used today.An SQL injection attack can execute malicious SQL commands, compromising the security and integrity of your application. BillQuick: Cybercriminals exploited a blind SQL vulnerability in the popular billing platform to spread ransomware.
A ‘classic’ SQL injection vulnerability is one where unfiltered user input lets an attacker send commands to the database and the output is sent back to the attacker.

SQL injection cheat sheet
An SQL injection is a security flaw that allows attackers to interfere with database queries of an application.
Auditing for SQL Injection Vulnerabilities
If you were interviewing a Sysadmin for a job setting up a new Windows Domain Server and some file servers and they said: . In the case of Cross-site Scripting, this would mean that a field allows the entry of JavaScript which is then re-displayed to the client. sqlmap is an open source penetration testing tool that automates the process of detecting and exploiting SQL injection flaws and taking over of database .Along with these, we will also use the –dbs and -u parameter, the usage of which has been explained in Step 1. Let’s assume that we don’t know the structure of the database or that the administrator used non-default naming/prefixes when installing WordPress. Luckily for us, I’ve already written a tutorial about extracting and filling forms in Python. For more information, see SQL . SQL Injection vulnerabilities can have very serious consequences for the business, such as sensitive information theft (for example, credit .Another technique we can use for blind SQL injection, the one where no data is sent back to the screen is to inject other hints. When an attacker identifies an injection vulnerability, they are able to pass SQL instructions in that string to the database.
Injection Prevention
Using SQLMAP to test a website for SQL Injection vulnerability: Step 1: List information about . Injection flaws are very prevalent, particularly in legacy code, often found in SQL queries, LDAP queries, XPath queries, OS commands, program arguments, etc.SQL Injection Scanner: Enter Acunetix. If you understand how these attacks work, you’ll be better equipped to prevent them. Here are some of the testing methods to help identify SQL vulnerabilities: 1.Is there a way to find SQL injection vulnerabilities? Note: I am asking how to find them on a server you are in control of so you can fix them. To perform SQL Injection, a malicious user first tries to find a place in .How to Fix SQL Injection Vulnerabillities. You can use it to test web applications for SQL injection and gain access to a vulnerable database.
- How To Fix Outlook Offline – 7 Ways to Troubleshoot If Outlook Is Not Receiving Emails
- How To Analyse Narrative Perspective
- How To Get All Alcremie Forms : Pokémon Sword & Shield
- How Old Is Enola Holmes – Enola Holmes
- How To Clear Hsts | How to reset HOSTS file to default on Windows 11
- How To Choose The Right Printing Ink
- How To Change Cisco Jabber Profile Picture?
- How Much Is Rivaldo Worth? , Southwest Points Value Calculator
- How To Fix Jw Player _ Adding Captions & Subtitles to JW Player 7 Videos
- How To Charge Battery While Simultaneously
- How To Cite Quotes _ MLA Titles
- How Much Protein Is In Millet , Calories in Millet (Cooked) and Nutrition Facts
- How To Center A Div In Css? _ How To Center an Image