How Do I Disable Network Level Authentication (Nla)?
Di: Samuel
Disabling and enabling NLA is quite easy. To enable preset firewall rules of RemoteDesktop, use the following PowerShell command: Enable-NetFirewallRule -DisplayGroup ‚Remote Desktop‘ or from CMD, append powershell. — Windows Components. Click Start and select the Settings icon. there are also options to use powershell script or change registry remotely to disable this option: The DisableNLA run command in Azure is actually a registry code that turns off the network level authentication on the remote Azure VM. If you’ve determined that NLA is ineffective for your business context, you can disable it using PowerShell by following these steps.When you connect remotely using Remote Desktop to any Windows computer.
The remote computer requires Network Level Authentication
Enter your computer name and click Ok.

If this fails to connect you may be out of luck. It appears even when Network Level Authentication (or NLA) is enabled on the computer.1 mentions it in the work in progress section: Network Level Authentication is half-way done (TLS works, but NTLM authentication is partially implemented) Release notes of the following versions do not even mention it. I would much rather not do that for many reasons, however it’s never been clear what traffic I’ll .Fix: Remote Computer Requires Network Level Authentication (NLA) [Tutorial]Sometimes Windows won’t let you connect to a remote computer, citing an issue with. No matter what . Click Windows and R, type sysdm. I don’t know which of these settings would cause it to falsely report that the far side server needed to have NLA disabled when it already was configured that way. Here, scroll down to choose “Remote Desktop” from the left panel. Without NLA, an attacker could potentially access the remote desktop by guessing or brute-forcing the username and password. Computer configuration > Administrative Templates > Windows Components > Remote Desktop Services > Remote Desktop Session Host > Security. Locate the ‘Require user authentication for remote connections by using Network Level Authentication’ and set . (see screenshot below) B) Click/tap on Confirm, and go to step 5 below. Disables Network Level Authentication (NLA): You can use this script to disable NLA .
What networking exactly is required for NLA? : r/sysadmin
You can press the Windows and the Pause/Break . In this article, we will show you some ways to fix the above problem First access your VPS through the Console. 0 votes Report a concern.The remote computer that you are trying to connect to requires network level authentication (NLA), but your windows domain controller cannot be contacted to perform NLA.You can use the same steps to disable the NLA on Windows 11 as well. To Disable Remote Desktop Connections. Disable Network Level Authentication. In the Remote tab, in the remote Remote Desktop group you will have to uncheck “ Allow remote connections only from .Can I Use Scripts to Disable Network Level Authentication? You are aware of how much we at Gorelo adore automation and scripting. Following are the steps to enable NLA via Remote Desktop settings: Step 1: With the help of the “Win + I” key combination, access Windows Settings and tap System. If you are an administrator on the remote computer, you can disable NLA by using the options on the remote tab of the System Properties dialog box. You will now see the System Properties window.Network Level Authentication (NLA) is an authentication tool used in Remote Desktop Services (RDP Server) or Remote Desktop Connection (RDP Client), introduced in RDP 6.Method 01: Disable NLA Using Properties.exe in the beginning: powershell. Under Related settings, select Advanced System Settings.
Enable Network Level Access For Windows RDP
Wenn Sie die Remoteverbindung sichern möchten, müssen Sie die Netzwerkauthentifizierung (Network Level Authentication, NLA) aktivieren. To do this, follow the given steps: Step 1: Open the System Properties dialogue box on the remote computer. Windows 10 or Windows Server 2016 and Windows 8 or Windows Server 2012 without RD Session Host Role. Terminal servers running Windows 2003 Server without SP1 or earlier do not support a clients’ ability to authenticate the terminal server . 1] Go to ‘Run’ and type ‘ sysdm. Uncheck “Allow connections only from computers running Remote Desktop with Network Level Authentication (recommended)”. Allow connections only from computers running Remote Desktop with Network Level Authentication.Require user authentication for remote connections by using Network Level Authentication: Enabled; Set client connection encryption level: Enabled.msc and press Enter to launch the Local Group Policy Editor. — Remote Desktop Services. Disabling NLA using Registry Step 1. Unter dem Reiter Security deaktivieren Sie die Option Verbindungen nur von Computern zulassen, auf denen Remote Desktop mit Network Level Authentication läuft (für maximale Kompatibilität stellen Sie sicher, dass Security Layer auf Negotiate gesetzt ist).This guide describes how to disable Network Level Authentication on various versions Windows Server with or without RD Session Host Role. A) Click/tap on Remote Desktop on the left side, and turn off Enable Remote Desktop on the right side.cpl, and enter.It allows users to secure remote connections with an additional layer of authentication. Press WIN + R and then .On the left pane, select Run Command under Operations. Note: These steps do not apply to Windows Server 2012 and 2016 with the RD .But NLA (Network Level Authentication) is still not supported. On the Windows Settings page, select System.reg file into Microsoft Group Policy GPO ; How to enable .Allow connections only from users running Remote Desktop with Network Level authentication The second option is recommended in the dialog, but even the help does not really explain the risk in choosing the first one. You are going to modify the key named ‘Security Packages’. Here, you’ll find the Require devices to use Network Level Authentication to connect (Recommended) . —- Remote Desktop Session Host. Under the File menu click “Connect Network Registry.To disable NLA remotely: Open regedit on another computer on the same network. It allows you to easily troubles.This article will cover what network level authentication is for, how it’s used, and how to enable and disable network level authentication in a specific environment.The remote computer that you are trying to connect to requires Network Level Authentication (NLA), but your Windows domain controller cannot be contacted to perform NLA. Move to remote tab.“The remote computer that you are trying to connect to requires network level authentication (NLA), but your windows domain controller cannot be contacted to perform NLA. Open a Run dialog by pressing Win + R. These errors might . NLA is sometimes called front authentication as it requires the connecting user to authenticate themselves before a session can be established with .Follow the steps carefully.By default, you might find RDP firewall rules disabled which prevent RDP connections to the server.Network Level Authentication (NLA) wird verwendet um Remote Destop Services wie Windows RDP und Remote Desktop Connection (RDP Client) zu authentifizieren. Not via Intune today to my knowledge.Klicken Sie auf Tasks und wählen Sie Eigenschaften bearbeiten.
Remote Desktop Network Level Authentication
If you are an administrator on the remote computer, you can disable NLA by using the options on the Remote tab of the . Navigate to this Key: . I hope the information above is helpful.If you want to ‘blanket disable’ NLA then group policy is the way to go; Computer Configuration > Administrative Templates > Windows Components > Remote Desktop Services > Remote Desktop Session Host > Security.
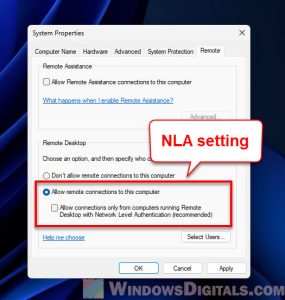
With that environment, the only way to RDP to the remote office is to disable NLA.Is there another way I can enable NLA while running Windows Pro. The first is located at: HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Lsa. NLA is a Remote Desktop Services (RDP Server) feature requiring the . Scroll down and click About.Jul 27, 2022, 9:37 AM. This is the default setting. Download PSExec from TechNet. If you are an administrator on the remote computer, you can disable NLA by using the options on the Remote tab of the System Properties dialog box.Getting “the remote computer requires network level authentication windows 10” even though the remote machine has NLA disabled.
How to Disable Network Level Authentication
To Enable Remote Desktop Connections. Teilweise wird dafür auch der Begriff Front Authentifizierung verwendet.
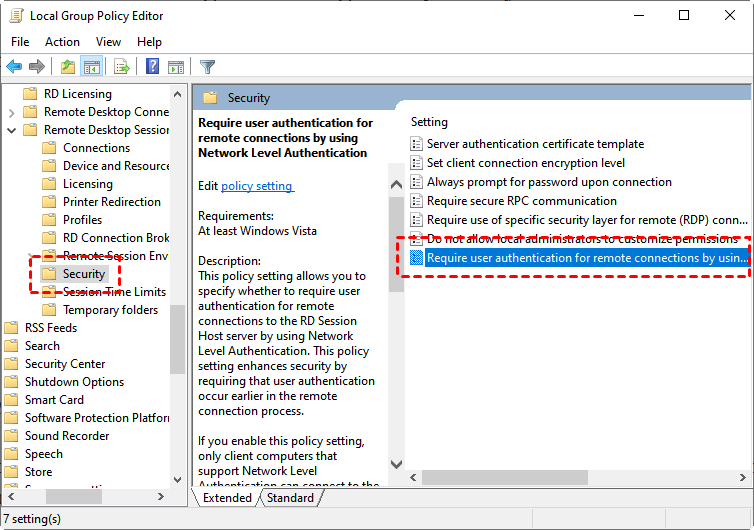
Run the code below updating the following values. First, it is important to distinguish between enabling NLA on the PSM server itself and enabling NLA on the target servers. \\VMNAME – The name of the machine on which you want to disable NLA. Then, expand the Remote Desktop drop-down.Go to Control Panel / System and Security / System and select Remote Settings.Open the Group Policy Editor by typing ‘gpedit’. Jason Sandys 31,146 Reputation points • Microsoft Employee 2022-03-11T18:36:30. There are two keys to change. Disable NLA on the Remote Computer.0 in Windows Vista. We fully support enabling NLA on the target servers. Navigate to the following: Computer Configuration. Add ‘tspkg’ to the listing of security packages. I know we were investigating opening up the Settings Catalog to Windows Pro but I don’t think that’s .Disabling Network Level Authentication (NLA) can potentially introduce security risks, as it removes an important layer of authentication and can make remote desktop connections more vulnerable to unauthorized access. Network Level Authentication (NLA) for Remote Desktop Connection is an optional security feature available in Windows Vista and later.
What is network level authentication?

– Administrative Templates.If you want to secure remote connectivity, you need to enable Network Level Authentication (NLA). hi @Gabriel Barreto.Network-level authentication authenticates Remote Desktop services, such as Remote Desktop Connection (RDP Client) and Windows RDP.If you are an administrator on the remote computer, you can disable NLA by using the options on the Remote tab of the System Properties dialog box.Disable NLA from local group policies/administrative template/Windows Components/Remote Desktop Services/Remote Desktop Session Host/Security again. Scroll down in the left pane to find the newly added server.msc MMC snap-in. You can connect via console and disable the option NLA on system properties -> remote.cpl ’ and hit the ‘Enter’ button. Encryption Level: High Level; Users intended for remote access are added to the respective remote desktop PC’s user group Remote Desktop Users, using the lusrmgr.How To Enable Network Level Authentication In Windows 11/10 [Tutorial]Windows’ remote access technology is quite incredible. As for FreeRDP, only the release notes of v0.From the second link in @jessevas comment above, the group policy option is:.Step 4: Navigate to and modify the registry keys. (see screenshot below) 4.
What is Network Level Authentication (NLA)?
VMNAME\ADMIN_ACCOUNT . It will redirect you to system properties.
Disable NLA Network Level Authentication
In the other direction, the only open port from my desktop is 3389 to those servers. When NLA is enabled, remote connections pre-authenticate to the remote system when the RDP client connects before displaying a full remote session. The Network security: LAN Manager authentication level setting determines which challenge/response authentication protocol is used for network logons.
PowerShell
Disabling NLA using the group policy editor can be very useful especially if you are blanket disabling. If enabling Network Level Authentication (NLA) on the remote computer doesn’t solve the problem, you can try disabling it. It’s also referred to as front authentication because it requires the end user to enter their credentials to make the session work. Report abuse Report abuse. When NLA is disabled, the Windows username .Wenn Sie Ihrem System Remotedesktopkonnektivität erlauben, öffnen Sie tatsächlich einen Port auf Ihrem System, den andere Systeme in Ihrem lokalen Netzwerk verbinden können. You need to go to the Remote tab. Let’s dive in! What is network level authentication (NLA) used for? Before you can start a remote desktop session, the user will need to authenticate themselves – . On the PSM server we require the NLA to be disabled to allow the PSM to provide full isolation . —– Security. This choice affects the authentication protocol level that clients use, the session security level that the computers negotiate, and the authentication level that servers . From the list of run commands, select “ DisableNLA . Related Knowledge Base Posts – How to import . The benefit of this is that users need to authenticate themselves to establish remote session. Follow these steps to disable ‘remote desktop network level authentication’ using local group policy editor. To open the search bar and then navigate to PowerShell as the administrator, press the . Go to your control panel-> System and Security; Allow remote access; Enable or disable Network Level Authentication-> OK; Done! Microsoft Disable NLA, Hardening, Hardening Windows Server, Nla.
Remotely disable Network Level Authentication (NLA)

Finally, Apply changes. 2] You are now in the System Properties window.Alternatively, there’s a much easier way to configure the Remote Desktop NLA settings, and here’s how you can do it: In the Settings window, move to System > Remote Desktop.Disable NLA (for Windows system only) Background.Now I am getting a different message: The remote computer that you are trying to connect to requires Network Level Authentication (NLA), but your Windows domain controller cannot be contacted to perform NLA. Dieser Artikel wird darüber sprechen, wofür die Authentifizierung auf Netzwerkebene . I can work out the setting with Terraform automation code for the other four (for detail , take reference in Login to a Virtual Machine using Azure AD Account on Linux), but I’m facing challenges in implementing the last one “Disable NLA ( Network Level Authentication)” through scriptsOn the right pane, find Require user authentication for remote connections by using Network Level .In Windows Server 2008, Network Level Authentication (NLA) is designed to be secure against MITM, and it supports the ability to authenticate the server with either a SSL/TLS server certificate or Kerberos. Using PSM as a jump server eliminates much of the need for NLA. Doubleclick on “Require user authentication for remote connections by using Network Level Authentication”.To facilitate, this, remote office has full access to the Domain Controllers.
- How Did Ada Become Involved In The Peaky Blinders?
- Hotels Vaihingen Stuttgart _ B&B Hotel Stuttgart-Vaihingen in Stuttgart
- How Do I Add Ietc To My New Zealand Tax Return?
- How Do I Play Chords In A Circle Of Fifths?
- How Do I Export A Cropped Video?
- How Do I Install Windows On My Iot Device?
- How Do I Get To Wow? _ How to get to Kul’tiras in dragonflight?
- How Do I Make Perfect French Press Coffee
- How Did Fury Beat Wilder In ‚The Bronze Bomber‘?
- How Do I Contact The Owncloud Technical Support?
- How Do I Add A Stop On Google Maps?
- How Do I Contact Dude Perfect?
- How Do I Know If My Flash Player Is Installed?
- How Do I Convert Mp3 To Mp4? : M4A in MP3 Umwandeln (Online & Kostenlos) — Convertio
- How Are Urban Regeneration Schemes Implemented In Prd Cities?