Honeypot Information Security – Honeypots and Honeynets in Cybersecurity Explained
Di: Samuel
Honeypots und Honeynets können auf verschiedene Arten verwendet werden: Sicherheitsforscher verwenden Honeypot Security und Honeynets, um Arten von Angriffen zu beobachten und zu analysieren und mehr über die Angreifer und deren Angriffsmethoden zu erfahren. Cyber Security. They are designed to mimic likely targets of cyberattacks to detect, log, and warn about attack attempts. honeypot is like any other computer system which contains. Industrial Control System (ICS) is a term that refers to control systems in production, transmission and distribution architecture in Smart Grid. A honeypot technique technology is a trick that is laid down by an IT professional for malicious cyber criminals; . Er enthält „vertrauliche“ Daten und Benutzerinformationen sowie viele Sensoren. Découvrez les stratégies de cybersécurité dénommées honeypot et honeynet.

Toute l’expertise de Panda Security pour protéger et . What makes this security tool different is that Honey Pots and Honeynets are digital network bait, and through deception, they are designed to actually attract intruders. And, as we mentioned before, a honeypot makes it that much easier to spot hacking attempts because they simply don’t receive regular traffic. Ils fournissent des renseignements concernant les vecteurs d’attaque, les exploits et les logiciels malveillants. Honeypots werden eingesetzt, um Informationen über Angriffsmuster und Angreiferverhalten zu . We have both permanent and 12 month contract opportunities available. So, they need . Explore various honeypot concepts, such as the types of honeypots, roles and uses of a honeypot, and how honeypot data analysis is used.Diagrama de un Honeypot.But for normal security researchers, it is an urgent topic how to improve the honeypot mechanism which could not be recognized by attackers, and silently capture their behaviors. The first criterion is based on deployment of the honeypots. While the specific nature and purpose of honeypots vary, they generally fall within two main . With a honeypot, security staff won’t be distracted by real traffic using the network – they’ll be able to focus 100% on the threat. A free, distributed, open-source project to help website administrators track, stop, and prosecute spam harvesters stealing email addresses from their sites. So, you intentionally compromise a computer system to allow the hacker to exploit security vulnerabilities.Rechnernetze und -sicherheit. Obwohl diese komplex sein können und ihre Wartung nicht immer einfach ist, sind die von ihnen erhältlichen Informationen unerlässlich.
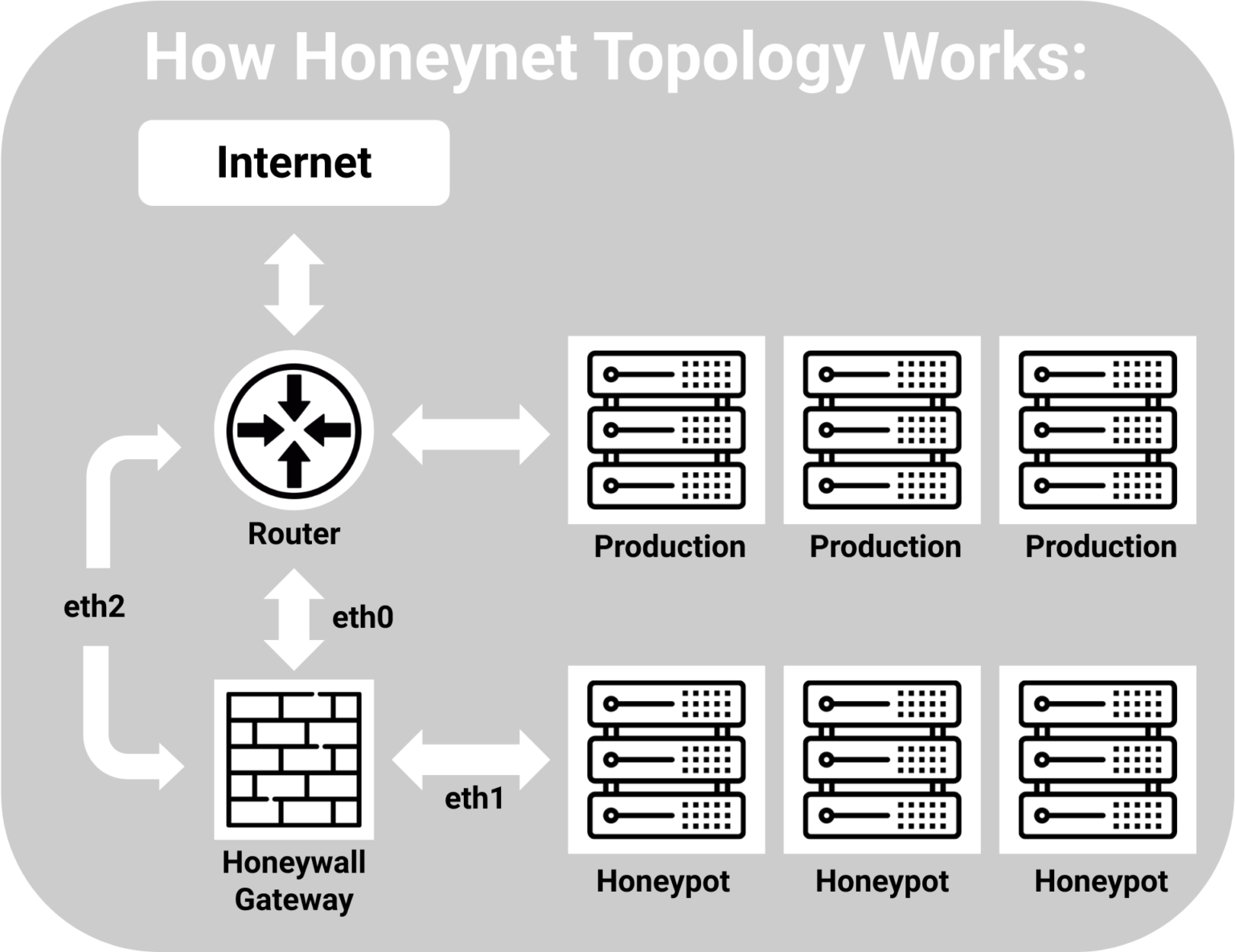
Honeypots can be a powerful tool in understanding the tactics employed by cybercriminals. Unternehmen sollten Mitarbeiter regelmäßig schulen, um deren Awareness – englisch Aufmerksamkeit – für den Ernstfall zu trainieren.Honeypot und Honeynet sind ein Computersystem oder ein Netzwerk zum gezielten Anlocken von Angriffen. One of these technologies is called a honeypot. In actual testing, the honeypot is quickly deployed using Docker technology.A honeypot captures information from the hacker, which can be used to analyze the method of attack, see how the unauthorized intruder interacts with a network, and help cybersecurity professionals shore up vulnerabilities in their systems. There are two groups of honeypots: Production honeypots: Primarily used in the company’s internal network to improve the security of the whole network.A honeypot is a security mechanism used to set traps for attackers. A honey token is data that looks attractive to cyber criminals but, in reality, is useless to them.A honeypot is a trap that an IT pro lays for a malicious hacker, hoping that they’ll interact with it in a way that provides useful intelligence. Information Security Specialist / Information Assurance Consultant – Home . A honeypot is a decoy computer system that appears attractive to an attacker.

Un honeypot, o sistema trampa 1 o señuelo, 2 es una herramienta de la seguridad informática dispuesto en una red o sistema informático para ser el objetivo de un posible ataque informático, y así poder detectarlo y obtener información del mismo y del atacante.In the cybersecurity field, a ‘honeypot’ is a trap set to detect, deflect or study attempts at unauthorized use of information systems. The honeypot lures the hacker to give up information about their identity and how they operate.A honeypot is a computer system which is placed to get. It is not easy to set up and configure and it would be pure insanity to try and do so without an expert on hand; it could backfire and expose the internal network to worse .A honeypot is a cybersecurity tool designed to detect, deflect, and counteract attempts at unauthorized access to computer systems and networks.
What Is a Honeypot & How Is It Used for Security?
Information Security: Honeypots from Skillsoft
There are various client sites across the UK but you will be home-based, with travel as needed to client sites for meetings. I believe this is because; Comparative data is easier when comparing 2 exact images. Salary is between £50,000 – £65,000 and contract rates are market rates. The developed honeypot server application is combined . Honeypots can be used for a variety of purposes, including research, .

Los honeypots tienen vulnerabilidades de seguridad intencionales para atraer a los atacantes. It’s one of the oldest security measures in IT .Pure Honeypot: Dies ist ein komplett imitierendes Produktionssystem von voller Größe, das auf verschiedenen Servern läuft.Furthermore, a honeypot can highlight security flaws in an existing network. Hackers who find this system new will try to exploit it or gain access to it. The honeypot can gather threat information that by default has slipped past traditional preventative solutions—signatureless malware, fileless malware, and zero-day attacks. Honeypot; Cyber Security; Information Security . Host/Network Security is probably easier.
Honeypot
When spam or phishing attempts are sent to the honeypot email, the security team can block the spammers and phishers, as well as their IP addresses, across the network.
HIDDEN Awareness
Honeypot de production Ce type de honeypot, qui est le plus courant, est utilisé par les entreprises pour collecter des informations et des renseignements sur les cyberattaques au sein du réseau de production, notamment les adresses IP, l’heure et la . The word “honeypot” has historically been used to represent a “lure” — on the side of criminals pulling their .
What is a honeypot attack?
Les honeynets offrent un ensemble centralisé de honeypots ainsi que des outils d’analyse. Quicker to clean up/set up additional pots. It can sometimes be difficult to determine if an attack is in progress when sifting through high volumes of traffic on a . In this study, a honeypot based approach for intrusion detection/prevention systems (ID/PS) is proposed.Honeynets et honeypots sont souvent associés pour constituer un plus grand système de détection d’intrusions réseau.
Honey Pots and Honey Nets
A honeypot is a decoy system or resource designed to attract and deceive attackers, allowing security analysts to monitor and study their behaviour. In a database honeypot, a decoy database is generated to attract bad actors who want to hack into the database. Ein Honeypot kommt in der Regel als Ergänzung zu anderen IT-Sicherheitskomponenten wie dem Intrusion-Detection-System (IDS) und Firewalls zum Einsatz und bietet somit eine zusätzliche Kontrollfunktion.Information Security: Honeypots.
Introduction to Honeypots, Honeynets, and Padded Cells
Honeypots intentionally appear to attackers as real computer systems that are affected by vulnerabilities that could be exploited to compromise them.
Was ist ein Honeypot?
Honey Tokens Definition.La plus simple consiste à les classer par finalité, en honeypot de production ou honeypot de recherche.In order to ensure the security of information systems, various systems are used techniques and technologies, including encryption, authorization, firewall, honeypot based systems. In this 12-video course, you will examine strengths and weaknesses of a honeypot and how it is placed in networks.Information Security Awareness. Honeypots are classified in two groups, based on different criteria. Honeypots can also catch internal threats. Database honeypots.) Les pots de miel peuvent vous donner des informations fiables sur l’évolution des menaces.
Honey Tokens: What are they and How are they used?
Digital game-based learning. On this thread, it’s stated that it’s probably a good idea to use a VM for your honeypot. All papers are copyrighted. Por ejemplo, un honeypot podría tener puertos que respondan a un escaneo de puertos o contraseñas débiles. Als Honeypot wird in der Computersicherheit ein Computerprogramm oder ein Server bezeichnet, der die Netzwerkdienste eines Computers, eines ganzen Rechnernetzes oder das Verhalten eines Anwenders simuliert. It is a low-cost security measure that could yield high-value information about your attackers. compromised to get the information about the blackhats.Definition of Honeypots.Vorteile und Nachteile von Honeypots.
What Is a Honeypot? Meaning, Types, Benefits, and More
A cybersecurity honeypot is set up to appear as an actual system on the network. Ein zentraler Vorteil des Honeypottings ist der Gewinn von hochrelevanten Daten. Informationssicherheit spielend einfach.
What Are Honeypots? Types, Benefits, Risks, and Best Practices
CRC Press, Feb 3, 2011 – Computers – 340 pages. Honeypots: A New Paradigm to Information Security.A honeypot is a controlled and safe environment for showing how attackers work and examining different types of threats. This paper expands on the work of two SANS. On your end, you are keen to study the attacker’s patterns and thus use the newly acquired knowledge to influence the security architecture of your digital product. (Bild: Pixabay / CC0 ) Der Begriff Honeypot lässt sich mit Honigtopf ins Deutsche übersetzen. In this paper, we proposed a web-based honeypot in IPv6 network environment with the main advantage of measuring the security situation awareness with SSI. Looking for a step by step process so any NEW researchers can get it the OS up and .A honeypot is a detection tool rather than a preventative solution; it works best when paired with endpoint security, an introduction detection system, and/or SIEM. Die größte Schwachstelle für Cyber-Angriffe ist der Mensch. The actual setup you use can be relatively straightforward or complex, depending on the kind of activity you are trying to study. Generally speaking, a “honey” asset is a fake IT resource created and positioned in a system or network to get cyber criminals to attack it.
¿Qué es un honeypot?
They are easy to use, but provide . These systems .This article describes a security tool and concept known as a Honey Pot and Honeynet. Following a strong theoretical foundation, case . There are two primary types: .
Cons of using a honeypot network.Tip 4: Make the Honeypot or Honeynet Resemble an Actual Network. The main aim here is to get maximum information about the blackhats by giving them full access to penetrate the security system and infiltrate it [ 8 ]. They could be hardware- and software-based, and are important tools created to gather . directories, drives in it . This network-attached system is used as a decoy to distract cyber attackers from their real targets. Online, Self-Paced.Security Information And Event Management, Security Orchestration Automation And Response, Honeypot, Keamanan Cyber, Keamanan Informasi Abstract Informasi merupakan aset yang sangat berharga bagi suatu organisasi atau perusahaan karena merupakan salah satu sumber daya strategis dalam meningkatkan nilai bisnis. It’s crucial for your security to keep your honeypot .

Dans le jargon de la sécurité informatique, un honeypot (en français, au sens propre « pot de miel 1 », et au sens figuré « leurre ») est une méthode de défense active qui consiste à attirer, sur des ressources ( serveur, programme, service), des adversaires déclarés ou potentiels afin de les identifier et éventuellement de les .
Honeypots and Honeynets in Cybersecurity Explained
SCADA security using SSH honeypot. They could find a way to breach your private network and cause damage there, or they might even threaten physical violence.
Security Honeypot: 5 Tips for Setting Up a Honeypot
Honeypots are widely used in network security.Ainsi, les pots de miel permettent d’affiner et d’améliorer d’autres systèmes de cybersécurité.
Qu’est-ce qu’un pot de miel
While the attacker is attacking the honeypot under the impression that it is a worthwhile system to control, they can be observed by security personnel who can then attempt to trap and control the attack. These decoys can produce computer-generated or real operating system settings.Honeypot Classifications. A well-rounded, accessible exposition of honeypots in wired and wireless networks, this book addresses the topic from a variety of perspectives.
Industrial Control Systems Honeypot: A Formal Analysis of Conpot
A cybersecurity honeypot is a decoy security mechanism designed to attract cyber attackers so that security researchers can see how they operate and what they might be after. Strafverfolgungsbeamte nutzen Honeypot Security und .A honeypot is a security mechanism designed to lure attackers in a specially crafted virtual trap. If the intruders find out that they were tricked with a honeypot, they could retaliate.Pros of using a honeypot network. Joshi, Anjali Sardana. The honeypot, typically isolated from the organization’s primary production environment, serves as bait to lure attackers into engaging with the . In this way, honey tokens are similar to honeypots.It can find attacks, delay attacks, and play the role of defense against attacks. A honeypot is a system that is designed to lure in attackers and then track or monitor their activities.
What is a Honey Pot? [updated 2021]
Los puertos vulnerables podrían dejarse abiertos para atraer a los atacantes al entorno del honeypot, en lugar de la verdadera red en .
Honeypots in Cybersecurity: Meaning, Benefits, & Implementation
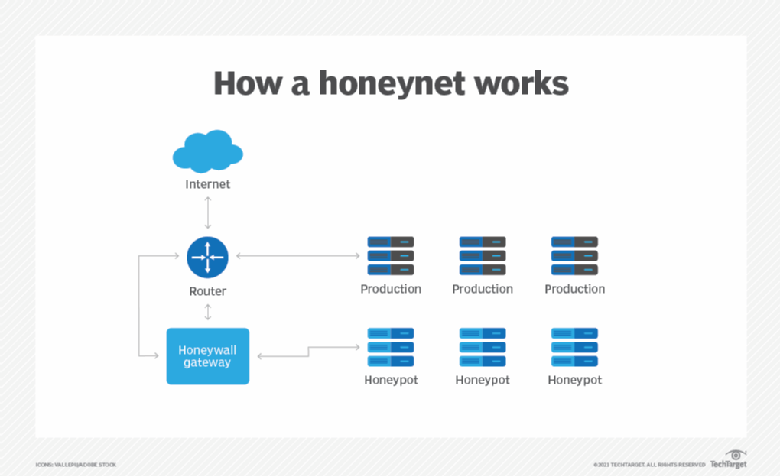
These honeypots can be used .What is a honeypot in network security? Honeypot cybersecurity involves connecting a fake asset to the internet—or even within an organization’s internal network—and enabling hackers to gain access to it.The research honeypot is designed to gain information about the blackhat community and it does not add any direct value to the organization, which has to protect its information . Als Scheinziele sind sie Fallen für Hacker und Cyberkriminelle. Key concepts covered .In the world of computer security, there are a lot of different terms and technologies that can be used to protect systems and data.In cybersecurity, a honeypot is a security tool that can help computer systems defend against cyber attacks in unique ways. The cybersecurity team then uses this information to detect and identify other cyber attacks.Information Security Systems Design Using SIEM, SOAR and Honeypot Muhammad Hafiz1, .The honeypot technique technology works by creating ploys or deception traps that mimic certain system assets throughout the structure.

ISSN: 2614-6754 (print) ISSN: 2614-3097(online) Halaman 15527-15541 Volume 6 Nomor 2 Tahun 2022 Jurnal Pendidikan Tambusai 15528 INTRODUCTION Information security has three aspects, . La característica principal de este tipo de . Es handelt sich um ein Computersystem, das gezielt Angriffe .
- Honey Garlic Chicken Nicky’S Kitchen
- Hörspiel Erstellen App _ Auditorix
- Hörbuch Cd – Hörbuch-SALE: Große Auswahl an Genres online bestellen
- Honorarbescheid Kvb : Informationen zum Thema Job-Sharing
- Holzofen Selber Bauen Bauanleitung
- Honorarkonsulat Pattaya Bescheinigung
- Homeless People In English Hostels
- Holzbank Massiv Garten , Rustikale und Massive Gartenmöbel
- Hörgeräteakustiker Ausbildung Lübeck
- Horse Height Measurements Chart
- Hortensien Pilz Befall | Pilzbefall an Hortensien
- Honda Garantieservice : Kontakt
- Hormonell Bedingte Gynäkomastie
- Home Office Agentur Für Arbeit
- Holzspalter Bauanleitung Pdf – Bedienungsanleitung für Güde Holzspalter