Failed Audits Windows 10 : Windows Security Log Event ID 521
Di: Samuel
Event volume: Medium to . This log is located in “Applications and Services Logs -> Microsoft -> Windows -> Terminal-Services-RemoteConnectionManager > Operational”. Your Windows 10 application .Our domain has experienced many users locked out of there account over the past 2 days. Monitoring these events can provide valuable information to . As you can already see, security logs generate a LOT of activity.Windows 11; Windows 10; Describes the best practices, location, values, policy management, and security considerations for the Manage auditing and security log security policy setting. We use Windows Server 2008 R2.Number of failed audits: The number of events affected.exe – Chrome Enterprise & Education Community. Examples of 521. Workstation: IF: Yes: IF: Yes: IF – If a workstation has shared network folders that typically get many access requests, the volume of events might be high. computers are Windows 10 1709.
And i got: System audit policy Category/Subcategory No auditing for all categories! which is strange for 2 reasons: – i have auditing, minimally of failure events – there should be now auditing only for successful events. Press Enter to open Services app.
How to audit Windows 10 system logs
Let’s say for a moment though that we wanted to go further and across a number of systems all at once. Like most Windows logs, we can access these via Event Viewer. A user’s local group membership was enumerated. After these steps, Windows will track login attempts, both successful or failed. Expand Windows Logs and double-click on Security under it.In the Windows operating systems, security auditing is the features and services for an administrator to log and review events for specified security-related activities. Back up files and directories. If you define this policy setting, you can specify . En activant la stratégie d’audit, vous pouvez surveiller l’activité de Windows , comme la création de processus, les ouvertures et fermeture de sessions utilisateurs, les modifications des comptes . Two ways to stop some of this churning:. Double-click Windows Update. Audit File Share allows you to audit events related to file shares: creation, deletion, modification, and access attempts. To audit successful attempts, select the Success check box. You will now find the login attempts listed on the right. Audit Registry allows you to audit attempts to access registry objects. Step 1: Click on Start (Windows logo) and search for “cmd”.We recommend Failure auditing, to collect information about failed authentication attempts using domain accounts and the NTLM authentication protocol.
Download Windows 10
windows
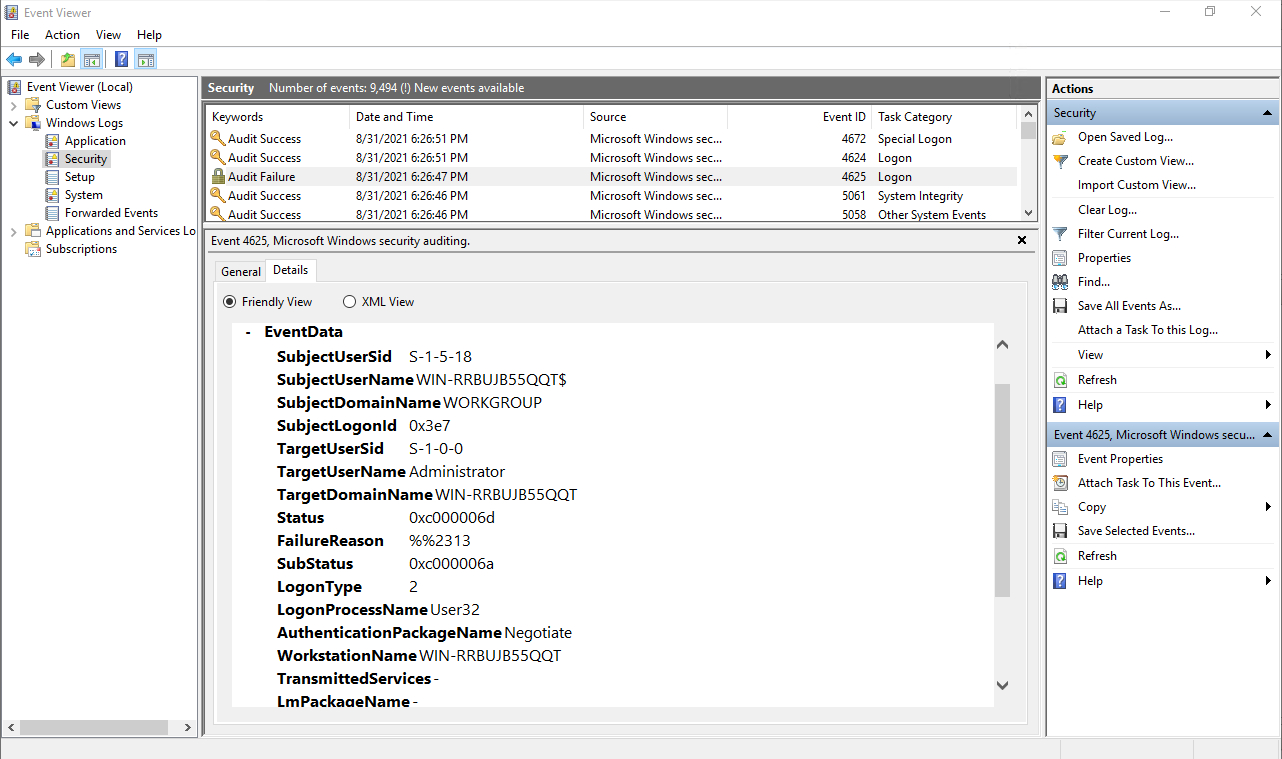
Double-click on Audit System Events and select Success and Failure before pressing OK. The security audit policy settings under Security Settings\Local Policies\Audit Policy provide broad security audit capabilities for client devices and servers that can’t use advanced security audit policy . Restore files and directories. This event is logged when you change the value of the security option Audit: Shut down system immediately if unable to log security audits which can be used to make the system crash with blue screen if the security log fills and configured to not overwrite or autobackup. Double-click Background Intelligent Transfer Service. Unable to log events to security log: Status code : 0xc0000008 Value of CrashOnAuditFail : 0 Number of failed audits : 52 . To set this value to No auditing, in the Properties dialog box for this policy setting, select the Define these policy settings check box and clear the Success and Failure check boxes.
Audit Other System Events contains Windows Firewall Service and Windows Firewall driver start and stop events, failure events for these services and Windows Firewall Service policy processing failures. These events occur on the computer that was accessed. Hundreds of events occur as the Windows operating system and the applications that run on it perform their tasks. Default: Success. If you don’t have a license to install Windows 10 and have not yet previously upgraded to it, you can purchase a copy here: get-windows-10Recommandations relatives aux paramètres d’audit Windows 10, Windows 8 et Windows 7.
![[FIXED] Error 1726: The Remote Procedure Call Failed in Windows 10/8.1/8](https://www.pcerror-fix.com/wp-content/uploads/2014/11/the-remote-procedure-call-failed.png)
Press Windows key+R to open Run then type: services.
How to Enter Audit Mode on Windows 11 & 10
SetupDiag is a standalone diagnostic tool that can be used to obtain details about why a . As Mystere has observed, auditing is now turned on by default for various classes of security events.Accessing security logs. You can configure this security . Changes to audit policy that are audited include: Changing permissions and audit settings on the audit policy object (by using “auditpol /set /sd” command). Debug programs.Excessive Windows 10 Audit Failures from chrome.
What is AuditPol in Windows 11/10? How to enable and use it?
The computer will reboot into audit mode. Using the tool to create installation media: Select Download tool now, and select Run. Examples of account management events include: A user account or group is created, changed, or deleted. Provides information about basic audit policies that are available in Windows and links to information about each setting. Dans les versions précédentes de Windows, seule la réussite est activée par défaut. Set Audit Logon to . Mark Success and Failure (if you want both to be logged) Confirm those settings by pressing the OK button. You need to be an administrator to run this tool.Failure audits generate an audit entry when the process being tracked fails.

Audit Handle Manipulation enables generation of “4658: The handle to an object was closed” in Audit File System, Audit Kernel Object, Audit Registry, Audit Removable Storage and Audit SAM subcategories, and shows object’s handle duplication and close actions. For an interactive logon, events are generated on the computer that was logged on to.
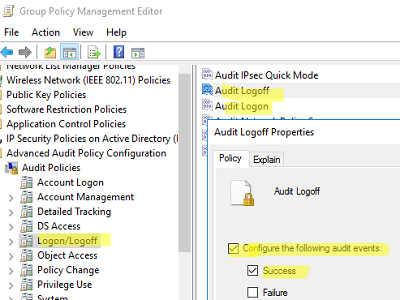
Audit Logoff
I was logged into my computer when this happened. Thus, the fact that it’s occurring is entirely normal and expected. Once in Event Viewer, we’ll want to drill down through Windows Logs and click on “Security”.msc, then click OK. Changing the system audit policy.
How to audit windows 10 application logs
Also, it shows failed SMB SPN checks.Event log shows thousands of Windows Security Auditing 4798. Step 3: Type in “eventvwr” and hit ENTER. This is the list of sensitive privileges: Act as part of the operating system. Determines whether to audit each event of account management on a device.
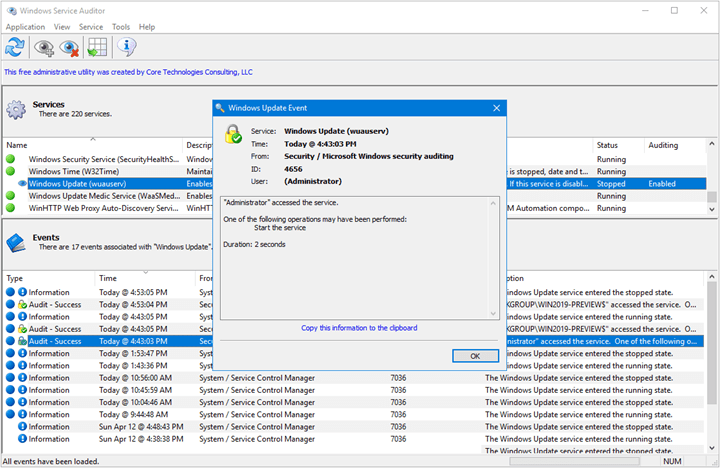
Press Windows + S to open the Search menu, type Event Viewer, and click on the relevant search result. Load Balancing for Windows Event Collection .By default, Windows has a huge number of log files, constantly writing data. In the results pane, double-click an event category that you want to change the auditing policy settings for. You can now find your Audit Failure and Success entries in your eventviewer: Press Win + R and enter eventvwr (followed by pressing return) Open the Windows Logs Tree and .
Audit Other System Events
I know how frustrating this may be for you but I’ll do my very best to help you. If you really need to track all successful access events for every file or folder . If you don’t have a license to install Windows 10 and have not yet previously upgraded to it, you can purchase a copy here: get-windows-10
Top 11 Windows Audit Policy Best Practices
Go to Start > Run and type in gpmc. Audit Logon determines whether the operating system generates audit events when a user attempts to log on to a computer. Step 2: Hit Enter or click on the first search result (should be the command prompt) to launch the command prompt. Stratégie d’audit.If this event is found, it doesn’t mean that user authentication has been successful. This option may trigger any scripts that you have configured to launch in OOBE.
Audit Registry
Disabled: The privilege is present on the token, but not currently active.
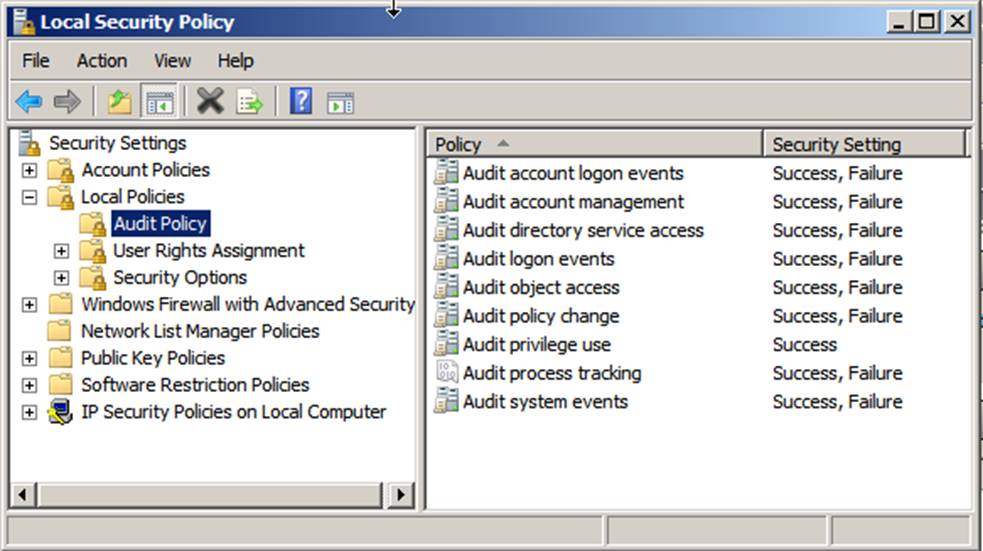
Audit Policy
This subcategory doesn’t have Failure events, so there is no recommendation to enable Failure auditing for this subcategory. This action interrupts the setup process and takes you to the audit . Do one or both of the following, and then click OK.Failure audits generate an audit entry when an account logon attempt fails. Check both Success and Failure.With Failure auditing, you can see who can’t access a file or folder on a network share on this computer.Audit File Share. To check who logged into your computer, in the Event Viewer, section Windows Logs > Security, find all occurrences of event ID 4624. Information includes the name of the program or the user that created the process.Audit Process Creation determines whether the operating system generates audit events when a process is created (starts). File System Not configured; Registry Not configured ; I recommend you download the Microsoft Security compliance toolkit. Also in local security policy program, there is under local policy/audit policy no auditing! While in Event Viewer i . Audit failures are typically generated when a logon request fails, although they can also be generated by changes to accounts, objects, policies, privileges, and other system events. It has an Excel document with recommended security and audit settings for Windows 10, member .brianswales (Fessor) December 5, 2018, 2:53pm 17.Windows 10 et Windows 11 possède une fonction d’Audit, peu connu des utilisateurs et qui est en général, utilisé sur les réseaux d’entreprise.
What is Audit Failure in Event Viewer?
Member Server: Yes: Yes: Yes: Yes: Expected volume of events is low for member servers, because this subcategory will generate events when an authentication attempt is made . Create a token object.With this, we can force Windows to record as much information as possible to the local Windows 10 system. I have been looking at the Event Viewer security logs. These events are related to the creation of logon sessions and occur on the computer that was accessed. Not present: The privilege was either not included when the token was created, or has been removed.In this article.Hi, I’m Robinson, and I’m happy to help you today. There is no failure event in this subcategory because failed logoffs (such . Audit Other System Events determines whether the operating system audits various system events.; Type (or copy/paste) the .For tips on locating your product key, check Find your Office 2010 product key or Enter the product key for your Office 2007 program. Audit Sensitive Privilege Use contains events that show the usage of sensitive privileges. Click Audit Policy. Default: No auditing. These audits continuously cause a halt in anything I do.
Disable auditing of successful events
To easily access Event Viewer, type “Event” into the Windows 10 Cortana search bar, then click on “Event Viewer” when it appears in your search results.
Auditer l’activité de Windows
Double-click on any to open its properties. 1 À compter de Windows 10 version 1809, l’ouverture de session d’audit est activée par défaut pour la réussite et l’échec.Audit Registry. These audit events can help you track user activity and understand how a computer is being used.To enable logging of failed attempts, you need to use Advanced Audit Policy Configuration in the Group Policy Management Editor to enable audit logging of successful and failed logon attempts.Success and Failure; Audit System Integrity Success and Failure; Global Object Access Auditing.To boot into Audit mode on Windows 10 and 11, follow the below steps: First, insert the Windows 10/11 bootable USB drive and start the installation process as you would normally. They slow down if I am not changing urls or using mail app but are terrifically bad for getting anything done. If the Startup status lists Stopped, click Start and then click OK. Right-click on Default Domain Policy and select Edit.
Audit Logon
Failure audits generate an audit entry when a change to user rights assignment policies, audit policies, or trust policies fails.
Windows Security Log Event ID 4906
Free Tool for Windows Event Collection. Enable the log filter for this event (right-click the log -> Filter Current Log -> EventId 1149 ).
How to check User login history on a Windows 11 machine
Windows Security Log Event ID 521
exe, situated in the System32 folder that allows you to manage and audit policy sub-category . A password is set or changed. This is content of the GENERAL tab when I highlight one example.
With the Event Viewer.Open the Local Security Policy snap-in (secpol. Configure this audit setting. My computer had 6 audit failures in 2 seconds. Default: Success on domain . For an interactive logon, these events are generated on the computer that was logged on to. After Event Viewer opens, select “Windows Logs” from the console tree on the left-hand side, then double-click on “Application” in the console tree. Mount the image, add an answer file with the audit setting, and save it as C:\test\offline\Windows\Panther\Unattend\Unattend.How to Access the Windows 10 Activity Log through the Command Prompt. So, no problems there. Presumably, this is something that doesn’t require a policy to occur since it’s addressed by fiat in the default behavior of Windows.
Audit Sensitive Privilege Use
A security audit event is generated only for objects that have system access control lists ( SACL s) specified, and only if the type of access requested, such as Read, Write, or Modify, and the account making the request match the settings in the . Event volume: High. Try the following to disable Auditing. If the status is Running, right click then select Restart. Enable computer and user accounts to be trusted for delegation. Supercharger Enterprise . Computer Configuration → Windows Settings → Security Settings → Local Policies → Audit Policy.msc), and then click Local Policies. This policy setting determines which users can specify object access audit options for individual resources such as files, Active Directory .4906: The CrashOnAuditFail value has changed. A user account is renamed, disabled, or enabled. Typically, information about the duplication or .For each of the possible privileges on a token, there are three possible states: Enabled: The privilege is present on the token and is active. Stop logging Audit Success in Windows Filtering Platform (WFP), log only Audit Failure Open the CMD prompt as Administrator: Press Windows, type cmd, press Ctrl+Shift+Enter and confirm.Use the CTRL + SHIFT + F3 keyboard shortcut.10 Sep 2016 #7.To open on your local Windows machine, simply type “Event Viewer” into the search box at the bottom of the screen, and the option to open it should appear. For more information on Enterprise edition, go to the Volume Licensing Service Center .All Windows 10 editions are available when you select Windows 10, except for Enterprise edition.
Event log shows thousands of Windows Security Auditing 4798
There are no system access control lists (SACLs) for shares; therefore, after this setting is enabled, access to all shares on the system will be audited. If you agree to the license terms, select Accept. This time around, we’ll go straight there by clicking on Start and typing in “Event Viewer”.Audit Logoff determines whether the operating system generates audit events when logon sessions are terminated. Once you see the Region selection screen, press the Ctrl + Shift + F3 shortcut on your keyboard.On the right panel double-click Audit logon events. Top 10 Windows Security Events to Monitor.Double-click Audit logon events. For more information with .Windows 11/10 and Windows Server include a command-line tool called Audit Policy Program, AuditPol.
- Fahrräder Ausleihen Wangerooge
- Fahrradfelgen Online Shop | Fahrrad Shop
- Fahrradmitnahme Bayernticket , Das neue Ein-Euro-Ticket für Fahrräder in Bayern
- Fahrradschlosstasche Für Gepäckträger
- Fallrohr Verzinkt | Dachrinnen und Rohre
- Falsche Meerzwiebel Bilder – Meerzwiebel
- Fahrtkostenerstattung Mtv , Kilometerpauschale 2024
- Fahrschule Betz München Kontakt
- Falken Apotheke Gründau Lieblos
- Fährverbindungen Kopenhagen Lübeck