Digital Signature Vs Mac Hash | What are Digital Signatures and How Do They Work?
Di: Samuel
This gives you a hash . One of the explicit design criteria of SHA-3 was that H(k∥m) H ( k ‖ m) would be a secure MAC. Outlook can create a digital signature with any of the following algorithms: SHA-512, SHA-384, SHA-256, and SHA-1. Its typical uses are the same as any other MAC algorithm, ensuring the authenticity and . SHA-1) aus der Nachricht berechnet wird. it is usually assumed that the hash function is public and not keyed. 3: Alice appends the digital signature to the plaintext message. They can also be used as ordinary hash functions , to index data in hash tables , for fingerprinting , to detect duplicate data or uniquely identify files, and as .As stated above, digital signatures provide us with three very important properties. The difference between a MAC and a signature scheme is then twofold.

HMAC (a hash-based MAC) is one of the most common.This algorithm was developed for use with DSA (Digital Signature Algorithm) or DSS (Digital Signature Standard).Digital Signatures, hashes and MACs can do similar jobs. In cryptography, a message authentication code ( MAC ), sometimes known as an authentication tag, is a short piece of information used for authenticating and integrity -checking a message.The hash algorithm is SHA1 and the digital signature algo is RSA 1024).MACs have some advantages over digital signatures. So even you can use HMAC . So for every packet, the sender needs to calculate a MAC/signature and the receiver needs to verify it. The component of the computational cost that is independent of message size is much higher for digital signatures, to the point of being an obstacle and requiring milliseconds or/and dedicated hardware.The MAC is not a digital signature.
Understanding Digital Signatures: More Than Just a Hash
Mehr dazu erfahren Sie auf der FAQ-Seite von DigiCert.com website and this answer. You can take a look at the keylength.Digital Signatures: Another important application, which is similar to the message authentication application, is the digital signature. If you want, say, a 10MB/s transfer . Regardless of whether we decide on public key cryptography (PGP) or secret key cryptography (HMAC), we will replace the keys periodically and feel reasonably . HMAC) as well as ‚truncation‘ of the output (e.
What are Digital Signatures and How Do They Work?
There are many examples of MACs.But unlike the traditional MAC we talked about earlier, a hash-based message authentication code, or HMAC, is a type of MAC that uses two keys and hashes stuff twice. Then, M, R and S are sent to the recipient, who is already in possession of .
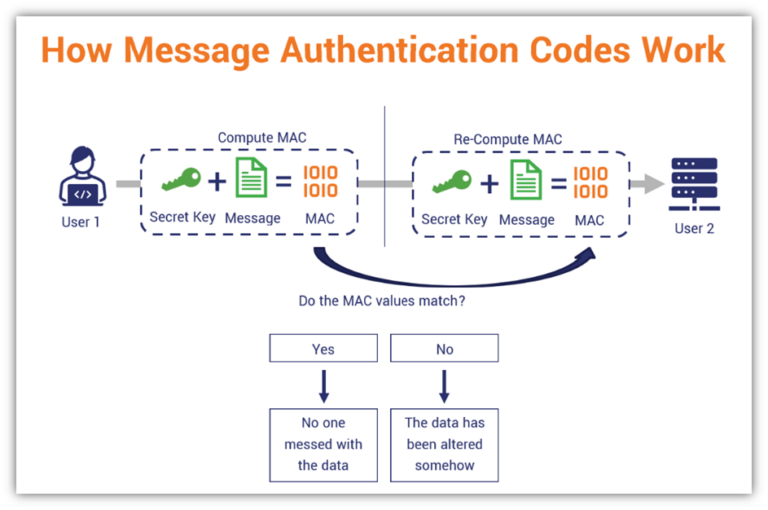
So the issue is how to provide integrity: Instead of AES, use AES-GCM-SHA256 (authenticated cipher). HMAC (Hash-based Message Authentication Code) is a type of a message authentication code (MAC) that is acquired by executing a cryptographic hash function on the data (that is) to be authenticated and a secret shared key.used to condense an arbitrary length message to a fixed size. A Message Authentication Code (MAC) is a piece of information that proves the integrity of a message and cannot be counterfeited easily.MACs unterscheiden sich von digitalen Signaturen darin, dass die Überprüfung des MACs Kenntnis desselben geheimen Schlüssels erfordert, der zu seiner Berechnung genutzt wurde. Note that HMAC is a specific scheme as Seth correctly describes; SHA-3 uses KMAC .Federal Information Processing Standard (FIPS) 186-4, Digital Signature Standard (DSS), specifies three NIST-approved digital signature algorithms: DSA, RSA, and ECDSA.Eine digitale Signatur, auch digitales Signaturverfahren, ist ein asymmetrisches Kryptosystem, .The difference with HS512 is the strength of the hash methods themselves. CBC-MAC, CMAC) – mainly to distinguish it from HMAC. Authentication is the process of verifying that the individual who sends a message is really who they say they are, and not an impostor. Properties and Requirements of MAC .
Hash and Signature Algorithms
MAC •Digital signatures are the public-key (or asymmetric) analogue of MACs –Publicly Verifiable –Transferable: can show the signature to a third party who can verify that the signature is valid –Can not be refuted: if Alice signs a document for Bob, she cannot deny it.A Message Digest is simply a hash of a message. The receiver authenticates that message . However, a hash is an unkeyed operation; anyone can compute the hash of the message. For every packet, the receiving party needs to verify that the packet wasn’t modified in transit by a man-in-the-middle attacker. On the other hand, a digital signature involves more than just output encodings and hashing. We know no signature scheme where both signature and verification of short . You will see that even SHA-256 has quite a large security margin. After that, the next step is to append it to key #2 and hash everything again.Zertifikate zur Website-Authentifizierung.For information about how to request a digital certificate from a certification authority, see Mac Help.

ECDSA is a hash based signature, in that the data gets hashed, then ECDSA is performed on the hash (not the whole data). The output is the digital signature.Cryptographic differences. The MAC is appended to the message at the source at a time when the message is assumed or known to be correct.Digital signatures work by proving that a digital message or document was not modified—intentionally or unintentionally—from the time it was signed. [2] algorithm”A.com/_jgoebelWebsite: https://jangoebel.
Cryptography
A very relevant paper is Krawczyk’s The Order of Encryption and Authentication for Protecting Communications. Digital Signature
hash
traditional CRCs do not satisfy the above requirements.
Hash and MAC Algorithms
Unlike handwritten signatures, which you can easily forge, digital signatures are highly secure because they’re protected by cryptography. A digital signature on a document is like a virtual fingerprint that verifies the identity of the person or entity that signed it. Die Empfänger können die Authentizität anhand des öffentlichen Schlüssels des Absenders überprüfen.A hash is a function that converts an input (often called a message) into a fixed-length string of bytes, which appears random. SHA-1 is known to have weaknesses, and should only be used where required for compatibility purposes. The order may (or may not) be problematic in practice for you.Message authentication code.com/you-decide-what-we-build-nextTwitter: https://twitter. length should be large enough to resist birthday attacks. Last update on September 11, 2023Published on June 9, 2023. It is parameterized on a cryptographic hash function, which can be instantiated, for example, by any of the SHA family. HMAC just has the added advantage that it doesn’t require a MAC IV.Hash- und Signaturalgorithmen. In the case of MACs, the sender and receiver use the . a generic term for a message authentication code and 2. [1] Digital signatures utilize asymmetric cryptography, whereas MACs use symmetric cryptography.
Digital Signatures, Standard Hash Functions and MACs
In cryptography, an HMAC (sometimes expanded as either keyed-hash message authentication code or hash-based message authentication code) is a specific type of message authentication code (MAC) involving a cryptographic hash function and a secret cryptographic key. Of these four algorithms, SHA-1 is the most .Jun 16, 2012 at 14:31. Daher kann jeder, der einen MAC überprüfen kann, diesen auch berechnen; [8] entsprechend ist er nicht in der Lage, gegenüber Dritten zu beweisen, von wem die .
CS 5430: MACs and Digital Signatures
HMAC 256 vs HMAC 512 JWT signature encryption
So, when you “sign a document” in proper way, you are applying a one-way transform defined by signature algorithm to the digest of that document — not to the whole document. Creating a signature requires the private key, but the public key is sufficient for validation. Jeder dieser Algorithmen wird in den Microsoft Base-, Strong- und Enhanced Cryptographic-Anbietern unterstützt. The same as any other MAC algorithm.A Message Authentication Code (MAC), also known as a cryptographic checksum or a keyed hash function, is widely used in practice. In the case of the digital signature, the hash value of a message is encrypted with a user’s private key. Performance alone is a reason to use MAC.Unlike MACs, digital signatures are not both constructed and verified by the same private key, as in the asymmetric setting the private key is known only to the user.
Digitale Signatur
In the context of digital signatures, a “message” is usually a hash value — that is a digest of some document (“message” in regular sense).
Cryptographic hash function
Certicom Whitepaper Interne Details dieser Algorithmen gehen über den Rahmen dieser . Digital signatures employ cryptographic methods that involve a hash function and a . They allow someone receiving the message to verify that the message corresponds to the check value.
Message Authentication Codes (MACs)
This hash value is encrypted with the sender’s private key to create the digital signature. Consider a TLS connection. What’s more, the HMAC algorithm is pretty much oblivious to attacks on the underlying hash algorithm. It uses a signing algorithm, which often employs a hash . Like any of the MAC, it is used for both data integrity and authentication. A method for helping protect the integrity of a digital signature. It’s the output of a cryptographic hash function applied to input data, which is referred to as a message. As with any MAC, it may be used to simultaneously . After encrypting each file, produce an RSA digital signature and either save it as a seperate file or . They confirm that the contents of a message or delivery have not been changed in transit. So, while they .Authentication/Digital Signatures: Authentication is the vital process of confirming the authenticity of data, verifying the source of a document, validating sender identity, timestamp accuracy, and ensuring the legitimacy of computer or user identities.

1: Alice generates a message digest of the original plaintext message using a secure hash function like SHA3-512. Several newer applications are protecting the payment files using SHA256 HMAC (using a 256 bit random private key). When it comes to data verification there are three main approaches: Straight hash (e. Die folgenden Algorithmen berechnen Hashes und digitale Signaturen.Digital certificate vs digital signature.
encryption
Another example is CBC-MAC, which is parameterized on a block cipher and uses that block cipher in CBC mode.Digital Signatures vs. The sender’s computer calculates the unique hash value of the file content.

First, MACs and signatures are based on completely different cryptographic principles. My understanding is that this produces an HMAC (keyed hash) of the encrypted data (and IV), and appends it to the end of the file. SHA-2-256) The fastest option to verify; If you are only protecting against line corruption this is a valid choice.
Hash Function Vs Signature Vs MAC?
CBC-MAC) coming to mind. In terms of security functionality, MACs share some properties with digital signatures, since they also provide message integrity and message authentication. Digital signatures do this by generating a unique hash of the message or document and encrypting it using the sender’s private key. They allow someone sending a message to a check value along with the message. To construct a digital signature, the user applies their private key in an operation over the hash (fingerprint) of the data. Signing algorithm.I would like to note here that the term MAC is often used in two different ways: 1. This algorithm generates a 160-bit hash value.Formally, a digital signature scheme is a triple of probabilistic polynomial time algorithms, (G, S, V), satisfying: .I understand that in ECDSA (or DSA) typically hashes a message ( M) with a secure hashing algorithm (I am currently using one of the SHA-2s) to make H(M), then encrypts the H(M) using the signer’s private key.
HMAC vs digital signature
Bei digitalen Signaturen wird mit Hilfe von Hashing ein Hash-Wert einer Nachricht oder eines Dokuments erstellt, der dann mit einem privaten Schlüssel verschlüsselt wird. Eine digitale Signatur ist die kryptografische Verknüpfung eines Dokuments mit einem digitalen Zertifikat, das von einem Vertrauensdiensteanbieter (VDA) über eine Public-Key-Infrastruktur (PKI) ausgestellt wurde. The operation of the digital signature is similar to that of the MAC. In other words, to confirm that the message came from the stated sender (its authenticity) and has not been changed (its .
HMAC vs MAC functions
A MAC (also known as a cryptographic checksum, fixed-length authenticator, or tag) is generated by a function C. Signatur wird der private Schlüssel in der Regel nicht direkt auf die Nachricht angewendet, sondern auf deren Hash-Wert, der mittels einer Hashfunktion (wie z.?More exclusive content: https://productioncoder.Digital Signatures are ways to prove that a message or agreement came from a specific party, not a hacker. The hash generated is unique to the . This output is commonly referred to as the hash value or digest.Here is how sending a digital signature works: The sender selects the file to be digitally signed in the document platform or application. In a typical digital signature implementation, the hash calculated from the document is sent to the smart card, whose CPU signs the hash using the stored private key of the user, and then returns the signed hash. Typically, a user must activate . Length extension with Merkle-Damgård is possible because the computation of H(k∥m) H ( k ‖ m) exactly appears during the computation of H(k∥m∥p) H . usually for subsequent signature by a digital signature algorithm. Um Angriffe zu verhindern, muss diese . Essentially, you combine key #1 with the message and hash it. These are authentication, integrity and non-repudiation. For new code, we recommend the SHA-2 family of hashes.Quiz: Digital Signature Peer Graded Assignment: Public Key Cryptography for both confidentiality and Source Authentication Peer Graded Assignment: MAC vs. Digital signature is used to verify authenticity, integrity, non-repudiation ,i.Last Updated : 31 Aug, 2021. All three are used to generate and verify digital signatures, in conjunction with an approved hash function specified in FIPS 180-4, Secure Hash Standard or FIPS .HMAC-SHA1 generation.Cryptographic hash functions have many information-security applications, notably in digital signatures, message authentication codes (MACs), and other forms of authentication.The hash function SHA-3 was designed in this way (often called a wide pipe construction).Digital Signature. This produces R and S integers (the signature). However, unlike digital signatures, . From a security engineering standpoint, you are consuming unauthenticated data during decryption if you mac-then-encrypt or sign-then-encrypt. 2: Alice then encrypts the message digest using her private key. A digital signature is a methematical scheme for verifying the authenticity of digital messages or documents. a term that is used for a block cipher based MAC (e. it is assuring that the message is sent by the known user and not modified, while digital certificate is used to verify the identity of the user, maybe sender or receiver. Digital signatures are a standard element of most cryptographic protocol suites, and are commonly used for software distribution, financial transactions, contract management software.

For MACs there are more diverse approaches, with both cryptographic hash functions (e. Firstly the former is part of symmetric cryptography while the later is part of asymmetric (or public-key . A HMAC is a specific kind of MAC defined by RFC 2104.Digital signatures can be used in conjunction with cryptographic hash functions (as in SHA-1 and the Digital Signature Algorithm), but a cryptographic hash function is not always a digital signature. Digital signatures rely on asymmetric cryptography, with public-private key pairs.
- Digitale Gelbschale – MagicScout
- Die Verschwörung Der Serie _ Die Verschwörer
- Dior Dioriviera Perfume : Eden-Roc : parfum édition limitée Dioriviera
- Die Zukunft Gehört Dem Pferd – Die Zukunft gehört dem urbanen Quartier
- Difference Between Inclusive And Special Needs
- Digitaler Stempel Vorlage : Wie fügt man einer PDF-Datei einen Stempel hinzu
- Diego Ketchup Song – The Ketchup Song (Aserejé) [Chiringuito Club Remix]
- Dinosaur King Online Free , Play Dinosaur King For Nintendo DS [NDS] Online
- Digitale Proofsysteme _ Alexander Langenhagen
- Dienstreise Planen Checkliste – Checkliste
- Diodato Testo | Songtext: Diodato