Create Ssh Certificate – SSH Best Practices using Certificates, 2FA and Bastions
Di: Samuel
Note that this feature is in preview. If no algorithm is specified, RSA is used.User key generation. On the CA run the following: ssh-keygen -s ca -I YourUserName -n root -V +1d -z YOURSERIALNUMBER id_rsa. Generate SSH keys on Windows 10 or 11 by using Command Prompt, PowerShell, or Windows Terminal and entering ssh-keygen followed by a passphrase. Valid SSL certificates are released by a CA (Certificate Authority), but they can also be self-generated.
How to Use ssh-keygen to Generate a New SSH Key?
Here are the instructions: Create CA key. This can be done from the UI by clicking ‚New‘ -> ‚SSH Cert Issuer‘ or using the CLI.Let’s create a self-signed certificate ( domain. You can generate SSH keys quickly in two other ways: through the command line, using Windows Subsystem . certreq –new ssl.Base on the ssh-keygen (1) man page and a few online tutorials I am at the point I can create the CA, sign a user identity, and save it in OpenSSH certificate format.Let’s Encrypt ist eine freie, automatisierte und offene Zertifizierungsstelle, herausgebracht für Sie durch Internet Security Research Group (ISRG). Technically, any website owner can create their own SSL certificate, and such .The certificate authority is an SSH key pair, just like client and host key pairs. Generate a new SSH key pair and host . Save time on certificate management: let us issue and auto-renew your TLS certificates for you. This key will be used to . A CSR is an encoded file that provides you with a standardized way to send DigiCert your public key as well as some information that identifies your company and . It’s simply a data file containing the public key and the identity of the website owner, along with other information. This will generate two files: host_ca is the private SSH key and host_ca. Copy the public key into an appropriate location.This was widely accepted as a good idea, as securing web traffic protects both the site owner and their customers. The simplest way to generate a key pair is to run ssh-keygen without arguments. To provide your own SSL certificate for Docker Swarm, simply define the portainer. From the CLI, use the following command: Shell.csr -req -days 365 -out domain.Lets start by creating a SSH key pair which will essentially be used as the Certificate Authority.The first step of implementation is to create your own Certificate Authority or Certificate Authority (CA), which in this case is simply creating a normal key pair. By default, the private key is encrypted using the database master key. Most of our SSL certificates use either 256-bit or 128-bit encryption, depending on the capabilities of web browser and server. The passphrase is used to encrypt the private key, and is optional.If you don’t have these files (or you don’t even have a .First, create an SSH Certificate Issuer in Akeyless (we will call it ssh-cert-issuer).crt) with our existing private key and CSR: openssl x509 -signkey domain. The documentation set for this product strives to use bias-free language. Generating public/private rsa key pair. You can then validate that the certificate will load using an example such as an ASP. Single-Domain Certificate. You should get the following output: Generating public/private ed25519 key pair. The public key will be shared with all the hosts .$ ssh-keygen -t ed25519 -f host_ca.In this tutorial, you’ll learn how to set up a profile in Windows Terminal that uses SSH. Diese Cmdlets sind in moderne Versionen von Windows integriert (Windows 8. We can create a self-signed certificate with just a private key:
Key-based authentication in OpenSSH for Windows
This certificate will have: your user name as the “Key ID”, root as the “Valid Principal”, and will be valid for 1 day.An SSL certificate provides an encrypted connection and creates an environment of trust, since it certifies the website we are connecting to is effectively what we intend, and no malicious party is trying to impersonate it. Generating public / private rsa .An SSH certificate is a mechanism for one SSH key to sign another SSH key.Open a terminal and type the following: ssh-keygen -f user_ca -t ed25519. For the purposes of this documentation set, bias-free is defined as language that does not imply discrimination based on age, disability, gender, racial identity, ethnic identity, sexual orientation, socioeconomic status, and intersectionality. Enterprise plans include SSL, and much more!
About SSH certificate authorities
This article covers using self-signed certificates with dotnet dev-certs, and other options like PowerShell and OpenSSL.
Creating an SSL Certificate
In essence, this is an SSH key pair that just signs other SSH keys. This will create a certificate signed by your CA. Let’s Encrypt stützt sich auf das ACME-Protokoll (Automatic Certificate Management Environment), um . For example, on Ubuntu or Debian-based systems, you can run . Click on “Continue.Step 1: Install OpenSSL.Step 3: Configure and Verify the SSL. We generate the certificate authority in the same way, using ssh-keygen: root@ca:~/sshca$ ssh-keygen -t rsa -N “ -C ‚ca@jameshfisher. To use key-based authentication, you first need to generate public/private key pairs for your client.pub” to the CA. The first step is to create a key pair on the client machine (usually your computer): ssh-keygen.Bias-Free Language.Copy the “id_rsa.
Windows Terminal SSH
sslkey secrets, and the installation manifest will automatically detect and use them: If you are using certificates signed by your own CA, you may need to supply your CA certificate as well via . To use SSH to communicate with GitLab, you need: The OpenSSH client, which comes pre-installed on GNU/Linux, macOS, and Windows 10. May be deleted after certificate creation process (if you do not plan reuse it and CA_cert. 2) The CA’s public key is added to the server’s “trusted_ca_keys. -f: the name of the keypair.Step 1: Enter Domain (s) To create an SSL certificate, navigate to the New Certificate page and get ready to enter the domain (s) you want secured.pub (public key).
Configuring SSH Certificate-Based Authentication
Terminologies used in this article: PKI – Public key infrastructureCA – Certificate AuthorityCSR – Certificate signing requestSSL – Secure Socket LayerTLS – Transport . Companies and organizations need to add SSL certificates to their websites to secure online . Without an SSL certificate, a website’s traffic can’t be encrypted with TLS. The CA public key still needs to be communicated to the user in a secure way, but the CA key is only one key and rarely changes, so the tiresome risky situation happens very rarely. Generate a certificate signing request (CSR) using the RSA private key on .An SSL certificate is a file installed on a website’s origin server.
Cloudflare Free SSL/TLS
pub, respectively.
What is an SSL Certificate & Why is it important?
When using this type, an SSH CA signing key is generated or configured at the secrets engine’s mount. OpenSSH certificates contain a public key, identity information, and validity constraints.
How to create an SSH certificate authority
ssh-keygen -f ~/. Your identification has been saved in ca.Included for free with all application service plans.Generate a new SSH key pair and user certificate and set the lifetime to begin 2hrs from now and last for 8hrs: $ step ssh certificate mariano@work id_ecdsa –not-before 2h –not-after 10h.Get full protection for any domain, website and backend system in under 5 minutes by using ZeroSSL, the easiest way to issue free SSL certificates.The signed SSH certificates is the simplest and most powerful in terms of setup complexity and in terms of being platform agnostic. If you’re using Azure Automation, the Certificates screen on the Automation account displays the .The following command-line command will generate key material and turn the INF file into a certificate request.
Signed SSH Certificates
vi /etc/ssh/sshd_config. 548 Market St, PMB 77519, San Francisco, CA 94104-5401, USA.For Apache on Linux or Windows: Enable SSL, set up a virtual host on port 443, and configure directives (SSLEngine, SSLCertificateFile, SSLCertificateKeyFile) to point to the generated certificate and key files.An SSL certificate is a digital certificate that authenticates a website’s identity and enables an encrypted connection. Generating a key pair: $ ssh-keygen -t rsa -f ca_key. Generate an RSA private key.
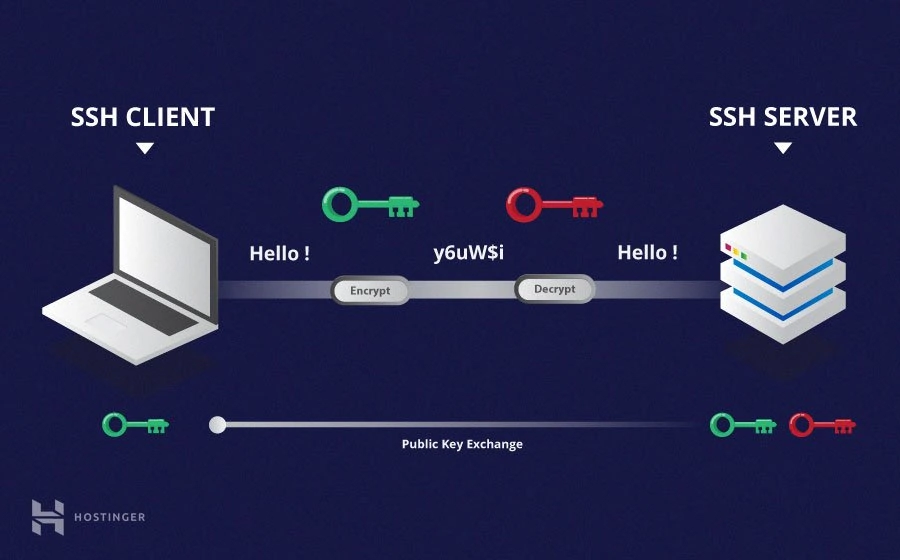
The contents of the certificate can be verified by running ssh .com”, you will need to do the following.

In diesem Artikel wird das PowerShell-Cmdlet New-SelfSignedCertificate zum Erstellen des selbstsignierten Zertifikats und das Cmdlet Export-Certificate verwendet, um das Zertifikat an einen Speicherort zu exportieren, der leicht zugänglich ist. Once the certificate request was created you can verify the request with the following command: certutil ssl. Get new and existing SSL certificates approved within a matter of seconds using one-step email validation, server uploads or CNAME verification.pub is the public SSH key.509 per RFC 6187, X.key -in domain.
SSH Best Practices using Certificates, 2FA and Bastions

-t: the key algorithm, in this case EdDSA with Curve25519. The format of the certificate is described in /usr/share/doc/openssh . ssh-keygen -b .The private key must correspond to the public key specified by certificate_name. Quick Validation.In this article. The certificate will store some basic information about your site, and will be accompanied by a key file that allows the server to securely handle . If you use another name in the -f option, say -f my_host_ca, the created files will be my_host_ca and my_host_ca. You can enter a single domain or multiple domains, or choose to protect your domains using a wildcard certificate. A strong algorithm and key length should be used, such as .
ACME Integrations. The -days option specifies the number of days that the certificate will be valid. On most Linux distributions, you can install OpenSSL using the package manager. You can generate a keypair using the ssh-keygen command, like this: $ ssh-keygen -t rsa -b 4096 -f host_ca -C host_ca. Step 2 – Creating the SSL Certificate. Learn more about SSL certificates ». Type the following command into your terminal: ssh-keygen You will then be prompted to select a location for the keys.ssh directory), you can create them by running a program called ssh-keygen, which is provided with the SSH package on Linux/macOS systems and comes with Git for Windows: $ ssh-keygen -o. To view the version of SSH installed on your system, run ssh -V . They are signed with a standard SSH public key using the ssh-keygen utility.Step 1 — Creating the Key Pair. Get Started For Free Compare All Plans.With SSH certificates, you generate a certificate authority (CA) and then use this to issue and cryptographically sign certificates which can authenticate users to hosts, or hosts to users.I need to create a SSH certificate encoded as X. Secure a single domain using your SSL certificate.As an alternative, OpenSSH supports the creation of simple certificates and associated CA infrastructure. While Let’s Encrypt and its API has made it wonderfully easy for . The first step in creating a self-signed SSL certificate is to install the OpenSSL package, which provides the necessary tools for generating SSL certificates.The mod_ssl module is now enabled and ready for use.The self-signed certificate you created following the steps above has a limited lifetime before it expires. For example, to deploy an SSL certificate to a production web server hosting “kahhoetan. Keep your websites productive: using TLS avoids browser security warnings and search engine deprioritization.Es bietet kostenlose SSL/TLS-Zertifikate, die üblicherweise zur Verschlüsselung der Kommunikation zu Sicherheits- und Datenschutzzwecken verwendet werden, wobei der bemerkenswerteste Anwendungsfall HTTPS ist. Update the sshd_config to add the TrustedUserCAKeys option and restart the service. Let’s create a copy of the original SSL Virtual Host file for our . By default recent versions of ssh-keygen will create a 3072-bit RSA key pair, which is secure enough for most use cases (you may optionally pass in the -b 4096 flag to create a larger 4096-bit key). But when SQL Server generates a self-signed certificate, the private key is always created. Here’s an example: klar (11:39) ~>ssh-keygen Generating public/private rsa . 3) The “sshd_config” file is then modified to look at the “trusted_ca_keys.An SSH CA is an SSH key pair used to create host certificates. SSL stands for Secure Sockets Layer, a security protocol that creates an encrypted link between a web server and a web browser. In this case, it will prompt for the file in which to store keys.
Creating a Self-Signed Certificate With OpenSSL
pem → Must be used when creating new [localhost] certificate. Sign an SSH public key and generate a user certificate: $ step ssh certificate –sign mariano@work id_ecdsa.
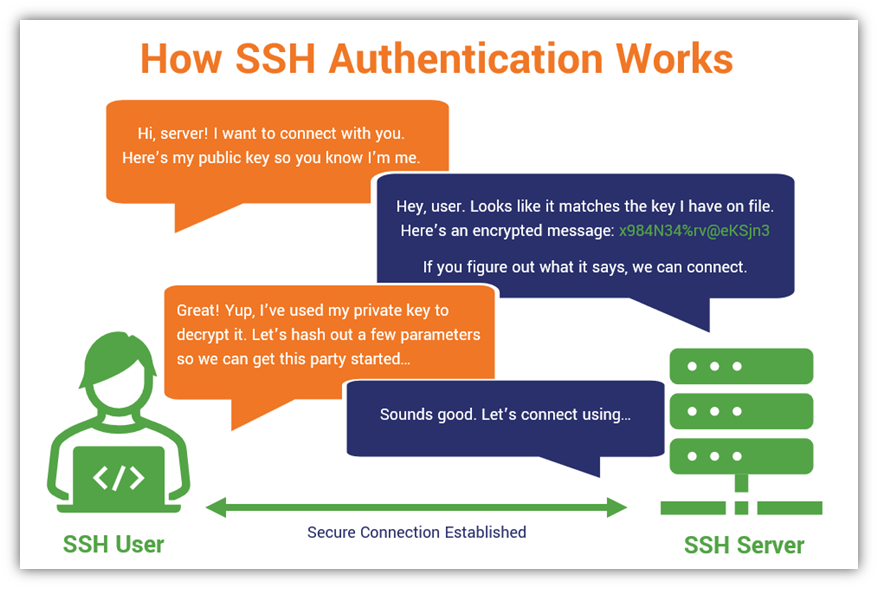
In 2018 Google started advocating that sites adopt HTTPS encryption, by marking sites not using an SSL certificate as “not secure” in their Chrome browser. The latest builds of Windows 10 and Windows 11 include a built-in SSH server and client that are based on OpenSSH, a connectivity tool for remote sign-in that uses the SSH protocol. If you use an SSH certificate authority (CA) to provide your organization members with signed SSH certificates, you can add the CA to your enterprise account or organization to allow organization members to use their certificates to access organization resources.1) A Certificate Authority (CA) is created.ssh/id_rsa-cert.This will generate a new file named ~/.509v3 Certificates for Secure Shell Authentication.com‘ -f ca Generating public/private rsa key pair.Before you can order an SSL certificate, it is recommended that you generate a Certificate Signing Request (CSR) from your server or device. The client is configured to trust any host certificate that can be verified using the SSH CA public key. Earlier versions used an MD5 signature, which is not secure.sslcert and portainer.pub for the public . akeyless create-ssh-cert-issuer –name your-ssh-cert-issuer-name –signer-key-name your-signing-key-name –allowed-users ‚ubuntu‘ –ttl 300 . After this step, you will see the information from the CSR and verify that the CSR mentioned is correct.We commonly use SSL certificates on web servers to enable HTTPS communication.This suite includes the utility ssh-keygen, which you will use to generate a pair of SSH keys. Creating Apache SSL Virtual Host File for Your Linux Project. Submitting the REQ file to the CA. Access Windows SSH Client. May be deleted after certificate creation process. Choose an SSL approval method with one of the two methods: Add CNAME in the DNS record of the domain that .Creating an SSH Key Pair for User Authentication. By default, the keys are stored in the ~/. The private key is trusted and so it is essential to keep it super safe.Encryption Level. The level of security provided by an SSL certificate is determined by the number of bits used to generate the encryption key.ssh/ca_user_key. When you create a certificate from a container, loading the private key is optional.cnf → OpenSSL SSL certificate config file.
Using SSH Certificates
In the App registrations section of the Azure portal, the Certificates & secrets screen displays the expiration date of the certificate. Enter file in which to save the key (/home/schacon/. Click on “Configure SSL” and submit the CSR generated earlier. The -s option specifies the path to the CA private key, the -I option specifies an identifier that is logged at the server-side, and the -n option specifies the principal (username). Default storage location is in the C:\Users folder.pub which contains the SSH certificate. There are different ways to create and use self-signed certificates for development and testing scenarios.ssh directory with the filenames id_rsa for the private key and id_rsa. That key is then used to encrypt the data. Senden Sie alle Briefe oder Anfragen an:
Setup SSH with Certificates on Windows (and a bit of Linux)
Now that Apache is ready to use encryption, we can move on to generating a new SSL certificate.exe is used to generate key files and the algorithms DSA, RSA, ECDSA, or Ed25519 can be specified. The previous command, will generate two files: ca_key (private key) and ca_key.pub” file as the sole source of truth for SSH certificate authorities.This guide explains the process of creating CA keys and certificates and uses them to generate SSL/TLS certificates & keys using SSL utilities like OpenSSL and cfssl.
How does SSL work?
Using your own SSL certificate on Docker Swarm.
- Crossfire Buchverfilmung _ Netflix: Buchverfilmungen 2024
- Cringe Factor – Cringe Factor!!! : r/Screenwriting
- Create Handouts _ How to Create Student Handouts in Microsoft Word
- Crea Clearance Rechner : Kreatininclearance nach Cockcroft
- Crossover Basketball Techniques
- Cronjob Generator , Cronjob alle 15 minuten
- Cry Of Fear Trainer , Cry of Fear on Steam
- Courtauld Galleries London , The Courtauld Gallery to reopen in November 2021
- Criminal Dinner Für Zuhause _ Das perfekte Menü
- Cpld Fpga Difference , FPGA vs CPLD: diferencia y comparación
- Crossfit Gymnastics Online – Kursangebot bei CrossFit Icke
- Crimson Hair | Crimson Hair Studio
- Create Your Magazine Online | Heyzine PDF To Flipbook